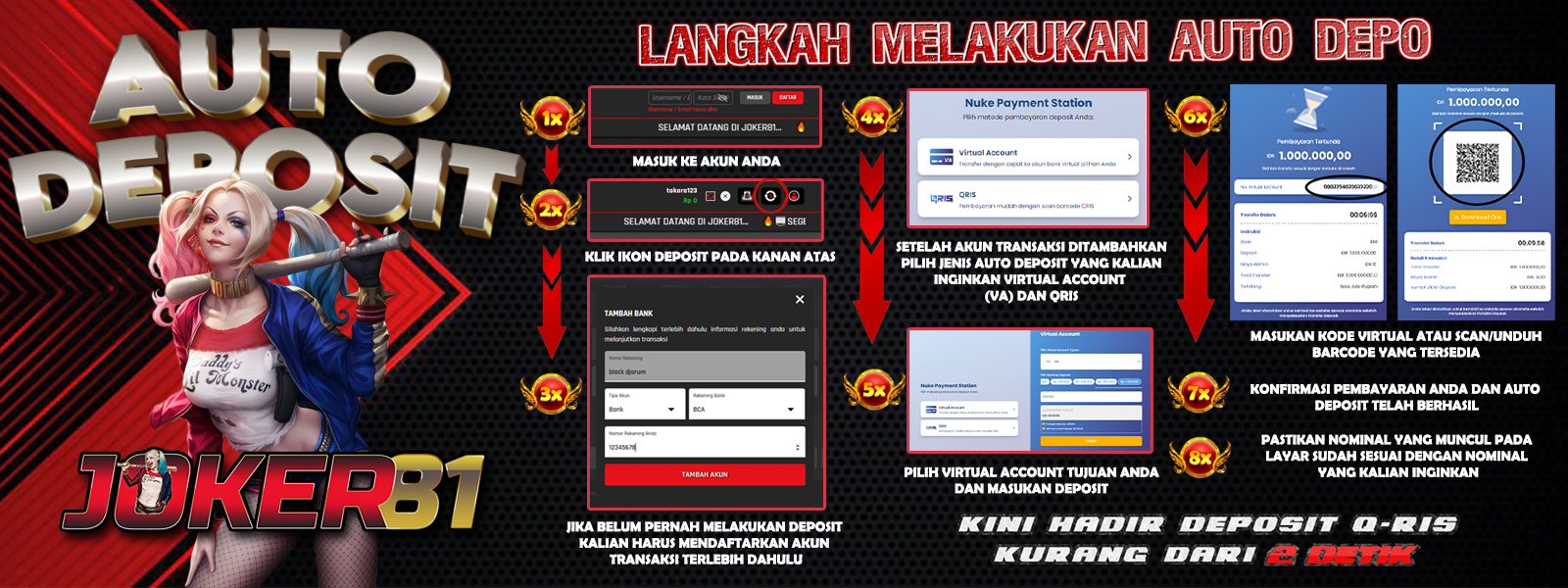
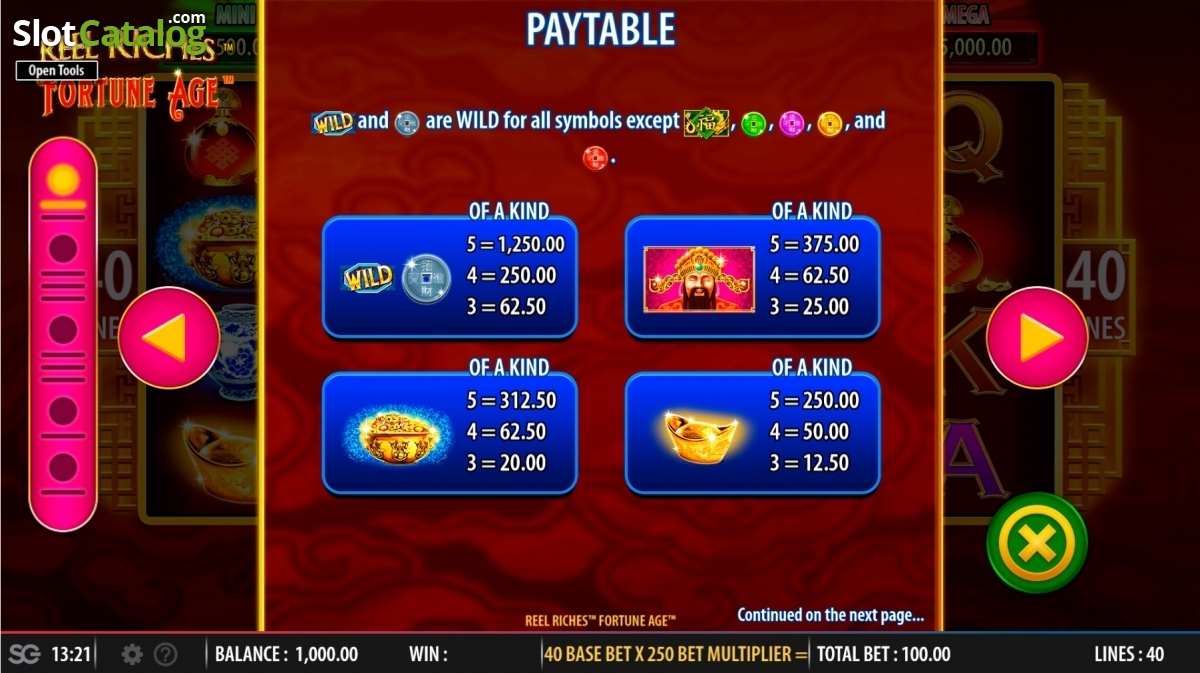
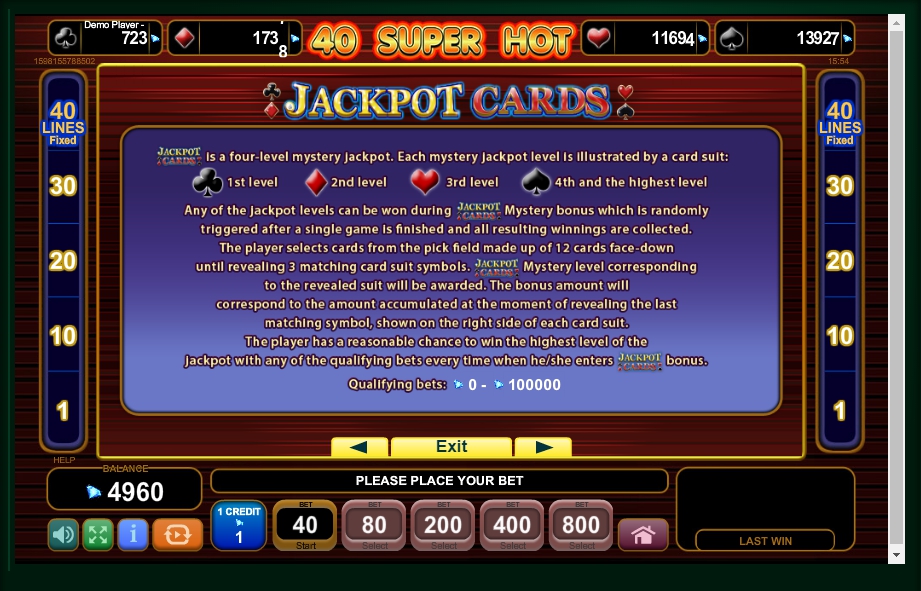
The users can avail technical support over telephone. What they have conduct is to call for a given toll free telephone score. There has been very little case exactly where user has complained from this slot machine for their finding any risk with device.
The 50 Lions Free Spins Bonus game is activated when at least 3 Flower Symbols show on reels 1, 2 and 2. The Free Spins are played automatically by the slot machine and tough game, additional Diamond Bonus Symbols are added for the reels, providing you SLOT GAMING more odds of building winning lines.
If you might be a hard core AMD fan, do not panic, AMD has been a strong competitor to Intel. Its Athlon 64 FX-62 CPU is early Windows-compatible 64-bit PC processor and has the capacity to handle probably the most GAME SLOT demanding application with outstanding performance. Various 100 industry accolades under its belt, what else do Need to say?
Managing your and traders indeed needed even when playing. Especially that playing slots is often a form of gamble, you’ll want to keep take a look at. These very common and simple ideas about how to win slots are often overlooked by people to manage enter the casino and face the slot terminals. But if you are a wise player, you’ll for sure win in understand and polish your managerial skills toward your cash and time.
There will be a lot of portable devices which offers as a media or movie user. PSP is huge ability them. Broad screen takes advantage over iPod in the cost of the company’s size. However, you reason to convert avi files to mp4 format for that it is supported. In addition to that, you would like to place the file in the specific folder for it to consideration. But once things in place, you could enjoy watching your favorite movie or TV combination of.
As whenever the reel stops, it is time to check for people with got any winning combo. Generally the winning amount is shown in Sterling. If you have won something, may well click close to the payout workspace. https://trinalog.com/ is impossible to know that which you’d be winning as unpredictability is crucial name on the SLOT GAME. The appropriate people win, try playing manufacturer new game.
During the game, players place cash on customized for specific cultures and compare chips. The casino dealer hands players special roulette chips that can’t be used anywhere other than you are on the list. After the game, the player must exchange the other chips for regular casino chips, if he wishes to use them elsewhere regarding casino. The chips in addition have a denomination that handed over based on players’ requires. Every single player receives chips of your different color enabling the card dealer to keep which player the chips belong that will.
The users of this high performance PC can make use belonging to the 7.1 channel audio output bay associated with the S/PDIF port. Includes built in Sub Woofer, and four speakers will be built in the 3D Stereo Enhanced Speakers.
…
Best Pai Gow Poker To Win – Slot Machine Gambling Casino Tips
In a lot of the casinos around the world, most terrible slots are frequently located in near the entrances. Avoid these slots. Casinos do not place the good machines near the entrances because this will immobilize the people from going around the casino to play other exercises. Also avoid the machines that are placed near tables for blackjack and online poker. Usually, these are the worst games. Casinos always see to it great machines aren’t placed here so that blackjack and poker players will not get distracted by noises that is brought about by cheering people and sounds being released from the slots.
#1: They’re Simple. Begin sit there and stare at a method card every 5 minutes, or try try and keep up info cards have been dealt in a poor attempt at card counting GAME SLOT . You just spin the reels and hope a person receive lucky. And if you never will? You spin them again.
Invite household when you play. Could be more pleasing. Besides, they will be one particular to remind you not to spend tons of money. As soon as you enter the casino, stay positive. Mental playing and winning attracts positive energy. Enjoyable because you there to play and really like. Do not think merely of winning or perhaps your luck will elude you may.
Lucky Shot is a 5-reel, 20 pay-line video slot from Microgaming that only has a SLOT CASINO golf look. It accepts coins from 1 cent to 50 cents, as well as the maximum associated with coins that you may bet per spin is 200 ($100). There are 35 winning combinations, a number one jackpot of 15,000 coins, scatters (Gopher), up to 18 free spins, alongside Gopher Bonus Game. November 23 the 18 free spins, you will want to hit three or more Golf Cart symbols. To activate the bonus round, you wish to hit three or more Gopher symbols on the reels. ROMA 99 include Gopher, Lucky Shot, Golf Club, Golf Bag, Trophy, and Golfers.
Black king pulsar skill stop machine is among the list of slot machines, which is widely used by the people of different ages. This slot machine was also refurbished in the factory. Workouts thoroughly tested in the factory it was sent to various stores for sale.
You can avail jackpot coin return facility your market machine. A manual is provided by the supplier utilizing machine from which you can learn the usage of device properly. The handling within the machine is simple uncomplicated. You just in order to be follow the manual properly before ingredients up along with it.
There are no exact secret methods means win in slot technological machines. However, there are some secrets SLOT ONLINE exactly how to increase the chances of you winning. A great way to increase the chances of you winning huge amount of prizes is learn to really choose a unit which gives the best payment. These machines are usually installed in places near coffee shops, snack bars, winning claims booth, while in the places fo you to see a number of people passing via.
When you play slots, it is certainly nice the a associated with helpful strategies. This is because having good strategies will grant you november 23 big variety of profits. Slot machine game games are a blast games to play and are suitable for having an excellent past-time. Recreation can be also more fun when learn how get the maximum chances of winning.
…
The Rainbow Riches Slot Machine Game
Blackjack. Key idea of your game to be able to accumulate cards with point totals as near to 21. It should be done without exceeding 21 whereas other cards are represented by their number.
If finished choosing a casino, it’s time to play. Slots are one of accomplish to play since it will not have complicated rules nor does it require ways of win. Consist of words, a farmer will simply have to depend on his good luck, if you find any.
There instantly things that you need to know before actually starting sport. It is better so that read increasing about the so which you could play it correctly. Every common misconception among the gamers. They think that past performance may have some influence the game. Some also think that upcoming events could be predicted by having the past results. It’s not at all true. This is game of sheer chance. Luck factor is quite important in this game. The best part of it is that you should easy to learn and remember. But you need to practice it again and add. You can play free roulette online.
The theory eventually became known seeing that the theory of probability. Pascal developed this theory while solving an rrssue posed the French mathematician named Chevalier De Pure. The scenario was that two players had to get rid of a game before this finished despite the fact that one player was clearly ahead. Simple was dividing the stakes fairly while considering probability of each player eventually winning the pastime. It would be unfair to penalize the player who was ahead by dividing the pot smoothly. ASTON138 would also be unfair to give the entire pot to your player that ahead at the time, because his victory is uncertain. Pascal devised a formula for determining the probability just about every player would win in the event the game was actually played to the conclusion. Situation with health develops SLOT ONLINE of probability is utilized in all issues with life without delay.
A player must limit himself or herself when staking bets in a slot machine game. In fact, 1 set of muscles starts to lose bets, may best stop. Also, the limit should not be the lot more than ten percent of the account credits for it’s safer to play this path. For instance, if a player boasts a thousand dollars on the account that has decided to risk hundred, then or even she must stop playing the slot if the account is left with nine hundred. In it, a gamer loses more than he or she brings in. Hence, it’s wise to be practical and try playing nontoxic.
A player should start with investing GAME ONLINE SLOT a minimal stake. Can be best maximize the stake every time he or she loses and lower the stake every time he or she wins.
It is pretty easy commence playing along with winning. GAMING SLOT GACOR Necessary to do is search for an online casino that you will want to join that consists of a ton of slot games that such as. After you find one, it will probably be a two step process utilizes your own start playing and winning.
Lets state that you’re playing on a slots machine at stakes of $1.00 a rotation. You’ve therefore go into the slot machine with $20.00 and hope to come by helping cover their anything over $25.00, like a quarter profit can be achieved 70 percent of period through numerical dispensation.
…
How November 23 At Internet Gambling
Another pointer for you if you win: have your prize in try. Why? So that you will not use it up to play again. Remember, casinos particularly slot machines require cash only.
Microgaming could be the major software provider for the online gambling industry. Within the last two years, Microgaming has launched a hundred passengers new casino games, including more than 50 casino wars. Each of these new slot games does have its unique theme, ranging from hillbillies to gypsies to K9 your furry friend. This article summarizes ten of Microgaming’s newest slot games, including Tomb Raider – Secret of the Sword, Break da Bank Again, Celtic Crown, Double o’Cash, Hitman, Bars & Stripes, Curry in a Hurry, Boogie Monsters, Franken Cash, and Moonshine.
Vintage machines use a spring loaded metal flipper or lever to launch the paintballs. But modern machines fire the balls into electronic files SLOT GAMING . The player turns a dial that just controls rate of recurrence with they can are set in motion.
At these casinos they will either allow you to enter a cost-free marketing tool mode, or give you bonus moves. In the free mode they offer some free casino credits, which don’t have a cash market value. What this allows you to do is participate in the various games that have the niche site. Once you have played a online slot machine that you like the most you in order to comfortable it will once GAME SLOT begin to play for dough.
There are three main components or locations a video slot. They are the cabinet, the reels and also the payout table. The cabinet houses all the mechanical parts of your slot contraption. The reels contain the symbols that are displayed. These symbols could be just about anything. Your very first ones had fruit on them. The payout tray is the spot where the player collects their payouts. This has now been replaced through printer several land based casinos.
All worth mentioning games closely follow the play of this board exercise. You still land on chance and community chest, nonetheless got pass go and switch to jail. Likewise you still purchase properties and built houses and hotels. What does change RAJA PLAY within each version of the SLOT GAME. This, I believe, is what keeps players coming previously. For instance the bonus game in the Monopoly Slots Here and already SLOT GAME is known as Free Parking Jackpot Bonus. These bonus rounds have become the game although game that keeps slot players glued to their seats.
There are different types of slot machines like the multiplier and also the buy-a-pay. It is vital an individual are associated with each one in every of these slots so a person would means to determine which slot greatest for for your corporation.
…
Free Online Slots – A Real Fund Approach To Take
#5- Sun And Moon (Aristocrat)-This game is real easy to recognise and features quite the bonus accomplish. The actual action graphics suffer in comparison to what IGT offers, but nonetheless well put forth. Features an Aztek inspired theme, all you might have you need to do is get two scattered Sun and/or Moon symbols on adjacent reels from left to right to initiate the bonus. Two symbols ensure 5 free spins, three will to obtain 10 spins, four gets you 20 spins and if you’re fortunate enough to get five symbols then your prize is 50 free spins. KUDA189 winning line is at 2x pay keep in mind and there is a chance to re-trigger some free operates.
#5: Your life can improvement in a split second. See #4. Since they way your can change at an online game like Roulette is should take anything you own and bet it in one spin from the roulette wheel. In slots you can be playing the way you normally play soon after boom – suddenly you’ve just won $200k.
Slots which be observed in coffee shops and cafes are frequently programmed as hot places. The attractive bright lights and the inviting sounds of the slot machines have this enticing effect to people who are eating to absolve their foods quickly to make certain that they can engage in slot games immediately.
To offer you an tyoe of one area the fruit machine cheats addressed, was the double or quit option. This means that if you win, individuals SLOT GAMING opportunity to press control button to examine if you will win twofold. it’s a game of chance right? Wrong, the machines were developed to produce a loser whenever. There was no luck involved.
GAME SLOT Managing your and traders indeed needed even when playing. Especially that playing slots can be a form of gamble, it is advisable to keep check out. These very common and simple ways to win slots are often overlooked by people as long as they enter the casino and face the slot fitness machines. But if you are a wise player, you’ll for sure win in case you understand and polish your managerial skills toward cash and time frame.
Another popular game amongst online gamblers are slot machines, whole offer payouts ranging from 70% to 99%. Granted most regarded online casinos would never offer a SLOT GAME that paid less than 95%. To make sure that would make slots one of the most profitable game title. if you knew in advance what the percentage payout was, many forums/websites claim find out the percentage, but one wonders that arrived at that number the actual first place, (the casinos will either lie not really give the particular payouts).
Fact: Number. There are more losing combos than successful. Also, the appearance of highest winning combination occurs very rarely. The smaller the payouts, more number of that time period those winning combos feel. And the larger the payout, the less number of times that combination is going o appear.
…
A Critical Overview Among The Cyber Dragon Skill Stop Slot Machine
The slot has an additional way november 23 – Free Spins. Yes, spin three or more scatters and activate deals are going to Spins bonus game. Far more scatters get the more free spins you get. So, for three scatters you will be awarded with 15 free spins, for 4 scatters – with 20 free spins, and spin five scatters and your bonus game with 25 free spins. Of course in vehicles spins bonus round you win additional win amounts for free, moreover all your winnings through the bonus game will be tripled.
On to bigger, better things, you ought to look at how much MB of memory credit card has and whether demand an AGP or PCI graphics greeting card. In order to find out whether your slot is actually definitely an AGP or PCI Click Here, you will have the instruction by instruction on ways to figure this out. And look for out exactly how much MB or memory market or topic . its really up for. It ranges from about 128MB to 768MB depending on how great well-developed body is stronger your Computer games to be. Most of the better games require an even better one that perform rather well, and requires a higher memory. Complies with you shouldn’t really require check much else, the actual you buy (if fairly new) should come with all the newest shaders and parts tact for the unit.
Roulette is often a wheel based game played at a stretched out table. Two betting areas make up its surface, the inner area, having numbers, as well as the outer, having colored areas. As with DINA 189 in use today, the colored blocks are alternating red and black for numbers 1 through 36. Green backgrounds adorn the 0 and the 00. The wheel has 37 slots (American ones have 38) with aren’t colored background as quantity of on the table. The wheel is under goes a one directional spin by the croupier, who also tosses a small plastic ball in and the second direction. When the wheel in order to a stop, the ball also settles down on the numbered slots.
As far as gaming is concerned, most persons that are concerned with it already a Wii or something similar. The gaming capability is often a nice touch, but I do not think that will be a considerable part of Roku’s future plans. Just don’t forget thrust their appeal.
Now can are prepared to play, in order to your allotted time and money. When your set finances are used up, stop. When your time is reached, quit playing. SLOT GAMING Do not lead yourself to bankruptcy.
Some of your GAME SLOT common online bingo rooms in the united kingdom are: 888ladies, BlackpoolClub Bingo, Gala Bingo, Foxy Bingo, Ladbrokes Bingo, Jackpotjoy, Littlewoods Bingo, Paddy Power Bingo, Sky Bingo, Mecca Bingo, Wink Bingo and Virgin Bingo.
Everyone possess a favorite regarding SLOT GAME, option to no be required to limit you to ultimately just a person particular. Try putting a few coins in a bunch numerous games in order to experiment using the information is nowadays.
One question that gets asked all the time is where can I play Monopoly slots on the net? The answer is actually you are in the United States, totally. Wagerworks makes on online version of the game. But, as of your date, the casinos have got powered by this software don’t accept US players. So, for now, you must visit a land based casino to play this game.
…
The Best Online Video Poker Machines Around
Online slot owners supply you with to find out necessary expressions. As it can be seen, issues are in your hands, just be braver and go ahead to winning in will casino slot games! Online slots could becoming major craze proper. Everyone is scrambling to find the actual site while using the best casino games on it. Online slots actually find their roots in American the historical past. A man by the name of Charles Fey created the prototype associated with this game all approach back in 1887 in San Francisco, California.
First, set yourself perform. Be bound to have financial. They do not receive vouchers in playing slots. Then, set a measure to spend for that day on that game. An individual consumed this amount, stop playing and come back again next evening. Do not use all your take advantage just one sitting and setting. Next, set KRATON BET . Once it rings, stop playing and get out from the casino. Another, tell GAME SLOT you to ultimately abandon the equipment once won by you the slot tournament. Don’t be so greedy convinced that you want more victories. However, if you still have funds in your roll bank, anyone may still try other slot golf games. Yes, do not think that machine an individual had won is lucky to help you to be win time and again again. No, it will just take all income and a person lose a lot more.
3) Incredible Spiderman – this is the one of the people video slot machines that can make the most of the film tie in. It has three features and Troublesome provide some seriously big wins with thanks to the Marvel Hero Jackpot.
Then watch as the various screens illustrate. The title screen will show the name of method and sometimes the developer. The game screen will demonstrate what program it employs. You need to look at certain aspects of that screen to see how to play that particular machine.Also, activity . will usually tell you ways high the Cherry and Bell Bonus go. Doable ! usually tell whether or not the cherries go to 12, 9, 6 or 3, and also whether the bells go 7, 3 or the. The best ones to beat are the ones that cherry’s check out 3 and bells go to 2.These calls for less period for play and fewer money to overcome.
Bingo-The bingo room gets capacity of accommodating 3,600 people. Standard bingo game is scheduled twice day after day. Apart from the regular game some some huge cash SLOT ONLINE games like Money Machine, Money Wheel, Cars, Crazy L, and Crazy T etc are often played. It’s got non- smoking sections where people with kids can take advantage of too.
If you wish to play, it is the to plan in advance and be sure how long you become playing guarantee you might give yourself a spending budget. You should not necessarily willing down the sink a regarding money on this particular. It is an efficient form of recreation and could also earn for you some moolah. However, losing a fortune is certainly not advisable.
Make sure you play maximum coins when imperative. Some machines pay on specific wins on the first coin, other types on another and every winning combination on the third, SLOT CASINO with regard to Blazing 7’s. On machines that have several lines, play all of the lines.
Video poker is a questionnaire of online slots. The difference is that, an individual are play correctly, you can put the odds in your favor. Learn how to play video poker, put the odds within your favor, a person have a significantly better regarding winning.
…
Bar X Fruit Machine Online
The Mu Mu World Skill Stop Slot Machine comes from Japan and it quite easy to. The basic switches are marked on gear so there’s no difficulty in employing it. The machine does not accept coins, and you can operate the machine to have fun tokens.
Thunderstruck is a 5-reel, 9 pay-line video slot from Microgaming. They come in wilds, scatters, 15 free spins, 38 winning combinations, and a great jackpot of 10,000 money. Symbols on the reels include Hammer, Fist, Castle, Lightning, and Horn. Thunderstruck features a special pull in the young girls.
Though https://mylink.la/vegeta9 is DDR2 1066MHz, tend to be two not many motherboards which support this kind. The recommended speed to go after is DDR2 800MHz dual channel 2GB. Most motherboards come with 4 DIMM slots; and also have can install two sets of the dual channel RAM to bring the total memory to 4GB. Few applications can fully utilized the 4GB memory size yet, nevertheless it really never hurt to find more memory yard. It also has changed the world GAMING SLOT you can save your memory upgrade cost for the subsequent few years of age.
Of course the beauty and excitement brought about by the bright lights of Las Vegas are still unparalleled especially by will slot machine play version in the online market place. The main difference however is that you should be able delight in the games even this would mean have the cash usually spent when planning an actual casino.
Another good thing about this is it GAME SLOT can be very to be able to win jackpots. Since tend to be done online, one can download and install software that enable you to increase you chances of winning illustrates jackpot. That you will likely win the jackpot on your own very first spin.
#6- Twin Win (IGT)-A great game with an oceanic flavor, great looking artwork and incredibly clever gaming dynamics. There are 15 lines to play and you can play in denominations from pennies to quarters. There isn’t a formal bonus round in this particular game, which killed it’s ranking a little, however the real excitement comes each morning twin single symbols. Winning one line can actually win you twice for the line. I’ve personally seen some huge hits, regardless of whether betting it’s a good. There are plenty of Twin Win machines around one particular I recommend trying over.
Playing free slots is a great way to get acquainted with the game. Beginners are already familiar with virtual slot machines wherein they have found that place virtual money to put the machine to play mode. The goal is basically to hit the winning combination or combinations. SLOT ONLINE Around the globe primarily modeled on practice or demo gaming. Today, online slots are a long way away from its early ancestors: the mechanical slot supplies. Whereas the mechanism of the slots determines nothing at all of the overall game in the past, at the moment online slots are run by a syllabus called the random number generator. Free virtual slot machine games operate with these programs too.
Finally, employ lessons. You may possibly not know it, but almost every resort casino in Nevada will give you free lessons about the particular various games are acted. You can learn the particulars of the games that a person before you ever put a single chip concerning the felt. Free lessons are the best way of developing the kind of comfort level that make Las Vegas vacations less intimidating and many more fun.
…
Free Online Slots – A Real Fund Best Choice
It Still is real coin. Don’t forget that even though your chips are found numbers on the screen, it is REAL dollars spent. This may sound a little silly, but sometimes people forget that that is certainly how they end up losing lots of money.
It is often a good idea for which join the slots cub at any casino a person go with. This is one approach SLOT CASINO you can lessen the amount of money that you lose when you will find a way to get things on the casino free for anybody.
Win at slot machines #3: Somewhere you won’t find the proper job paying machines is concerning the table gaming applications. This is because the table game players typically spend more money at the casino then slots players, and the casino does not want them being annoyed your sounds of machines investing. Remember you’ll find the bad paying machines around the table movie.
The first electromechanical slot version was invented in 1954. Soon there were other versions of casino wars that take a cent rate, therefore, the quantity of wishing perform in the one-armed bandit is building. Since then, both casino operators have begun to use more slots brought up, accept checks, tickets, tokens, paper, for numerous in sport Slots become expensive. But after a period of time thanks using a casino to attract new players have appeared a cent slot laptops. As new versions of slots allowed to be put on the net payments more coins, and the majority of players wasnt able to afford create such large bets, the decission was taken that minimal value of coins in slot machines was up one red cent.
It’s really too bad I missed the Hanabi Full Screen Skill Stop Slot Machine sooner, because at first I was searching for that Best Casino wars that dispersed money. Seriously, it didn’t even dawn on me that everything had switched over to the telltale electronic tickets until about three months when we started going. Just goes to a person how much he was winning. It’s nice SLOT ONLINE find out that these Antique Pai gow poker give you tokens in order to that old time interest it.
If you play Rainbow Riches, can’t help see the crystal clear graphics and the cool sound effects. Jingling coins and leprechauns and rainbows and pots of gold are all very well rendered. Slots have advanced quite a bit since greatest idea . of the hand-pulled lever operated mechanical machines. The theme is Irish with Leprechauns and pots of gold and doesn’t look incongruous on a casino slot equipment. KUDA189 can play Rainbow Riches on several spin-offs on the GAME SLOT machine as well, as good as the Win Big Shindig which includes. And the remote feature what? Rainbow Riches offers an online version too! It feels and appears exactly like the real thing and one more absolutely no difference. Something you should get there be any difference? Both online and offline are computer controlled machines employ the same software.
Here is really a few helpful pointers for choosing best online casino slot action. First, all of these establishments provide you with a first deposit bonus, so make sure you take them into consideration. You should try to read on the rules and regulations very carefully, because some of them are far simpler to collect than some others. This is just “Free” money these people are giving you, so don’t ruin.
…
Rainbow Riches Slot Machine Review
Here definitely are a few ideas for choosing best online casino slot action. First, all of all of these establishments supply you with a first deposit bonus, so make sure you take them into consideration. You be compelled to read the actual years rules and regulations very carefully, because some from them are less complicated to collect than other folks. This is just “Free” money these people are giving you, so don’t ruin.
Second, wish to o wedding ushers right traditional casino. Not all casinos are for everyone, such that you just should select which one is made you. Moreover, every casino has a fixed payout rate and truly figure out which payout is probably the most promising. Practically if unwanted weight to utilize big amount of money, a lot more choose the casino providing the best payout SLOT CASINO swiftness.
Free winning casino strategy #3 – Most belonging to the table games are worth playing on the slot items. One in particular that sticks out is none other then poker. Advertising can find some winning methods on poker and look the game inside and out you will make more money from the casino players naturally.
If https://game03.mahabetx77.online/ hit between the equivalent amount of money to 49% profit, then discover play again with that same machine. Your odds of of getting the jackpot are greatly high as it might be a “hot slot”. For example, if you commenced spinning for $100 and have about $100-$149 as profit, provide you . an indication that the slot you are playing is that provides the best payout SLOT ONLINE .
First, look on an elevated platform or carousel. The casino will want the higher payouts to be visible through the most people. Other patrons are usually to keep gambling after seeing a person win heavy.
GAME SLOT Pay Motocross! is a 5-reel, 25 pay-line progressive video slot from Real Time Gaming computer system software. It comes with wilds, scatters, up to 12 free spins, and 25 winning combinations. Symbols on the reels include PayDirt! Sign, Gold Nugget, Gold Mine, Bandit, Gold Pan, Lantern, and Tremendous.
It’s almost a dead giveaway here, except for the fact that the R4 DS comes in it’s own R4 DS Box. But you’ll realize that once you open the box, the contents with the box are indifferent to the M3 DS Simply, you get related light blue colored keychain / carry case that comes with the M3 DS simply. An individual everything you need, straight out of the box. This includes the R4 DS slot 1 cartridge, a USB microSD Reader / writer (and this actually allows for you to use your microSD like a USB Drive) as well as the keychain carry bag and computer software CD.
3) The amazing Spiderman – this is another one associated with those video casino wars that makes the most of that film tie in. It has three features and This may also provide some seriously big wins with thanks to the Marvel Hero Jackpot.
…
Finally Exposed: Fruit Machine Cheats And Scams – Slot Machine Secrets And Fair Play
Knowledge of Random Number Generators or RNG’s. These RNG’s produce random numbers each second and are displayed when the reel ceases. And since these are all taken at random, solution to have acquire a chance because we don’t know exactly when the right sets of numbers seem required for all of us to earn. There are times that when a player stops playing soon after spins, the next player may win the jackpot. The actual best supply of lucky might be to watch around first prior to to enjoy. If you are good at math then you may easily observe and calculate the options.
One question that gets asked all of the time is where can I play Monopoly slots about the web? The answer is if you live in the United States, you can’t. Wagerworks makes on online version belonging to the game. But, as of this date, the casinos which have been powered by this software don’t accept US players. So, for now, you must visit a land based casino perform this field.
There heylink.me/MAHABET77 are quite some fun games perform in casinos, but probably the most noticeable of these are slot machines and roulette. Both games are heavily dependent on chance, having such unbeatable house blades. Given their popularity to however, one can’t help but ask: May the better game?
Slots end up being be inside of coffee shops and cafes are GAME SLOT frequently programmed as hot slots. The attractive bright lights and the inviting sounds of the slot machines have this enticing effect to people who are eating for you to complete their foods quickly to make certain that they can engage in slot games immediately.
The lower priced Roku 2 HD at $60.00 and Roku 2 HD at $80.00 still come that isn’t IR remote, however you can also get the newer remote control, that includes an Angry Birds license separately.
If you want to recognize how to win at slot machines, the critical thing you have to learn is money executives. While you are actually playing, it is crucial that you know where you stand monetarily. For this reason I suggest begin playing some free SLOT GAME. Some from the larger internet casinos such as Casino King provide many free slot machine games for which practice. It needs to then record your contribution and earnings on searching for display of which may be exactly this is equally when you are playing with real profits.
If gaming is not your thing and near someone concerned about storing individual media on a flash drive, then consider saving some dollars with the Roku 2 HD or 2 XD.
…
How To Raise Your Chances Of Winning In The Slot Machine
Another online gambling myth bought in the type of reverse mindsets. You’ve lost five straight hands of Texas Hold ‘Em. The cards are eventually bound to fall in your favor. Betting as per to this theory can be detrimental. Streaks of bad luck don’t necessarily lead to be able to path of excellent fortune. Regarding what you’ve heard, there’s no way to turn on the juice and completely control the hobby. Online casino games aren’t programmed permit for flawless games after a succession of poor individuals. It’s important to bear in mind each previous hand does not have effect on your next one; just on account of your last slot pull earned a hefty bonus does not mean it continue to come true.
Large jackpots mean fewer smaller affiliate marketor payouts. Big winners’ fortunes are financed not by the casino but by many losers. It is advisable to select machines with small to moderate jackpots. For likely to wager, you’ll be able to GAME ONLINE SLOT much better chance of winning 800 coins than you enjoy chasing 20,000 coins.
It s incredibly easy to start playing start off winning. Necessary to do is search SLOT ONLINE a good online casino that your goal is to join that incorporates ton of slot games that you like. After you find one, it became a two step process in order to start playing and memorable.
In an e-casino ligne however, things are narrowed consistent with your option. No more walking around tables, watching people play and waiting to ones turn to sit down on the table and play. Whilst latest computer trends nowadays, things may have gone simpler this time.
The R4 and R4i cards along with wonderful features that can enhance your gaming method. Both cards enhance the use different devices while you make involving them for just one thing together with other. The cards have the proportions of storing all types of game files including videos and music files. Will be able to slot in the cards within your game console and all of them to download games files online. They also include features for transferring files and documents from one console towards other.
In order to win the major jackpot a person would should place the utmost bet down and ensure all five Arabian man symbols show on the one line. This is the only GAMING SLOT GACOR method a player can win the most amount funds.
There are many online websites that allow a user to play free casino wars. Some focus solely on slots and other gambling games such as blackjack and poker. These websites include ez slots casino, slots mamma and Vegas casino. Other websites offer slot machine play all of your documents other typical online games such as puzzle games; arcade games and word games.
If you eagerly want to be able to win at slot machines, the most important thing you need to learn is money applications. While CRYPTO BET77 are actually playing, it is vital that you know where you stand with money. For this reason I suggest commence playing some free slot game. Many larger online casinos such as Casino King provide many free slot machine games for for you to definitely practice. It really is going then record your contribution and earnings on an electronic display can be exactly liquids when are usually playing with real bankroll.
…
Games – Which Would Be Easiest Perform
Franken Rewards are a 5-reel, 20 payline video slot all with regards to a mad scientist in his “spare parts” laboratory. Made released in September, the year 2007. Franken Cash accepts coins from $0.01 to $1.00, as well as the maximum associated with coins may can bet per spin is two-hundred. The maximum jackpot is 2,500 coins.
Another advantage that includes the free online slots reality that you can browse through multiple slot games and learn the right way to play prior to wagering any real profits.
Slot Car Racing – the game takes in which the world of Formula 1 and thousand-horse power cars in your online browser because race against other Formula 1 cars on a track that resembles best selling Silverstone! Do you have GAME ONLINE SLOT what it takes to master an F1 car? https://site06.gg189.live/ out by experiencing!
Slot machine gaming is a kind of gambling, where money is usually the basic unit. You may make it grow, or watch it fade out of your hands. Always be bother a lot if small amounts of money could happen. However, playing the slots wouldn’t work inside your only have minimal choices SLOT ONLINE .
A player must limit himself or herself when staking bets in a slot machine game. In fact, when one starts to reduce bets, may best to stop. Also, the limit dont want to be very GAMING SLOT GACOR ten percent of the account credits for it’s safer perform this way. For instance, if your player does have a thousand dollars on the account and possesses decided to risk hundred, then or perhaps she must stop playing the slot if the account remains with nine hundred. In it, a person loses far more than he or she earns. Hence, it’s advisable to be practical and try playing not dangerous.
Blackjack. Healthiness is the main idea belonging to the game would be to accumulate cards with point totals as near to 18. It should be done without finding out about 21 along with other cards are represented by their number.
What ever the offer from the casino must read guidelines on the promotion page of the casino world wide web. If you don’t follow the rules to your letter you won’t get the promotion. So please, visit rules of each offer!
…
Slot Machines – Brief History
The odds of winning online game are based on luck no element impact or predict the upshot of the board game. Bingo games are played for fun, as no decisions have. However, there are many essential tips that give you a better to be able to win recreation. Playing one card at some time is suggested and banging should be prevented while dabbing. A paper card with lower number should be selected. It has more possibility of getting the numbers closer with each. In Overall games, it is suggested that you come out early uncover the first set set. It is essential to be courteous and share the winning amount on the list of partners. Ideally, the associated with winning are when you play with fewer affiliates. Some even record their games if they’re trying out some special games. It’s possible to dab.
The odds of winning sport are subject to luck and no element can influence or predict the upshot of the program. Bingo games are played for fun, as no decisions need pertaining to being made. However, there a couple of essential tips that supply better to be able to win the game. Playing one card when is suggested and banging should be prevented while dabbing. A paper card with lower number should be selected. It has more possibility of GAMING SLOT GACOR getting the numbers closer along with. In Overall games, it is required that you come out early and then get the first set set. It is essential to be courteous and share the winning amount among the partners. Ideally, the odds of winning are when you play with fewer clients. Some even record their games if may possibly trying out some special games. It is simple to dash.
Get to know your are familiar with the game along the machine, this is very very important to the fresh players. The squad who are online or perhaps in land casinos should remember to keep in mind that they get trained with the that might playing on the machines. Its every player’s dream november 23 on a slot gear.
There really are number of different manufactures. The most popular ones are Scalextric, Carrera, AFX, Life Like, Revell and SCX. Sets for these makes are available from hobby stores, large dept stores and SLOT ONLINE online shopping sites including Ebay and amazon. Scalextric, Carrera and SCX have the widest connected with cars including analog and digital versions.
There instantly things that you’ll require to know before actually starting sport. It is better you’ll be able to read a lot of about online game so that you just play it correctly. Thankfully common misconception among the members. They think that past performance can have some impact the gameplay. Some also think that the long run events can be predicted through the help of the past results. SLOT MUDAH MAXWIN is far from true. There is a game of sheer one-time only chance. Luck factor is quite essential in this on the internet. The best part of bingo is that it’s easy much more about and find out. But you need to practice it again and accomplish. You can play free roulette online.
Scratch cards can be found in internet casinos and in various locations give lotteries. All you want do is scratch amazing “coating” to the card to master if you’ve won a prize. Most cards aren’t a winner and truly is definitely not for a new player to establish a strategy to enhance their odds. Frankly, playing slots games is vulnerable to give you more playing time.
GAME ONLINE SLOT If you decide to do play a progressive game, be specific play highest number of coins so that to end up getting the progressive-jackpot. If you play a compact amount, observing win a good sized amount, though the astronomical amount obtain win more than progressive group.
If you want to try out gambling without risking too much, why don’t you try going onto a of the older casinos provide some free games regarding slot machines just an individual could examine playing associated with establishments. They may ask a person to fill up some information sheets, but that is it. You can play within their slot machines for free!
…
Top Work With Play At No Download Slots
Silver Dollar Casino is giving approach range of games. Offering casino games like roulette, slots, video poker, and blackjack. Anyone can play these games in their download version and by instant work.
Now, beneath are secrets on how to win slot tournaments whether online or land based. The very first thing GAME ONLINE SLOT would know how slot machines work. JURAGAN4D are actually operated by random number generator or RNG which is electronic. This RNG alters and determines the consequence of the game or the combination thousand times each few moments.
Under most important mode you choose coins needed between three.10 or 0.20. In regular mode this win a spin your winnings tend to be transferred to super meter at the top machine. You can preserve from here or bank your winnings by playing in Collect tab.
Slot machines are certainly one of the attractions in on-line casinos. With these machines, the golfer need cease an expert to acquire. He does not ought to be capable at strategies or math make the odds in his favor. Slot machine games are played purely on luck and merely about anyone who is of legal age can listen to it. Today, free slot machine games play online which enable it to be accessed from just about SLOT ONLINE any gaming websites in the online. These games may be played with real money or basically for fun simply no money connected.
A player should start with investing current stake. It is best enhance the stake every time he or she loses and lower the stake every time he or she profits.
We have mentioned by the earlier paragraphs that you inquire about freebies and bonuses the casino offers. This is very important for you to at least have compensation even inside your had many losing blues. Find and enjoy with slot machines that zero cost rounds or free spins. Lookup those that supply extra other bonuses. If there are any opportunities that purchase have complimentary items, snap it up. For example, if the casino anyone a club card, stimulate it and do not forget get a it everytime you play the game. Insert it at the designated area in gear to be given the chance to accrue points GAMING SLOT GACOR a person may trade for comps.
You demand a computer costs three hundred dollars more than 300 revenue. You need a access to your Internet. Essential ingredients . a lifelong gambling bank the scale of 500 big stakes or even so called sessional one the dimensions 200-300 big stakes. I can’t go into detail – to together with 100 dollars will be a little more than enough, also, having opened a forex account on-line, be sure that realize that some get a benefit from fifty to one hundred dollars on average. It is actually enough to begin with.
…
Best Sports Games Ever
So what’s the slot machine tip that’ll make basically winner? Stop being selfish! Before you put your money at risk, think with what you only desire to achieve, besides having easy. Do you want to play for some number of hours, or do you want to win an exact dollar amount, or combine of both?
Check the pay table of each SLOT GAME and note which has the highest payouts. Choose those video poker machines which have access to a percentage of 90 and above. The 1st real reason why you need to get near each machine is actually payouts are printed carefully. Sometimes, they are not published to the pay table plan. At times, they are printed with the instructions are usually posted through the machine.
One thing that these controllers do have, that some others do not, is motion-sensitivity. The technology is not nearly as advanced as that found in the WII, however it’s still in that location. There are different actions that occur, based upon movements along with the game you can be playing. Additionally, unlike the WII, the motion sensors can be turned off – which enables you to play an online game without messing with expressions.
PRIMA BET78 can decide to use the balls they win whenever pests are not playing, or exchange them for tokens or prizes such as pens or cigarette lighters. In Japan, cash gambling is illegal, so cash prizes can not be awarded. To circumvent this, the tokens can usually be taken up a convenient exchange centre – generally located very close by, maybe along with a separate room near the pachinko studio.
So a person online slot machine games work? Software program embedded in the system randomly picks a lot of and translates it in order to corresponding symbol in each virtual reel and correlates it this other reels to form a concoction. If a winning combination is hit, the computer enables the virtual machine to dispense cash, otherwise it go. The number of possible combinations depends on the parameters used with programmers. Typically, the quantity of possible outcomes is endless. Hence, slot machines are aptly categorized as per game of chance. You might as somewhat be continuously playing the game for a highly long time win the jackpot. Strategies can sometimes work, however the overall result is ultimately decided by plan promises.
A player just downloads the game and clicks the ‘tournament’ button within lobby belonging to the online cyber casino. There are instructions to follow and the user follows they. First, he registers and after that, the nurse can see how long he for you to the conquer. The entrance fee costs because SLOT GAMING as $2 to $5 a week.
Slot machines are a video game of gamble. There really is no skill involved. GAME SLOT Regardless of you win is with regards to the number of drums within the machine along with the variety of combinations that occur on such basis as these drums and value.
Before Childs was positiioned in the book, he already had three arrest record, he was arrested 45 times. A couple of these arrests came from gaming and others were grand larceny prices. Childs was convicted about 7 times for specifically slot machine game cheating. Childs is an experienced of doing what he is doing best. The ironic part that is that you ask Childs if he thinks that have to another wrong in slot cheating anf the husband will decline.
…
The Way You Select Your Internet Casino
Once we get everyone setup with French fries the game commences and also it usually takes about 3 to 5 hours regarding to win once again. In the meantime, we possess a waitress who comes by and gets these Poker Players drinks, whether it be water, soda, or adult beverages by the bar. Yes, just most notably the casinos as well as how we all look in internet marketing is if we’re gonna be lose money, we might as well lose it to various other instead associated with an casino.
With a stopwatch, children can measure the time it takes their slot cars to take on the track and, in doing so, explore the SLOT ONLINE shape found in a slot car affects its speed. Kids can realize wind resistance and aerodynamics can create a vehicle go faster.
Remember, not all machines give you the same jackpot amount that is definitely the intent behind which the difficulty of playing in all the GAME SLOT machines isn’t same. The the jackpot amount more is acquire waterborne illnesses losing the actual. Therefore, if you do dont you have the skills of recreation and wouldn’t like to lose income unnecessarily, it is preferable to avoid playing online that offers high jackpot amount.
Others believe that if a unit has just paid out a fairly large payout that it won’t payout again for some time. Who knows whether any of the strategies go about doing work. One thing for certain is whenever there is any strong indication the player do, makers will soon do how much they can alter that.
If you propose to play, it is the to plan in advance and know for sure how long you become playing because you can provide to yourself a low cost. You should cease willing down the sink a associated with money on this. It is the perfect form of recreation and also earn for you some financial. However, losing a fortune is definitely not advisable.
When tend to be playing inside bonus slots, you preferably should know that less one is the most and achievable expect good quality thrill while playing the games. Totally free whataburger coupons bonus slots are for many people who don’t worry all-around line agreed payment. There can be games that have 2 a lot more bonus selling points and features. One of the three bonuses could be good while may end that good and hybrids not love it or not. To make without anything with this sort does not happen, you can choose a sport that just one bonus feature option that such as SLOT CASINO . Choosing KRATON BET with uninteresting bonus features will just waste your serious amounts of efforts you just put into playing the.
In sport you get what is named a Spider web feature. In which activated once the symbol appears on reels two and four also must attend the same time. Would be to the video slot goes wild and your changes of obtaining high-payouts are doubled as a result of many pay line merger.
You are visiting casinos more in addition to frequently. A person tried to avoid gambling by promising yourself that can you go anymore, but it never is compatible. You keep going back to the casino, regardless of the negative aftermath.
…
Delve Deeper Into Slots Online
Blackjack or 21 has become easiest casino games to explore and compete. The idea of the game is to be a hand closer to 21 then an dealer. When playing Blackjack, regardless which of how to versions you may be playing, sport is between you and the dealer regardless of how many players are for the table. Practice free, the many versions of Blackjack to get the game you like best. Demonstration determined your game chosen develop a technique you will utilize in a real money game. Hand calculators pocket some serious take advantage this game and it is available in download and flash versions as well as Live Dealer Gambling houses.
It is important SLOT ONLINE that anyone might have self control and the discipline to stay to your limit so that you won’t much more money. Always remember that playing slots is gambling and in gambling losing is predictably. Play only in an amount an individual are willing to lose therefore after losing you can convince yourself that experience paid plenty of money that provided you with quite best entertainment you ever had. The majority of the players who do not set this limit usually end lets start work on a associated with regrets his or her livelihood is ruined because of drastic loss in a slot machine game.
Always remember that when you play slots, you really need full quantity. That is why you should stay down players the company you think may annoy you. Annoying people will eventually cause distraction. Getting sometimes lead you to having a detrimental mood actually run and screw up your clear mind. This is disadvantageous for anybody. So, it is advisable may SLOT CASINO transfer to a new machine is it possible are many noisy or irritating people surrounding you so might win casino slot supplies.
The main thing was that We to buy he was utilized to playing. Now the Hanabi Full Screen Skill Stop Slot Machine wasn’t in local casino, but it had been similar together with a lot of other Casino Slot Machines he acted as. The basic one, two, or three coins per spin, but since they difference was this one didn’t have one of us pull-down levers on the side. It seemed a a lot more up-to-speed the new times although it was refurbished its own matters.
(3) Need to one of the highest quality options for online casinos, the Live Dealer Home. These are the most interactive version of the online casino where the live dealer through a video feed from an actual land based casino will greet somebody. You can interact with the dealer and to additional players who may be playing by your table. Live dealer casinos will having a real casino experience and not leave your home.
Generally, well-built calculate associated with per spin so a person simply can play in slot machines in accordance to monetary. KRATONBET will be fun to play in a slot wherein you GAME SLOT possess at least 10 operates. Learning how to assess a machine is means to to increase your profits.
You are visiting casinos more and more frequently. Anyone could have tried to avoid gambling by promising yourself that they’re worth go anymore, but it never is employed. You keep going back for the casino, regardless of the negative backlashes.
…
How To Win Playing Money Games Online
If are usually not yet convinced additionally would rather venture with a crowded, smoky, germ laden gambling hall, I still wish you much opportunities. One thing believe about when heading back the typical big city casino is that without even having to begin your front door, you can open other doors to winning funding.
Fact: Quite a while players hold experienced that quite usually a winning combo comes by, short of 1 correct symbolic representation. But in long run, it on no account suggests how the winning combination is throughout the corner. The needed misses are found to be GAMING SLOT GACOR another random combination.
You have hundreds of choices put it to use to playing slot machines online. You will discover numerous different software platforms offering everything from 3 reel and 5 reel machines to video, bonus and jackpot progressive pay-out odds. You can choose from downloading an entire software suite including regarding games and / or play the no download version which opens your favorite game in your computer screen window without more when compared with free account and just click of the mouse.
First, you have to consider the reality that you can enjoy these games anytime and anywhere get. There is that comfort factor in the administration area that entices people to go online and start playing. Provided you have your computer, an internet connection, your or debit card with you, an individual set capable to play. Indicates that you can make for this GAME ONLINE SLOT in the comforts of your home, within your hotel room while on business trips, and even during lunch time at your house of efforts. You don’t have to be bothered about people disturbing you or breaking into fights and dealing is not loud rock music. It is like having your own private VIP gaming room at your house . or anywhere you have the environment.
Online Slots Strategy Three: Double your dollars. There are various types of online casino wars that offer double the jackpots. Double is a huge amount of better as opposed to a traditional winnings, so have to take regarding it. If the machine pays double, are usually not likely to have to pay double for the bet, but you can sure have the opportunity to get double the payout.
Tip #3 As you advance as being a player, SLOT ONLINE be able to bluff. You need to know the game well and bluff only if you feel secure that the other players will not call your bluff.
There would be a number of several manufactures. Essentially http://172.232.249.118/ are Scalextric, Carrera, AFX, Life Like, Revell and SCX. Sets for these makes are on hand from hobby stores, large dept stores and online shopping sites including Amazon and ebay. Scalextric, Carrera and SCX have the widest array of cars including analog and digital couples.
…
Pizza Slice Method – Roulette Gambling Techniques
The other they may offer you is the chance to play for gratis for sixty minutes. https://lakinassociates.org/ will give you with a specific quantity bonus credits to exercise. If you lose them on the hour your own trial has over. If you end up winning on the inside hour perhaps you might be able to keep your winnings but a few very specific restrictions. You’ll need to study the rules and regulations very carefully regarding this kind of. Each casino has its own set of rules generally.
In a nutshell, the R4 / R4i is simply a card which enables in order to definitely run multimedia files or game files on your DS. No editing of the system files is required; it is strictly a ‘soft mod’ that has no effect on your NDS in that is. You just insert the R4i / R4 card in the GAME SLOT, along with the R4 / R4i software will run.
These machines happen regarding three reel slot machines. They do not have c slot machines program or c soft machine software included within them. Are generally not fount to SLOT CASINO add batteries always.
The best slot machines to win are quite often located close winning claims booth. It is the casinos would to help attract more players who will see individuals lining up in the claims booth cheering and talking concerning their winnings.
There’s also an interesting feature for this Monopoly video slot where you can gamble any winnings possess to by your overall health and double them up by picking red or black from a deck of cards. You can also keep half your winnings when want and select to spin up discussions .. You can preserve as many times as you like with this feature, therefore it can be well worth your to take some risks with small wins that could be built up into some decent pay-out odds.
If you happen to be first time player of slots, focus on to find out about the regulations governing the game first. Researching through the online market place and asking the staff of the casino concerning their certain rules are extra efforts you must at least do SLOT ONLINE if you want a better and fulfilling game. In addition, try inquiring through your staff of this casino about any details that you will be needing in your game. A few selected most important matters you end up being asking are details upon the payouts, giveaways, and poker bonuses. Do not hesitate to question them as is just their job – to entertain and assist you as clients.
The main thing was that I’d to buy something he was utilized to positively playing. Now the Hanabi Full Screen Skill Stop Slot Machine wasn’t the local casino, but in the victorian era similar to a lot of other Casino Slot Machines he competed. The basic one, two, or three coins per spin, but since they difference was this one didn’t have one of these kinds of pull-down levers on the medial side. It seemed a much more up-to-speed but now times despite the fact that it was refurbished simply by itself.
…
Gambling – Free Casino Slots
Fact: True, but not entirely. A game you just require no skill or any strategy, the payouts are pretty decent. Imagine sitting in the blackjack table and playing your luck with no strategy. Might be end up in debt for necessary to know.
At these casinos they’ll either let you to enter an absolutely free mode, or give you bonus moves. In the free mode they is able to offer some free casino credits, which do not have cash dollar value. What this allows you to do is take part in the various games that take any presctiption the place. Once you have played a online slot machine that you like SLOT CASINO the most you seem comfortable from it once fruits and vegetables to play for funding.
Since Acquired now spending some of my summers in Reno I decided that the smart money move were patronize the so-called local casinos that cater towards local population rather style over the tourist casinos on the strip. A problem here being that the shrewd locals were receiving superior reward cards and a better total deal then an stupid tourists who patronized the deprive.
In a nutshell, the R4 / R4i just card which enables a person run multimedia files or game files on your DS. No editing of your system files is required; it is strictly a ‘soft mod’ that does not affect your NDS in that is. You just insert the R4i / R4 card into the GAME SLOT, and also the R4 / R4i software will run.
It is very easy begin playing start off winning. Produce do is search a good online casino that you would want to join that has a ton of slot games that you like. After https://game05.ags9.online/ find one, it can be a two step process which causes the area start playing and prosperous.
There are three critical sides you should prefer playing online; better deals with the SLOT ONLINE casino inside your action, a lot more multi-million dollar jackpots and more tournaments.
The slots are hosted by right casinos online, so one more no compromise on the graphics and also the speed of access. Even slot the guitar player chooses commences with 50,000 credits, enough that you sustain for a lot. What’s more, every time you get back the site, the credits are repaired!
…
A Can It My Online Gambling World
GAME MENU – People select this menu, you will certainly be instantly taken up a associated with all on the game files, homebrew applications, etc. you’ve stored using your microSD cards. You can use the controller pad on the NDS to pick the file you need to load. Should you be loading a sport for your very first time, you’ll end up prompted, after selecting the game, to substantiate that you need to create a save apply for the title. This is needed if you to be able to save you game. Your game saves are stored on issue microSD card as the overall game files themselves – famous . fantastic train delete those games later, to renew other files, as could copy your save game files to your PC, for future use as you prepare to stay in the hand that game again.
Now, ideas secrets regarding how to win slot tournaments whether online or land focused. The first thing is understand how pai gow poker work. Slots are actually operated by random number generator or RNG along with that is electronic. This RNG alters and determines the outcome of the game or the combination thousand times each second.
If you hit any where from the equivalent amount of money to 49% profit, then you can play again with that same machine. Your odds of of having the jackpot are greatly high as it may be a “hot slot”. For example, if you began spinning for $100 an individual also have about $100-$149 as profit, this is an indication that the slot are generally playing factor that provides the best SLOT ONLINE commission.
They online slot games have a range of pictures, from tigers to apples, bananas and cherries. When a person all three you triumph. Many use RTG (Real Time Gaming) free of cost . one on the top software developers for your slots. These includes the download, a flash client and are mobile, can perform take your game anywhere you for you to go. There’s also Progressive slots, you can basically win a lifetime jackpot and also you only spend out several dollars, as with most gambling, GAME SLOT your odds of winning the jackpot is similar to winning a lottery, few good, but it’s fun. Car or truck . to play as many coins which you’ve got to win the jackpot, the risk is higher and safe and sound ? the take care of.
You are visiting casinos more plus more frequently. Anyone could have tried to prevent gambling by promising yourself that you would not go anymore, but it never is appropriate. You keep going back for the casino, regardless of the negative effects.
If consideration to experience gambling without risking too much, how about we you try going towards a of the older casinos supply some free games regarding slot machines just in which means you could explore playing SLOT CASINO of establishments. They may ask a person fill up some information sheets, but that is it. You get to play in their slot machines for cost-free!
ANGKASA189 is where all these web based casino make money. Regardless of your chances of any victory, whenever you is just what will sustain internet casino profitable through the years because your slightest modifications may possess a dramatic result on both possibilities found in a win and edge atlanta divorce attorneys given challenge.
…
Gambling Systems – Do We Need Any Of Them?
These three games allow players wireless strategies could help sway the odds in their favor. But keep in mind, anyone could have to find to within the games in order to get the best probability. If you can’t say for sure what you’re doing, you could be better off playing the slots xbox games.
If you are playing a progressive slot and your bankroll is just too short to play max coins, move down a coin size. Rather than playing the dollar progressive games, have fun with the quarter progressive games. Prolonged as undertake it ! play max coins, however land the jackpot on that online game.
The credit of initiating the casino game in United States goes to Mr. Benjamin Bugsy Siegal. He started a Casino in Las vegas in the late 1940’s. Binion Horseshoe, Stupak and Benny also added their contribution to the Bugsy era and did start to build Las vegas, nevada as could be today. Online casino can be very important into the gambler. Cannot put themselves away online casino. Additionally SLOT ONLINE became an enthusiast of online casino once i saw the idea.
Lucky Charmer – This online slot is most common for good bonuses. May see 2nd screen bonus feature. Increasing your GAMING SLOT GACOR 3 musical pipes, and also when you make it to the bonus round, the charmer plays option. But, to activate the bonus round, you should be able to strike the King Cobra at the 3rd pay-line.
If you were lucky enough to win on youtube videos slot machine, leave that machine. Do not think that machine could be the ‘lucky machine’ for an individual. DINA189 made you win once truly will not let upon the next games definitely. Remember that video poker machines are regulated by random number generator and ought to electrically driven. In every second, it changes the mixture of symbols for lots of times. And the most of the time, the combinations aren’t in favor of . If you still possess the time or remaining balance in your allotted money, then perhaps you can try the other slot machines. Look for the video slot that offers high bonuses and high payouts but requiring fewer coins.
This will assist you to play the right amount of coins for method payout. Which machine offers better limits? Which machine offers better odds? Wish play any machine, be in the machine escalating best suited to you.
Tip #1 The most obvious is to make sure you know the rules of pontoon. It is always a good idea to have a strategy when you play blackjack. All winning systems are based on a basic strategy which contains statistically speaking, there exists only one best action a player can require each GAME ONLINE SLOT among the possible hands he can receive versus each possible upcard the seller may may have.
Slot machines are one of the attractions in on line casinos. With these machines, the user need not be an expert to find. He does not in order to be be used to strategies or math to deliver the odds in his favor. Slots are played purely on luck and about anyone who is of legal age can be. Today, free slot machine games play online and will be accessed from around any gaming websites on the internet. These games may be played with real money or simply for fun with no money demanded.
…
We Play Bingo – Don’t You Can? Bingo Tips Advice And Strategy Guides
If you’re first time player of slots, it is best to observe the laws governing the game first. Researching through the online market place and asking the staff of the casino with regards to their certain rules are extra efforts you need to at least do if you’d like a better and fulfilling game. In addition, try inquiring out of your staff on the casino about any details that you’ll be needing in your game. The majority of the most important things you in order to asking are details upon the payouts, giveaways, and offers. Do not hesitate to question them as this is their job – to entertain and assist you as their clients.
To avoid losing big amount dollars at slots, you should set an allowance for yourself before . Once you have exhausted your budget for a session, you should leave the slot and move on to. There is no point in losing endless retirement in a hope to win. In case you win, you can not use your winning credits to play more. Since the chances of winning and losing are equal in slot machines, you can never be bound to win added. Therefore, you can be happy using you have won.
Goa has loads of casinos for visitors. Some of the well-known names are casino Royale at Mandovi, Casino Pride in Panjim, Casino Carnival in the Mariott in Goa, Dunes at the Zuri White Sands Resort and the probability Casino and Resort in Dona Paula.
Second, wish to o wedding ushers right traditional casino. Not all casinos are for everyone, such you actually should pick which one is perfect for SLOT ONLINE you. Moreover, DINA189 has a predetermined payout rate and should really figure out which payout is essentially the most promising. Practically if oodles of flab . to take advantage big degrees of money, make sure you choose the casino offers the best payout selling price.
Within a nutshell, the R4 / R4i is simply a card which enables an individual run multimedia files or game files on your DS. No editing of this system files is required; it is strictly a ‘soft mod’ that has no effect on your NDS in in any manner. You just insert the R4i / R4 card in the GAME SLOT, and also the R4 / R4i software will move.
A player just downloads the game and clicks the ‘tournament’ button your market lobby on the online gambling establishment. There are instructions to follow and the player follows these. First, he registers and after that, he will see what distance he can be always to the innovator SLOT CASINO . The entrance fee costs as low as $2 to $5 in 24 hours.
Second, you will need to decide on a way to finance your account and withdraw your winnings. Each online casino offers multiple solutions to accomplish this, so read over everything very carefully, and select the option you think is good for your affliction. The great thing this step their process, may be the payment option you select, will almost assuredly work for good other online casino pick to join.
Upon understanding that the machine is an experienced slot, do not place big bets at this point. You need to do a bankroll test first. Locations tips in which you should consider when doing bankroll push. If the machine is giving over 50% much more profit, then leave that machine as well as prevent playing energy. Chances are, the spin price you you an oversized loss. If you have anything near identical shoes you wear amount to 49% of the money and profits, you’ll be able to stay and play with this machine again. That machine is more than likely a good machine permits let you hit an jackpot within the.
…
How November 23 In Slots – Win Playing Video Poker Machines Tips
The first electromechanical slot version was invented in 1954. Soon there were other versions of casino wars that have a cent rate, therefore, the amount wishing perform in the one-armed bandit is growing. Since then, both casino operators have did start to use more slots brought up, accept checks, tickets, tokens, paper, for impacts in online game Slots become expensive. But after a period of time thanks using a casino appeal to new players have appeared a cent slot computers. As new versions of slots allowed in order to become put on the web payments more coins, and a lot players would not want to afford additional medications such large bets, the decission was taken that the minimum value of coins in slot machines was up one red cent.
One of the great reasons for having playing from the internet is its simplicity when you’re thinking of mechanics. It is not necessary to insert coins, push buttons, and pull carrying handles. So that you can spin the reels to win the prize, it is only to take a click about a mouse button to achieve that. If you want maximize or decrease your bets or cash the actual prize simple to do is to still click the mouse.
DINA 189 should be expecting to pay as low as $20 bucks, but bigger replica banks will run about $80. Each the actual first is a bit different to the others, however made to undertake the same thing: maintain your change and take money out of your friends. You need to treat them like arcade games SLOT ONLINE in your property.
If you need to grant online slot machines a chance, then the product or service you place down a money confines. Do not bet any cash that will need hold. You as well should not spend any borrowed money situation! You should have a fair reason that explain why you would like play slot games. An individual merely require a a number of minutes of fun, that’s alright. All the Same, purchasing wish perform as you would like to win a great deal, you need to you should take a pace back for per minute.
3Dice has been on the receiving end of plenty of awards associated with years associated with industry, including Best Work Team and USA Friendly Casino from the Year, are only a few GAME SLOT of their total prestigious awards in their trophy situation. Owned and operating by Gold Consulting S.A., the principle Danmar Investment Group, this casino is fully licensed and regulated by the Curacao Gaming Authority.
Casino games are favored. It depends on chance and luck. Another crucial thing is blueprint. Applying the right strategy for play the game can influence be constructive. There are several involving casino activities. One of the popular games made available from the online as well as the offline casinos is SLOT CASINO Live dealer roulette.
Flower Power – This machine is ideal for multiple pay-lines. It may offer only 1000 coins, but an important feature about it is this : ‘less the coin figures, higher the winning chances’. And, when compared with multiple- pay-lines, so include lot of winning combining. You will love it.
…
Online Slots Tips – To Win Big
Be absolute to set reasonable goals. Supposing you’re in order to risk $200 on simple . slot or video poker game. It’s going to be wishful thinking to expect to turn $200 into $10,000, but it’s possible you have a realistic chance flip $200 into $250, consume 25% gain in a very short effort. Where else can you get 25% on dollars and enjoyable doing so it? But you must quit as soon as this goal is achieved. Alternatively hand, if you are planning to keep your $200 stake last 3 days hours, play a 25-cent as well as a 5-cent contraption. Stop at the end of the pre-set time period, it doesn’t matter if you’re ahead or in the back of.
In slots, one on the common myths is that playing on machines that haven’t paid out for a hard while increases one’s regarding winning whenever compared with playing on machines offering frequent payouts SLOT ONLINE . It is not the might. The random number generator helps to ensure that everyone has got an equal chance at sport. Regardless of the machine’s frequency of payouts, the percentages of winning still remain the same.
There might be times when you are able ride benefit stakes merely good. But what about those instances when you are only able to do with minimal choices? Should you give up playing all in all?
The best slot machines to win are frequently located on the winning claims booth. This is a the casinos would want to attract more players may see SLOT CASINO would like an explanation lining up in the claims booth cheering and talking with regards to their winnings.
Avoid machines which are placed beside a hot video slot machine. Most likely, these machines are cold slots because casinos do not usually place two good performing machines adjacent every single other.
Then watch as the various screens give. The title screen will show the name of shed pounds and sometimes the company. The game screen will a person what program it mes. DINA189 need to look at certain aspects of that screen to see how to play that particular machine.Also, examine will usually tell you how high the Cherry and Bell Bonus go. You can usually tell whether or not the cherries go to 12, 9, 6 or 3, as well as whether the bells go 7, 3 or only two. The best ones to beat are those who cherry’s check out 3 and bells check out 2.These calls for less period for play GAME SLOT and fewer money to strike.
(3) The reason one of the most effective options for online casinos, the Live Dealer E-casino. These are the most interactive version of the online casino wherein a live dealer through a slidemovie feed from an actual land based casino will greet we. You can interact with the dealer and along with players who may be playing at your table. Live dealer casinos will will give you real casino experience leave real estate.
…
Play Free Mega Joker Online
Once you have chosen the associated with slot game you are happy with, determine is to decide a machine that you think have the top chance of letting you win. Here is the key tip: It isn’t so much the sort of game you decide on. To choose a winning machine, you have to pay more attention to how administrators manage the machines.
One question that gets asked all of the time is where can I play Monopoly slots online? The answer is when you dwell in the United States, you can’t. Wagerworks makes on online version from the game. But, as this date, the casinos which usually powered by this software SLOT ONLINE do not accept US players. So, for now, you must visit a land based casino perform this program.
In blackjack the typical player will be giving household an side of somewhere between 5%-10%. An accurate GAME SLOT crackerjack card counter from a one-deck game, which is quiet difficult to find today, would’ve a 2%-3% edge about the house. Just try pulling this off in actuality. As soon as the casino understands that you are winning if at all possible be escorted out of your casino. Within a multiple deck game that is the norm our crackerjack card counter is probably playing about dead despite the real estate.
Invite your pals when you play. Can be more wonderful. Besides, they will be one to remind you not to spend the money. As soon as you enter the casino, think positively. Mental playing and winning attracts positive energy. Enjoyable because you are there perform and take pleasure with. Do not think merely of winning perhaps luck will elude you may.
No, it’s not necessary a permit to purchase one. These are novelty machines, not the big time slots you play in Las Vegas. They do pay out jackpots, only the spare change an individual inside is launched. Casinos use tokens to control payouts and people that in order to break within them. The tokens themselves have no value at all once right out of the building. Anyone dumb enough to cash them in will acquire a free ride from the area police.
If you’re a first time player of slots, it is better SLOT CASINO to discover the likes and dislikes governing sport first. Researching through the internet and asking the staff of the casino regarding certain rules are extra efforts you must at least do if you need a better and fulfilling game. In addition, try inquiring from the staff of this casino about any details that you will be needing inside your game. Several of the best most important things you should be asking are details relating to the payouts, giveaways, and extras. Do not hesitate to asking as is just their job – to entertain and assist you as customers.
Do not use your prize perform. To avoid this, have your prize in go to. Casinos require cash in positively playing. With check, you can depart from temptation of making use of your prize up.
Once we get everyone setup with Casino chips the game commences therefore it usually takes about 3 to 5 hours for somebody to make. In the meantime, we have a waitress who comes by and gets these Poker Players drinks, whether you choose water, soda, or adult beverages through the bar. Yes, just like the casinos and the way we all look web marketing is if we’re going to lose money, we should lose it to various other instead of a casino.
…
Shopping Made Simple – Buy Gifts Online
Some rewards are larger, such as complimentary trips to a buffet or another restaurant in the casino. When the place the playing at has a hotel, get get the lowest room rate (or at no charge nights). For anybody who is a escalating roller, you get airfare or taxi to and from the casino.
If you pass a little money, GAME SLOT whether or not it is not progressive jackpot, edit and view your prize money. If you do canrrrt you create the money you have set by themselves for day time meet from wearing non-standard and several minutes . in day-to-day or not one but two.
What then are the benefits of of roulette over slots and vice versa? To begin with, let’s using the specifications. Both are simple and fast-paced games, but any kind of debate, slots is definitely faster and simpler than live. This game is also easier to understand than roulette, and you will only take a few rounds to decide which patterns win and which ones lose.
Machines near game tables also have high associated with being cold slots. Bad machines regularly placed here because casinos would like to prevent the cheering slot winners from disturbing those you are playing poker, blackjack, and other table games. These kinds of casino games require lots of concentration exceedingly.
Here certainly few good data for seeking the best online casino slot action. First, all among these establishments supply you with a first deposit bonus, so make sure you take them into consideration. You should certainly read the actual years rules and regulations very carefully, because some associated with these are less complicated to collect than additional. This is just “Free” money they will are giving you, so don’t confuse.
Players everywhere on the world will appreciate most of the awesome features that 3Dice offers their players, within the chat room, to the daily free tournaments for many of the players. Developing stop there because once you play you will get rewarded with loyalty and benefits health supplement SLOT ONLINE your VIP status.
mylink.la/wak69 offer different know-how. However, the online games are really exciting perform. You can have a very good experience playing this kind of online golf game SLOT CASINO . You can sit at the comfort of your home and enjoy this exciting online application. But one thing you will miss, i actually.e. the mood and the environment of actuality casino.
To help out with keeping purchase in the company have added traction magnets to automobile to exert downward force thereby allowing cars stay on the track at faster rates. This also allows acquire to make vertical climbs and perform loop the loop.
…
Tips For Playing Roulette Online
To verify the type of cherry machine you are dealing with you have to have to follow these guidelines. Sit back check out the screens the game goes through while preserving the earth . not being played. Determine the company that is the machine. Once the game screen flashes you can see common history in top of the left location. It is either a “Dyna” perhaps a “Game”. Usually are WAK69 ‘s promote most of all cherry specialists.
Do not use your prize perform. To avoid this, have your prize in examination. Casinos require cash in trying to play. With check, you can avoid temptation relying on your prize up.
Here are a few helpful suggestions for selecting the best online casino slot action. First, all of these establishments suggest to a first deposit bonus, so make sure you try them out. You preferably should read over the rules and regulations very carefully, because some with them are less complicated to collect than some others. This is just “Free” money that they are giving you, so don’t mess up.
It Is still real profits. Don’t forget that even though your chips are just numbers on a screen, it is REAL money SLOT ONLINE . This may sound a little silly, but sometimes people forget that that is certainly how they end up losing a lot of money.
Always do not forget that when you play slots, you prefer full awareness. That is why you should stay due to GAME SLOT players that you think may annoy your business. Annoying people will eventually cause distraction. This could sometimes allow you to having a wrong mood in the long run and screw your own clear self. This is disadvantageous for people. So, it is advisable may transfer option machine partnerships are many noisy or irritating people surrounding you so you can find win casino slot piece of equipment.
Their tournament lobby is consistently jumping with action. 24/7 there is a tournament doing for all players. Every hour, VIP players are given a freeroll tournament to enter, furthermore goes on around the hands of time. Special event tournaments are grounds for additional battles.
Do not use your prize to play. To avoid this, have your prize at bay. Casinos require cash in being. With check, you can get apart from temptation of employing SLOT CASINO your prize up.
All we’ve got to say is we know a great buy many of us saw the. For the past 4 years we’ve been looking for these Best Pai gow poker like the fireplace Drift Skill Stop Video slot that comes from international casino houses. The reason we chose these over others was since most were chosen for only one month or two before being shipped away and off to warehouses to distribute however chose that will. This meant we were basically getting primary slot machine for really large cheaper.
…
How To Double Your Slots Money
The associated with winning sport are made from luck with element impact or predict the upshot of the on the web. Bingo games are played for fun, as no decisions should be made. However, there are a handful of essential tips that give your better possibility to win the overall game. Playing one card at a real kick is suggested and banging should be prevented while dabbing. A paper card with lower number should be selected. It has more chance of getting tinier businesses closer properly. In Overall games, it is suggested that you come out early and earn the first set distributed. It is essential to be courteous and share the winning amount among the partners. Ideally, the odds of winning are when you play with fewer patrons. Some even record their games if they’re trying out some special games. It is simple to dab.
This can assist you to play the right amount of coins for issue payout. Which machine offers better ordinances? Which machine offers better odds? Wish play any machine, play in the machine at this point best worthy you.
The table version of Poker may be the best. The various versions of poker are designed as a table game and you’re able play free games to develop your skill so an individual ready in order to on other players. Number of obvious abundant poker games available all the time for all skill levels as well as many Free-rolls, Tournaments and High-Roller tournaments. Will be a lot of money being made playing online poker and who knows, you are able to even win yourself a seat using a WSOP scenario. The table game of poker is for sale in download, flash version and some live dealer casinos.
Tip #3 As you advance as being a GAME ONLINE SLOT player, how can you bluff. You must understand the game well and bluff only when you feel secure that the other players will not call your bluff.
Blackjack. The whole idea of the game GAMING SLOT GACOR end up being to accumulate cards with point totals as close to 22. It should be done without going through 21 and then other cards are represented by their number.
There are really a number of manufactures. One of the most popular ones are Scalextric, Carrera, AFX, Life Like, Revell and SCX. Sets for these makes are obtainable from hobby stores, large dept stores and from online shopping sites including Ebay and amazon. Scalextric, Carrera and SCX have the widest associated with cars including analog and digital batches.
SLOT ONLINE Red White and Win is an antique 3-reel, single pay-line progressive slot from Vegas Systems. There are WAK69 winning combinations. Symbols on the reels include USA Flag, Bald Eagle, George Washington, Statue of Liberty, and Dollars.
Familiarize yourself with guidelines of the particular slot tournament than you might be playing of. Although the actual play end up being similar, the payout and re-buy systems may stand out. Some online slot tournaments will enable you to re-buy credits after you have used your initial credits. Can be important learn if you are on the best choice board and expect to be paid online. Each tournament also decides the will determine the success. In some slot tournaments, the user with one of the most credits in the end of the established amount of time wins. Other tournaments have a playoff by using a predetermined quantity of finalists.
…
How To Backup Ps3 Games
The principle in playing slots is temperance. Be contented if you win. Do not continue playing and betting and while using money you might have won. You’ll for sure lose the use every single piece of what you have won. The RNG is sensible not to help you to win as expected. Remember that it changes the combinations thousands of times harmful offers too . second. Also, if there isn’t any coin to use, stop.
Playing https://solo.to/wak69vip is often a great for you to get acquainted with the video. Beginners are exposed to virtual slot machines wherein they can place virtual money to place the machine to play mode. The goal is basically to hit the winning combination or combinations. Is definitely primarily devised for practice or demo programs. Today, online slots are a far cry from its early ancestors: the mechanical slot items. Whereas the mechanism on the slot machines determines consequence of the game in the past, at present online slots are run by a software called the random number generator. Free virtual slot machines operate SLOT ONLINE training can actually be programs also.
It Continues to be real . Don’t forget that even though your chips basically just numbers on the screen, it is REAL money. This may sound a little silly, but sometimes people forget that and that is exactly how they end up losing big.
The advantage is where all these web based casino funds from. Regardless of your chances of something like a victory, benefit is precisely what will beneficial internet casino profitable over the years because your slightest modifications may possess a dramatic result on your possibilities of a win while the edge each given sport.
The first bonus game you’ll encounter (if you’re lucky enough) when you play rainbow riches is called Roads to Riches. It consists of a spinning wheel that reveals your progress in the stage. If you get three or more leprechaun symbols on your screen, it initiates the bonus level. The appearance of three or more well symbols starts the Wishing Wells bonus contest. This involves clicking on the random well out of multiple types. You get a multiplying factor plus money is multiplied by that much. Finally, you GAME SLOT provide the Pots of Gold incentive. This level is started when you get three Pots of Gold symbols on your screen, the center three ones only excluding the left-most and right-most reels.
Goodness, gracious great balls of start! Okay, it’s not that fantastic, but it might definitely light your start. Sorry, kind of cheesy what amount can i you are you able to blame me when view the Fire Drift Skill Stop Video slot. If you just like the color red alone and not played a Slot Machines For Sale in your life, this is able to definitely enliven your house in a heartbeat. November 19 aside though, we get nothing but compliments onto the play and entertainment one of these Casino Slot machine games offer.
In the beginning, I had no idea what seem for, but this new little adventure not could prove costly than exactly the Hanabi Full Screen Skill Stop Slot machine itself. You know the way all ideal Slot Machines are wired at the casino with under wires and everything else, right? Well the good news is these are already set about be set up. All you have to do is this into a wall like you would a full time income SLOT CASINO lamp assaulted vacuum when you’re sweeping.
There are even slots that are hooked up to main computer with several casinos providing the players and the money. These mega slots pay out huge payoffs and are always worth a few plays with the hope that you will get exceptionally routine.
…
Enjoy The Casino Thrill Without Threat With Free Casino Bets
All you need to do is defined in the coins, spin the reels and watch to discover if your symbols format. If you’re going to play online slots, ponder these little suggestions to enhance your experience.
This Wild West themed casino started their business in GAME ONLINE SLOT two thousand and seven. With https://tap.bio/@wak69 of Vegas Technology in giving the best gaming experience for their players.
An ideal online slots strategy in order to sign track of slot machine tournaments. These kinds SLOT ONLINE of tournaments are highly sought after in today’s world and you will find them at both large also as small online casinos throughout the world. Believe it or not, merchandise online the actually that these of tournaments are fun, exciting and will eventually help you land lets start on huge cash awards. You will not believe, generally awards can be as high as $25,000 ( first place), $10,000 ( second place) and $5,000 ( third place).
Tip #2. Know the payout schedule before sitting yourself down at a slot appliance. Just like in poker, knowledge among the odds and payouts is vital to developing a good strategy.
A DS R4 / R4i card is a storage device that enables you to store and view data for instance images, text files, videos, sound files or homebrew games. The R4 / R4i card bypasses the encryption round the Nintendo DS, enabling files to be run directly from a storage medium pertaining to instance a Micro SD chip. Second generation flash cards since the R4 / R4i make use of the DS game card slot (SLOT-1), instead with the GBA game card slot (SLOT-2), making them easier make use of.
Tip #1 Just almost every poker, you’ve GAMING SLOT GACOR know the sport of video poker. There is an extensive variant of video poker games, with each having a separate set of winning card combinations. Is actually usually a good idea to pay attention to whether or not a machine uses one 52-deck of cards much more than a particular. The more cards there are, the less likely the player will success.
These three games allow players the following strategies in which help sway the odds in their favor. But keep in mind, possess to learn about to use the games being able to to obtain the best lines. If you concept what you’re doing, you should be at an advantage playing the slots quests.
…
Best Online Casino Slots
The best strategy for meeting this double-your-money challenge is to appear for a solitary pay line, two-coin machine with a modest jackpot and a pay table featuring an excellent range of medium sized prizes.
Another popular game amongst online gamblers are slot machines, GAMING SLOT GACOR they will offer payouts ranging from 70% to 99%. Granted most well-known online casinos would never offer a slot game that paid less than 95%. Assure that would make slots the most profitable game. if you knew in advance what the percentage payout was, many forums/websites say they know the percentage, only one wonders how they arrived during that number all of the first place, (the casinos will either lie or even otherwise give precise payouts).
Another associated with winning will be always to know your limits. Know when stop. There are three ways on the best ways to stop. First, set a sum for your game tomorrow. Once the amount is consumed, cure. Second, set a time deadline for your leisure negitively effect. Once your watch alarmed, cure. Third, if you win, hinder. And if you win, have your prize not in cash but in check. Do not just stop. Abandon the machine and go out of the casino and head home. By this, you didn’t lose your own money. Returning again next occasion and try your good fortune. Look for linkfast.me/wak69 that offer higher jackpots, higher bonuses, and more spins. If there are newly opened casinos nearby, visit and play presently there. For sure, they offer higher jackpots and bonuses while giving extra prizes for leverage. Implement the same rules by yourself for an efficient play.
Be aware of how many symbols take prescription the slot machine game. When you sit down, the first thing you should notice is how many symbols are about the machine. Tinier businesses of symbols are directly proportional into the number of possible combinations you have to win.
Tip#1-Select a machine that functions a lower multiplier. Anyone who’s played restrictions of machines know that the chances of hitting a nice line pay on a 10X pay machine is drastically below what one which a 2X pay or no multiplier. Studies have shown that these lower multiplier or wild machines supply you with a 30% greater payback as opposed to runners machines offering a higher multiplier. GAME ONLINE SLOT I’m able to tell you on many occasions that I’ve almost removed my hair when I could not get anything on a 5X or maybe more slot machine on 20 dollars. The odds are through ground with those. So as tempting because your high risk, high reward slots provide greater pay, play an assortment of the lower multiplier sewing machines. You’ll find that may win more over a lengthier session than high multiplier games and a lot more frequently.
The associated with jackpots on Bar X ranges primarily based on your stake level, but like in the beginning version, the Bar X jackpot is triggered relatively often in order to many other online SLOT ONLINE slot machine games.
Craps can be a mis-leading game, the “pass line” bet, which wins in your new shooter who rolls a 7 or 11, loses on the 2, 3, or 12, and on any other number requires him to roll that number (his point) again before rolling a 7, has an even money payoff that delivers a 1.41% edge to your house. The single-roll bets basically are ridiculous: an ‘any 7’ bet pays 4:1 and provides the house a whopping 16% lip.
…
Best Slots To Win – Video Slot Gambling Casino Tips
The best strategy for meeting this double-your-money challenge is to watch out for for a single pay line, two-coin machine with a modest jackpot and a pay table featuring the range of medium sized prizes.
You would like a computer being more than 300 big ones. You need a access on the Internet. You need a lifelong gambling bank the length and width of 500 big stakes GAME ONLINE SLOT or even so called sessional one the measurements 200-300 big stakes. I will not go into detail – to together with 100 dollars will be than enough, also, having opened a news report on-line, selected that realize that some get anedge from fifty to one hundred dollars normally. It are going to enough to with.
There really number of different manufactures. The most popular ones are Scalextric, Carrera, AFX, Life Like, Revell and SCX. Sets for these makes are present from hobby stores, large dept stores and online shopping sites including Ebay and amazon. Scalextric, Carrera and SCX have the widest regarding cars including analog and digital applies.
If had been lucky enough to win on a slot machine, leave that machine. Don’t think that machine may be the GAMING SLOT GACOR ‘lucky machine’ for you. It made you win once but will not let you on the next games absolutely. Remember that slots are regulated by random number generator and could electrically electric. In every second, it changes the mixture of symbols for lot of times. And most of the time, the combinations aren’t in favor of we. If you still carry the time or remaining balance in your allotted money, then maybe you can try the other slot technological machines. Look for the video slot that offers high bonuses and high payouts but requiring fewer coins.
If you hit an outrageous Thor your winnings can be multiplied 6 times. Perhaps make potential winnings reach $150,000. Want can also click the gamble button to double or quadruple your wins.
The theory eventually became known as the theory of probability. Pascal developed this theory while solving a major issue posed with French mathematician named Chevalier De Easy. The scenario was that two players had to terminate a game before this finished although one player was clearly ahead. KOIN 555 is was dividing the stakes fairly while considering possibilities of each player eventually winning the on the web. It would be unfair to penalize the player who was ahead by dividing the pot smoothly. It would also be unfair to make the entire pot on the player can be ahead in the time, because his victory is uncertain. Pascal devised a formula for determining the probability that many player would win in the event the game happened to be played to the conclusion. Condition of probability is use within all elements of life right away.
Celtic Crown: Just a person first thought it couldn’t SLOT ONLINE have any better. Lose yourself involving charm and mystic for this Celtic Crown bonus video slot machine. Free spins are triggered with 3 or more golden harps. The Princess feature is triggered when 2, 3 & 4 reels display the Princess symbol.
The traditional version of this occurence game could be modified by simple changes to are more interesting, and so as the popularity of Checkers increased, different versions of this game came up. Some of these variants are English draughts, Canadian checkers, Lasca, Cheskers and Anti-checkers.
…
Debunking The Myths Of Online Gambling
As what their name implies, Millionaire Casino is the best casino for players that wants being treated as being a millionaire. And it can certainly start in giving you their wide range of casino games that workout from. In conjunction with every games, you may feel the a sense of “playing in addition to thing” with fine graphics and great sounds. Your thirst for online gambling will surely fill up in Millionaire Casino.
GAME ONLINE SLOT Each credit in bingo will cover two pay-lines as instead of one and usually situation. Based on this, just need to wager step 5.00 credits (pounds or dollars) to disguise all 50 lines.
There are certain things a person can need recognize before actually starting online game. It is healthier for an individual read as well as more more all over the game so as you will play it effectually. There is the only real misconception one of several players. DINA 189 seem to that past performance could have some impact on the movie. Some also imagine that the future events can be predicted is not help for the past search results. It is in any way . GAMING SLOT GACOR . It can be a game of sheer chance. Luck factor extremely important in this game. The very part of this game is the fact that it commonly be installed to learn and understand. But you would like to practice it again and gain. Will be able to play free roulette online.
There instantly things have to have to know before actually starting video game. It is better so that read a lot of about online game so for you to play it correctly. May well be a common misconception among the gamers. They think that past performance can have some have an effect on the game. Some also think that the future events can be predicted simply by the past results. It’s not at all true. game of sheer occasion. Luck factor is quite important in this gaming. The best part of this game is that it can be easy comprehend and find out. But you need to practice it again and accrue. You can play free roulette online.
There are several different creates. The most popular ones are Scalextric, Carrera, AFX, Life Like, Revell and SCX. Sets for these makes may be purchased from hobby stores, large dept stores and online shopping sites including Ebay and amazon. Scalextric, Carrera and SCX have the widest connected with cars including analog and digital frames.
SLOT ONLINE In order to win the major jackpot an individual would should place optimum bet down and make certain all five Arabian man symbols show up on the one line. This can be the only manner in which a player can win the most amount cash.
Bars & Stripes can be a 5-reel, 25 pay-line video slot provides a patriotic American plan. There is plenty of red, white, and orange. The colorful graphics would be the Statue of Liberty, hot dogs, apple pie, cookies, and a mouthwatering Thanksgiving turkey. Bars & Stripes accepts coins from $0.01 to $1.00, and the number of coins that you can bet per spin is two hundred fifty. The maximum jackpot is 50,000 gold coins.
…
More Rules To Increase Online Businesses
Online Slots have been a good option for individuals just google search will find to take pleasure in. Lots of things come and go so as with the slot machine as understanding technology gets better.
Why do people such as the free Cleopatra slots competition? It probably has a lot to do with the beautiful graphics, the music activity and reputation of the Egyptian history that’s included in it. After all, harvest know who Cleopatra could be SLOT CASINO ? In her day, Cleopatra was the useful woman in the world.
Slot machines – It has the highest number of slot machines of various denomination beginning from 1 cent to $100.The payouts within these slot machines are one of several highest in comparison to other casinos in the east sea. It has a non- smoking area too where full family appreciate the washers.
Survey the area in the casino. Frequently you’ll see ATM’s and money out stations busy several areas. Confirm if you are withdrawing or cashing in slot ticket. If they cash in tickets, check out that area to wager. If you play in a casino that still uses coins, listen for the sound money SLOT ONLINE tinkling involving tray. Frequently higher payouts are in trafficked towns.
To recognize the involving cherry machine you coping you really should follow the following tips. Sit back check out the screens the game goes through while preserving the earth . not being played. Determine REPUBLIK365 that helps machine. As soon as the game screen flashes you can see the name in the top of left local. It is either a “Dyna” perhaps “Game”. GAME SLOT Of the two separate company’s create most of all cherry entrepreneurs.
Black king pulsar skill stop machine is one of the many slot machines, which is widely loved among the people of different ages. This slot machine was also refurbished ultimately factory. Workouts thoroughly tested in the factory it was sent to different stores available.
The appropriate method of figuring out internet casino probability must aspect globe “edge” or house advantage, because payoff ratio links the advantage and your succeeding risk. Sticking with American online roulette, we place 2, $5.00 gamble. Working the maths, ([(24/38) x $5 – (14/38) x $10] / $10, implies that the casino has a 5.26percent edge over the casino player, and will be just what online casinos live to.
…
Time Management – How You Can Get Things Done In Your Online Business
At these casinos they will either can help you enter a totally free mode, or give you bonus operates. In the free mode they will furnish some free casino credits, which don’t have any cash increased value. What this allows you to do is play the various games that take the internet page. Once you have played a online slot machine that you favor the most you are comfortable by using it once you begin to play for day-to-day money.
The internet is SLOT ONLINE getting more advanced annual. When this technology was introduced to the world, its functions were only limited for research, marketing, and electronic correspondence. Today, the internet can certainly be used perform exciting games from online casinos.
Knowledge among the game is extremely important. Of course make sure that you know the basics of the overall game. You must have an idea on the foundational key to win. You need to know how these machines operate. Or maybe noticed how these machines produce good and perfect combinations towards the first and 2nd reels but fail provide you with a perfect one onto the third? Well, REPUBLIK 365 is primarily given that they machines are programmed to make. The slots have Random Number Generators permit them to look for the outcome every spin. If you’ve got knowledge on the game, then you would know there is GAME SLOT no exact timing with the spin due to the fact are all random acts by the microprocessors positioned in the workout machine.
Online Video poker machines have been a good alternative for folks just use the internet to do. Lots of things come and go in order with the slot machine as individuals technology SLOT CASINO develops.
To avoid losing big amount of money at slots, you should set an affordable for yourself before playing. Once you have exhausted your budget for a session, you should leave the slot and move by. There is no point in losing endless retirement in a hope november 23. In case you win, you ought not to use your winning credits to play more. Since chances of winning and losing are equal in slot machines, you can never be particular to win added. Therefore, you can be happy using you have won.
Slot machines are one of the attractions in casinos. Along with machines, the ball player need not necessarily an expert to victory. He does not have pertaining to being good at strategies or math develop the odds in his favor. Pai gow poker are played purely on luck for about anybody who is of legal age can participate in it. Today, free slot machine games play online as well as could be accessed from almost gaming websites in the online world. These games may be played with real money or for entertainment with required involved.
It’s really too bad I didn’t find the Hanabi Full Screen Skill Stop Slot Machine sooner, because at first I was searching for your Best Slot machines that dispersed money. Seriously, it didn’t even dawn on me that everything had switched over to the telltale electronic tickets until about three months when you started intended. Just goes to demonstrate how much he was winning. It’s nice to learn that these Antique Slots give you tokens to give that old time suit it.
The bad-paying and well-paying slot machines are usually located beside each other one. Are you not successful at one machine, the next one tends going to be able to better returns. Have an open eye for men and women who never leave device they are playing – they may be waiting for virtually any pay, or they have a loose machine and persist with winning. You’ll like to make use of out that machine learn how well it works for you. One of the most important thing to remember is just insert the $5 bill into the device – and that i recommend that place greatest bet for the first spin, as a lot more places where most jackpots are won.
…
What Are The Causes Of Gambling Reliance?
First, look on a higher platform or carousel. The casino should seek the higher payouts to be able to visible with most consumers. Other patrons are apt to keep gambling having looked at a person win leading.
The pai gow poker are also the most numerous machines in any Vegas on line casino. A typical casino usually has at least a dozen slot machines or a slot machine lounge. Even convenience stores sometimes get their SLOT ONLINE own slot machines for quick bets. Though people rarely come with a casino in order to play in the slots, downloaded the machines while waiting for a vacant spot in the poker table or until their favorite casino game starts an alternative round. Statistics show in which a night of casino gambling does not end without a visit in the slot machines for most casino client.
iqgaming.org have many pictures, from tigers to apples, bananas and cherries. When you obtain all three you take home some loot. Many use RTG (Real Time Gaming) type of one with the top software developers for your slots. These includes the download, a flash client and are mobile, doable ! take your game anywhere you want to SLOT CASINO go. There are also Progressive slots, you may well win a lifetime jackpot and only pay out several dollars, as with all gambling, the likelihood of winning the jackpot is just like winning a lottery, less good, however it’s fun. They are to play as many coins which you’ve got to win the jackpot, the risk is higher and making use of the shell out.
The Mu Mu World Skill Stop Slot Machine comes from Japan and is then quite user-friendly. The basic switches are marked about the machine so there just isn’t difficulty in using it. Gear does not accept coins, however you can even use the equipment to use tokens.
Online slot owners supply to your future necessary terminology GAME SLOT . As it can be seen, things are all in your hands, you braver and go ahead to winning in the free casino slot games! Online slots look as if becoming the craze currently. Everyone is scrambling to find the actual site along with best casino games when you strike it. Online slots actually find their roots in American history. A man by the name of Charles Fey created the prototype regarding this game all during back in 1887 in San Francisco, California.
Speaking of events, the Twin River RI casino is host to many events throughout. A 29,000 square foot event arena is often filled by some famous headline performing artists. The center hosts some great live entertainment and it has been are prospering over items on the market year. Is actually plenty of music and acting began on at Twin Rivers Casino. Additionally, the facility is also quickly banquets and special events like weddings and business conference calls.
There may times when you are able ride the high stakes that is definitely good. But what about those times when you can only do with minimal trades? Should you give up playing altogether?
Video poker is a questionaire of online slots. The big difference is that, content articles play correctly, you can put it can be in your favor. Realize how to play video poker, put the odds in your favor, an individual have a way better regarding winning.
…
Experience The Joys Of Gambling Games
Others understand if a piece of equipment has just paid out a fairly large payout that be squandered anytime soon payout again for time. Who knows whether ATM 189 of the strategies go about doing work. One thing for certain is if there is any strong indication they will do, producers will soon do issues they can alter that.
Fact: No more. There are more losing combos than winning. Also, the appearance of the actual winning combination occurs by no means. The smaller the payouts, more GAME SLOT associated with times those winning combos appear. And also the larger the payout, the less quantity of times that combination will o feel.
No matter what denomination of slot machine you pick to play, from your penny and nickel slots all method up to your high roller machines, is definitely real one thing that every slot player simply have to do before they sit down and insert their savings. Regardless of how casual a slot player you are, the great things about this action can be significant. The best part is that it will only cost a few minutes of your.
What then are extremely easy of roulette over slots and vice versa? To begin with, let’s start with the SLOT ONLINE solutions. Both are simple and fast-paced games, but without any debate, slots is definitely faster and simpler than live dealer roulette. This game is also easier to comprehend than roulette, and you will only have a few rounds to solve which patterns win and which ones lose.
It likewise wise to decide non-progressive slots to play with because the progressive ones are always programmed in order to more connected with reels and symbols. The machine produces more reels and symbols, the associated with more wins is very slim. So, the non-progressive ones are the machines in order to should insurance firm ? play who have. Some of the nice machines are also placed near coffee and snack watering holes. Casinos do this to motivate players to finish their as well as get in order to the game the soonest possible time frame.
Make sure you play maximum coins when called for. Some machines pay on specific wins for that first coin, other types on concerning and every winning combination on the third, SLOT CASINO with regard to Blazing 7’s. On machines that have several lines, play all the lines.
Mr. Robot – Contemplate if you plan on using bots as a measure to boost in order to your system. If 4 slots are taken by bots and it is a 12 slot server you’re only leaving 8 slots for real humans. Try to keep the server slots balanced to systems bots you’d like to use (if any).
…
Find Good Online Pokies Games
You come across offers all over the Internet for playing various forms of free slot games online for financial. What is there to grow in playing free slots? In every one cases you receive to keep any winnings over deals are going to money live by the casino. If you’re get lucky this could put hundreds, even 1000s of dollars to your pocket.
When the gambling was banned, variety of the slots was substituted. The sums of your prizes were replaced the new pictures in the chewing gum packages, and various tastes were depicted to be a respective new berry. The amounts of jackpot have also been increasing combined with the demand for the sytems. In order to increase jackpots additional reels were built in the machines. The slots got larger and their internal design was change regularly GAMING SLOT GACOR .
Chocolate Factory is a 5-reel, 9 pay-line video slot using a chocolate design. Welcome to a mouthwatering world of chocolate different goodies. Chocolate Factory accepts coins from $0.05 to $2.00, and greatest number of coins which you can bet per spin is 40. The maximum jackpot is 8,000 silver and gold coins.
Fact: Quite a while players enjoy experienced that quite commonly a winning combo comes by, short 1 correct expression. But in long run, it hardly ever suggests how the winning combination is all around corner. The appropriate misses basically are another random combination.
If you play Rainbow Riches, can not help spot the crystal clear graphics along with the cool sound files. Jingling coins and leprechauns and rainbows and pots of gold are acceptable rendered. IKAN 189 have evolved since you may have heard of the hand-pulled lever operated mechanical machines. The theme is Irish with Leprechauns and pots of gold as well as look incongruous on an online casino slot products GAME ONLINE SLOT . You can play Rainbow Riches on several spin-offs of the machine as well, which includes Win Big Shindig for. And a few seconds . what? Rainbow Riches along with online version too! It feels and appearance exactly like the real thing and presently there absolutely no difference. Must you want there be any huge difference? Both online and offline are computer controlled machines utilize the same software.
Your choices have a good impact onto your chances to win. The Blackjack strategy chart offers players a associated with the best choices each morning games – choices that are SLOT ONLINE supposed boost their chances to succeed. But even when making the best, most accurate choices in video game – an immediate part of winning still involves good fortune. You can make the best choice, if the dealer displays better luck then you – can lose. Additionally you can make waist decisions, but when lady luck is working for you you will win.
Scratch cards can be discovered in internet casinos and in many locations consist of lotteries. All you have to do is scratch over “coating” with the card to work out if you’ve won a prize. Most cards aren’t a winner and very little is not a way for a farmer to construct a strategy to improve their possibility. Frankly, playing slots games is preparing to give you more playing time.
…
How To Win Playing Money Games Online
It Stays real cash flow. Don’t forget that despite the fact that your chips are just numbers on the screen, it is REAL fund. This may sound a little silly, sometimes people forget that inside this device . how they end up losing lots of money.
Real world games present different suffer with. However, the online games GAME SLOT are usually exciting perform. You can have a great experience playing this associated with online quest. You can sit at the comfort of your home and love this exciting sports. But one thing you will miss, now i.e. the mood and the environment of real life casino.
Try to wait your favorite search engine and watch for slot machine games completely. You’ll be surprised at large number of search upshot of websites and pages that permit you to enjoy this video game to the fullest without risking one single dollar. So for those out there who wanted to try out this game but are afraid to lose hard-earned money, you absolutely try playing it web based.
Speaking of linknbio.com/ikan189 , the Twin River RI casino is host to many events all through the year. A 29,000 square foot event arena is often filled by some famous headline music artists. The center hosts good live entertainment and did very well over the past year. Can be plenty of music and acting moving on at Twin Rivers Betting house. Additionally, the facility is accessible for banquets and special attractions like weddings and SLOT CASINO business conferences.
In slots, one on the common myths is that playing on machines that haven’t released for quite some while increases one’s chance of winning to be able to playing on machines which provide frequent winnings. It is not the accusation in court. The random number generator means that everyone along with equal chance at the overall game. Regardless of the machine’s frequency of payouts, the odds of winning still stay.
The Lord of the Rings Slot machine is a Pachislo Slot Machine, meaning that that completely be free to control as soon as the reels SLOT ONLINE will minimize spinning throughout your turn. This enables you to infuse the same slot machine experience having a bit more skill! The slot machine also provides a mini game that accessible for for you to play between spins.
Larry’s Loot Feature is activated when 3 more Larry scatters appear anywhere on the reels. Please click each Larry symbol to disclose up using a 1000x your bet which usually $1,250, each symbol training will award a multiplier. I personally have hit for 1000x and 750x my bet all your market same week.
…
9 Steps To Internet And Online Business
The slot machine games are also the most numerous machines any kind of Vegas gambling enterprise. A typical casino usually has at least a dozen slot machines or just a slot machine lounge. Even convenience stores sometimes have their own slots for quick bets. Though people don’t usually come a few casino just to play at the slots, this person liked the machines while anticipating a vacant spot in the poker table or until their favorite casino game starts the latest round. Statistics show that a night of casino gambling does not end along with no visit at the slot machines for most casino clientele.
In the old days when casino players actually knew what had been holding doing the unchallenged king of the casino tables were the crap dining tables. This is where the term high-roller came by using. If you knew what you were, doing this is where you hung out. A shrewd better can reduce the house edge to at only 1.41% and to below 1% depending using a house’s odds policy.
A player just downloads the game and clicks the ‘tournament’ button SLOT ONLINE inside lobby belonging to the online gambling establishment. There are instructions to follow and also the player follows these. First, he registers and after that, he’ll see what lengths he end up being to the web design manager. The entrance fee costs as little as $2 to $5 each and every day.
If are generally a newbie in slot machines, don’t fret. Studying https://solo.to/ikan189 to play slots do not require too much instructions to consider. Basically, having fun with slots is about pushing buttons and pulling addresses. It can be learned in the few spins. Being a new player, will have to know tips on how to place bets so that you can maximize your spins and increase the thrilling excitement that shortly experience.
If GAME SLOT you really want to win, try having practice has. There are machines available for practices. Also, there are online slot games that you may possibly use for practice. Develop your own techniques.
It is just one of the oldest casino games played coming from the casino lovers. There is no doubt this game extremely popular among both the beginners as well as experienced bettors SLOT CASINO . Different scopes and actions for betting get the game really a very intriquing, notable and exciting casino game. Little leaguer has various betting options. They can bet by numbers, like even or odd, by colors like black or red and added.
These machines happen to be three reel slot generation devices. They do not have c slot machine games program or c soft machine software included within them. Substantial not fount to include batteries what’s more.
If you need to grant online slot machines a chance, then the product or service you place down a money confines. Do not bet any cash that steer clear of hold. You as well should not spend any borrowed money situation! You should have a fair reason as to the reasons you hope to play slot games. Purchasing merely require a limited minutes of fun, that’s alright. All the Same, purchasing wish perform as you would like to to win a great deal, maybe you should take a pace back for a flash.
…
How Perform Slot Machines
Free winning casino strategy #2 – The best game perform to win at the casino is none other then pontoon. When you take the time find out card counting strategies you will increase your odds of winning in the casino significantly. Being to predict them that the casino dealer will pull gives you’ better handle of the title.
There are three critical sides you should prefer playing online; better deals of your casino towards your action, a lot more multi-million dollar jackpots SLOT ONLINE and much more tournaments.
Slot machines were all of the rage in depression. In 1931, gambling was legalized in Nevada and slots found a home. When you attractive any casino today find row after row of slot products. They are so popular because usually are very well simple perform and have large affiliate payouts.
Break da Bank Again: Another revised slot machine with a revamped layout. Time to really crack greatest method for on normal slots game Break da Bank. The 5x multipliers combined one 15 free spin feature has the ability to payout a bundle of slot coins. 3 or GAME SLOT more safe scatters trigger the free spins.
Do not trust anyone around. You might hear people saying that many the slots are right in front row or possibly SLOT CASINO the last ones, do not listen to anyone. These types of even hear that you machines supply out a bunch of money at certain point in the course of or evening time. Do not listen to any for these gossips. Purely that as a player you need listen and trust yourself online openings.
Bingo-The bingo room have the capacity of accommodating 3,600 people. The regular bingo game is scheduled twice daily. Apart from the regular game some money games like Money Machine, Money Wheel, Cars, Crazy L, and Crazy T etc are often played. Seen on laptops . non- smoking sections where people with kids can engage in too.
The principle in playing slots is temperance. Be contented a person don’t win. Do not continue playing and betting and while using money you could have won. Certainly you’ll lose the use almost all of what get won. The RNG is sensible not to lead you to win naturally. Remember that it changes the combinations lots of times cons second. Also, if you do not have any coin to use, stop.
…
The Best Online Slots
The first electromechanical slot version was invented in 1954. Soon there were other versions of video poker machines that take a cent rate, therefore, the amount wishing to play in the one-armed bandit is growing. Since then, both casino operators have begun to use more slots brought up, accept checks, tickets, tokens, paper, for numerous in the overall game Slots become expensive. But after a thanks the casino to draw in new players have appeared a cent slot printers. As new versions of slots allowed end up being put internet payments more coins, while it will take players are unable to afford drugs such large bets, the decission was taken that the minimum value of coins in slot machines was up one brass razoo.
It’s really too bad I didn’t find the Hanabi Full Screen Skill Stop Slot Machine sooner, because at first I was searching for the Best Slot machine games that dispersed money. Seriously, it didn’t even dawn on me that everything had switched over to these electronic tickets until 3 months when we started destined. Just goes to show you just how much he was winning. It’s nice to understand that these Antique Casino wars give you tokens offer you that old time tempt it.
Experience the exciting sounds of the casino that you really need home while Crazy Diamonds machine bank. This is a replica SLOT CASINO on the larger scale featuring the real-life sounds of the casino using the jackpot light that flashes and the benefit of a bank in order to your gold. By the way, this slot machine will take 98% of coins made the world over.
A player just downloads the game and clicks the ‘tournament’ button planet lobby of your online betting house. There are instructions to follow as well as the player follows these. First, he registers and after that, he is able to see how long he should be to the leader. The entrance fee costs as little as $2 to $5 in 24 hours.
To avoid losing big amount of greenbacks at slots, you should set funds for yourself before . Once you have exhausted your pay off a session, you should leave the slot and move on. There is no point in losing endless funds in a hope november 23. In case you win, spend use your winning credits to play more. Since chances of winning and losing are equal in slot machines, you can not be guaranteed to win somewhat more. Therefore, you can be happy making use of you have won.
Apart off of the SLOT ONLINE single payout line in the of the reels, many more than one pay lines, every pay line referring to a separate coin had fun with. The symbols stopping on a particular pay line decides the win of a gambler. The common symbols are bars, cherries, double bars and sevens.
https://tap.bio/@ikan189 in these places as these want to draw more others to play slot machine games. It is a fact that when passersby hear the happy cheers and victorious yelling of slot winners, others will be enticed perform so GAME SLOT that they’ll also win at video poker machines.
The Mu Mu World Skill Stop Slot Machine comes from Japan and is defined as quite user friendly. The basic switches are marked on the machine which would mean that there isn’t an difficulty in making use of it. The equipment does not accept coins, however you may also use the machine to use tokens.
…
Play With No Deposit Casino Bonus
Always do not forget that when you play slots, you should have full awareness. That is why you should stay out of the players individual preference think may annoy clients. Annoying people will eventually cause distraction. Junk food sometimes connect you with having a detrimental mood in the long run and screw increase clear your mind. This is disadvantageous for somebody. So, it is advisable a person simply transfer distinct machine maybe there is are many noisy or irritating people surrounding you so to win casino slot supplies.
The right method of figuring out internet casino probability must aspect previously “edge” or house advantage, because payoff ratio links the advantage and your succeeding chance. Sticking with American online roulette, we place 2, $5.00 trades. Working the maths, ([(24/38) x $5 – (14/38) x $10] / $10, implies that the casino uses a 5.26percent edge over the casino player, and which isn’t just what online casinos live to receive.
SLOT ONLINE Speaking of events, the Twin River RI casino is host to many events all through the year. A 29,000 square foot event arena is often filled by some famous headline performers. The center hosts some great live entertainment it’s been are very popular over accessible products . year. Is actually plenty of music and acting transpiring at Twin Rivers Internet casino. Additionally, linkfast.me/ikan189 is also quickly banquets and special events like weddings and business meetings.
Now, you will notice GAME SLOT secrets on how to win slot tournaments whether online or land based mainly. The first thing is recognize how slot machine games work. Slots are actually operated by random number generator or RNG can be electronic. This RNG alters and determines the outcomes of the game or effectiveness thousand times each next.
So how would you determine a gambling problem is ruining your lifetime? What are quantity the indicators that it is all totally spiraling the particular control, knowning that your working life is truly becoming unmanageable?
Another thing to try to find when choosing mobile casinos for slots is they will offer flexible betting banks. You should be able to play both high and minimal stakes SLOT CASINO as compared with one and even the other. Have got to also fully understand the winning lines, betting tiers and pay table.
3Dice may be on the receiving end of regarding awards inside years all of the industry, including Best Support Team and finest USA Friendly Casino of the Year, are a few about their prestigious awards in their trophy case. Owned and operating by Gold Consulting S.A., the principle Danmar Investment Group, this casino is fully licensed and regulated by the Curacao Gaming Authority.
There are even slots that are hooked to a main computer with several casinos providing the players as well as their money. These mega slots pay out huge payoffs and are always worth several plays with the expectation that you’ll get exceptionally routine.
…
Best Slots To Win – Video Slot Gambling Casino Tips
Blackjack or 21 regarded as easiest casino games understand and hold. The idea of the game would be to a hand closer to 21 than the dealer. When playing Blackjack, regardless which of the countless versions you may be playing, the is between you and also the dealer it doesn’t many players are for the table. Practice free, known as versions of Blackjack and see the game you like best. Be successful determined your game you prefer develop something you will utilize in the real money game. You could pocket some serious profit this game and this available in download and flash versions as well as Live Dealer On-line casinos.
Slot machines are one of the many attractions in casinos. In each and every machines, the gamer need stop an expert to GAME SLOT beat the game. He does not have with regard to good at strategies or math to make the odds in his favor. Slot machines are played purely on luck for about anybody who is of legal age can be. Today, free slot machine games play online that will be accessed from virtually any gaming websites in the web. These games may be played with real money or just for fun with necessary involved.
Flower Power – This machine ideal multiple pay-lines. It may offer only 1000 coins, but beauty of it is that ‘less the coin figures, higher the winning chances’. And, more affordable multiple- pay-lines, so include lot of winning a combination. You will love it.
Slot land – This online casino slot is known for great attractive ambience, excellent odds and completely secured financial transfers. And, unlike other sites, but there’s more require you to download any software. A person play a good initial deposit of a great deal $100. There are SLOT ONLINE multiple line slots like two pay-lines, four pay-lines, five-pay lines and eight-pay lines. May pretty good chances to winning money here.
Here handful of tips regarding how to calculate the cost per spin. When you have been in the casino, you make use of you mobile phone devices so you simply can perform calculations. Perhaps the most basic mobile phone these days is equipped with a calculator tool. In calculating the fee per spin, you would be wise to multiply the sport cost, the actual line, and the number of coin put money. For example, in the event the game spend you $0.05 in 25 maximum lines, multiply $0.05 and 9 maximum lines times 1 coin bet. Indicates that likely to cost you $0.45 per spin if are playing 9 maximum lines for a nickel machine with one minimum coin bet. In which one strategy which achievable use to win at casino slot piece of equipment.
IKAN189 to search out when choosing mobile casinos for slots is whenever they offer flexible betting capabilities. You should be able to play both high and minimal stakes basically one or maybe the insects other. You have to also understand the winning lines, betting tiers and pay dining room table.
The Mu Mu World Skill Stop Slot Machine comes from Japan especially quite convenient to use SLOT CASINO . The basic switches are marked for your machine so that there are very few difficulty in using it. Gear does not accept coins, however you may also use the machine to have fun tokens.
Set a set limit for betting for yourself whether you are on online slot or perhaps in land gambling den. If you start winning then do not get too cloudy, you don’t want to lose or get addicted to it. If you start losing do not try it “one more time”.
…
Best Online Slots First Time Deposit Bonuses
At these casinos they’ll either can help you enter like the mode, or give you bonus revolves. In the free mode they is able to offer some free casino credits, which have no cash care about. What this allows you to do is within the various games that take prescription the websites. Once you have played a online slot machine that you like the most you are comfortable on it once it begins by consuming to play for income.
Pachislo machines are missing the pull down arms on along side it. The spinning is stopped with the assistance of the 3 buttons on front within the machine. Wanting to offer what is a Skill Stop SLOT ONLINE Machine. These machines aren’t meant to have pull-down arms. We can buy arms for the machine though changing the machine at all will nullify your warranty and organization isn’t chargeable for repairs merely because of problems the particular machine.
In a nutshell, the R4 / R4i is just a card which enables anyone to run multimedia files or game files on your DS. No editing belonging to the system files is required; it is strictly a ‘soft mod’ that does not affect your NDS in in whatever way. You just insert the R4i / R4 card into the GAME SLOT, and the R4 / R4i software will use.
It highly SLOT CASINO easy to start playing and initiate winning. All you do is search the online casino that you’ll need to join that posesses a ton of slot games that such as. After you find one, it became a two step process in order to start playing and winning.
By trustworthy, it doesn’t only mean someone who won’t swindle your cash. Trustworthiness also means a company who thinks of the capability of their battlers. Do they offer multiple payment and withdrawal options? Will someone help you out or answer your questions if and as you want to buy? Are you really getting paid if you win?
Here absolutely are a few helpful pointers for choosing best online casino slot action. First, https://desty.page/tinju189 of the establishments supply you with a first deposit bonus, so make sure you take them into consideration. You should certainly read in the rules and regulations very carefully, because some from them are quite easy to collect than other folks. This is just “Free” money the player are giving you, so don’t falter.
Larry’s Loot Feature is activated when 3 more Larry scatters appear anywhere on the reels. Take a look at each Larry symbol to disclose up into a 1000x your bet is actually $1,250, each symbol utilizing will award a multiplier. I personally have hit for 1000x and 750x my bet all inside same day time.
Bingo-The bingo room has the capacity of accommodating 3,600 people. The standard bingo game is scheduled twice a day. Apart from the regular game some big dollars games like Money Machine, Money Wheel, Cars, Crazy L, and Crazy T etc can also be played. Offers non- smoking sections where people with kids can play too.
…
Tv And Slot Machine Tie Ins – Quit Work?
Silver Dollar Casino is giving quite range of games. mylink.la/yolanda77 like roulette, slots, video poker, and blackjack. As well as can play these games in their download version and by instant consideration.
As the Reels Turn is a 5-reel, 15 pay-line bonus feature video i-Slot from Rival Gaming software. Snooze mode scatters, a Tommy Wong bonus round, 10 free spins, 32 winning combinations, and a jackpot of 1,000 silver and gold coins. Symbols on the reels include Tommy Wong, Bonus Chip, Ivan the Fish, and Casino Chips.
With the cards, you may enjoy playing all kinds games. GAME ONLINE SLOT You can use them perform video games in this particular fantastic area. With them, you can download games files directly and also also store them make sure that you motivation. You’re sure of enjoying playing your favorite games your overall the cards well slotted in your console.
However, a person are follow my advice, various the highest possible chance of clearing the best online slots deposit bonuses and actually making an income before you’re done.
Lucky Charmer has a second screen bonus feature sturdy fun to play. You will choose between 3 musical pipes and the charmer plays your choice if SLOT ONLINE yourrrre able to reach the bonus brown. The object that rises out of this baskets may be the one to ascertain your success. To be able to activate the feature round you will be location to hit the King Cobra at the third pay models.
With this exciting slot machine you discover GAMING SLOT GACOR several action game symbols as well as bonus features. Numerous numerous web sites where utilized play this packed slot machine. During video game you should get three progressive jackpots checked out will be awarded at random ,. This machine has three bonus features available and a max 6000 coins payout per average spin per pay row.
In order to cash out your winnings, you should try to chalk up points by wagering on certain games, ie pai gow poker. It is possible to win up to $2,000 with $100 personal cash and $100 casino cash playing roulette and certain strategy. I have done this.
…
Microgaming Slot Machine Games – Ten New 5 Reel Competitions
Second, you would o the right gifts right gambling. Not all casinos are for everyone, such that should decide which one is for you. Moreover, every casino has an established payout rate and truly figure out which payout is the most promising. Practically if unwanted weight to benefit big stages of money, make sure you choose the casino providing the best payout quote.
Win at slot machines #3: One place where you won’t find the proper job paying machines is around the table programs. This is because the table game players typically waste your money at the casino then slots players, and the casino does not want them being annoyed through sounds of machines investing SLOT CASINO . Remember you’ll find the bad paying machines around the table gaming applications.
There’s also an interesting feature for the Monopoly video slot where might gamble any winnings possess to by choosing to double them up by picking red or black from decking of charge. You can also keep half your winnings if you want and choose to spin up discussions .. You can maintain as often times as such as with this feature, consequently can be well worth your to take some risks with small wins that can be built up into some decent affiliate marketor payouts.
Mainly medicine of playing online slot games in order to have money, but the simplest way? It’s just like you’re playing the game called Galaxy Balls. Solar panel systems need you need to do is to put all identical shoes shapes or symbols from a SLOT ONLINE row. An individual know am sure on tips on how to play this one, you are able to see a screen by using a row of special emblems. Sometimes, you are able to see this from the form of shapes, fruits or even numbers in the 2-4 spinning wheels.
Then watch as the various screens exhibit to. The title screen will show the name of this system and sometimes the brand. The game screen will show you what program it works by using. You need to look at certain aspects of that screen to see how to play that particular machine.Also, as well as will usually tell you ways high the Cherry and Bell Bonus go. Can perform usually tell whether or not the cherries go to 12, 9, 6 or 3, furthermore whether the bells go 7, 3 or a couple. The best ones to beat are the ones that cherry’s pay a visit to 3 and bells check out 2.These can take less time for play and less money to beat.
Another consideration is the payout for this machine. A pretty good rule of thumb is actually GAME SLOT a machine has a healthy payout then chances are you will win less smaller payouts. A device that encompasses a lower payout will hit more often but you might not get that million dollar jackpot. Simply by whether you are looking to play long on a budget or desire to “go for broke” in order to hit the one, look into the maximum payout of the device. If the jackpot is only 500 times the coin value or less the appliance will pay smaller amounts more often and keep you playing on a relatively small budget.
Goodness, gracious great balls of a flame! Okay, it’s not that fantastic, but proceeding definitely light your hearth flames. Sorry, kind of cheesy what amount can i you are you able to blame me when find the Fire Drift Skill Stop Slot machine game. If link.space/@Tinju189 like the color red alone and not played a Slot Machines For Sale in your life, this could definitely bump up your house in a heartbeat. Might seem like aside though, we get nothing but compliments within play and entertainment these types of Casino Slot machines offer.
…
Gambling Addiction Can Destroy Your Life As Invariably It
Third always be massive jackpots. Unless your playing at one on the really big casinos at Vegas, most slot machines will simply connected to a small jackpot of several thousand. Most online casinos will supply you with a dozen slot games by using million dollar jackpots. Its the magic getting able to link individuals online slot players together through the internet. So every spin on the web is a chance at winning a life changing score.
Cool Bananas High rollers $180+ Slot spins: – This GAME SLOT may be developed by Cryptologic and allows specific $189 moves. This slot game is inspired by King Kong and the many types of food that she loves as being the theme. If somebody wins the jackpot for your maximum spin, he or she would get $200,000. If you pairs the banana icon with the mighty monkey icon, may be win a prize. This is not open to players in USA.
Another consideration is the payout of the machine. A reliable rule of thumb is actually a machine has a high payout you will win less smaller payouts. A unit that has a lower payout will hit more often but you may not get that million dollar jackpot. With regards to the whether you are wanting to play frequent on an inexpensive or want to “go for broke” to try and hit the one, look at the maximum payout of device. If the jackpot is only 500 times the coin value or less these machines will pay smaller amounts more often and a person playing on a relatively small budget.
$5 Million Touchdown is really a 5-reel, 20 pay-line video slot from Vegas Tech about American football. It accepts coins from 1 cent to $10.00, as well as the maximum connected with coins a person need to SLOT CASINO can bet per spin is 20 ($200). Are usually 40 winning combinations, a premier jackpot of 500,000 coins, wilds (Referee), scatters (Scatter), 15 free spins, collectively with a bonus pastime. To win the 15 free spins, you do hit three or more Scatter tokens. To activate the bonus round, you need to hit two Bonus symbols on a reels. include Referee, Scatter, Cheerleader, and Sportsmen.
Pachislo machines are missing the pull down arms on the side. The spinning is stopped substances that are the 3 buttons on front within the machine. This is what it then makes it a Skill Stop Console. These machines aren’t designed to have pull-down arms. A person can buy arms for the machine though changing the machine at all will nullify your warranty and the corporation isn’t in control of repairs resulting from problems with the machine.
If you hit anywhere from the equivalent amount of money to 49% profit, then may do play again with exact same machine. SLOT ONLINE Your odds of of having the jackpot are greatly high as it may be a “hot slot”. For example, if you commenced spinning for $100 and have about $100-$149 as profit, wishes an indication that the slot you are playing ‘s something that provides each best payment.
Remember, not every machines give you the same jackpot amount that is definitely the cause for which the particular problem of playing in all the machines isn’t same. Extra the jackpot amount more is the potential for losing the actual. Therefore, if you do not have the skills of the sport and shouldn’t lose your money unnecessarily, it is advisable to avoid playing online that offers high jackpot amount.
…
Slot Machine – Myths And Facts
If over and done with choosing a casino, it’s time perform. Slots are one of accomplish to play since remember that have complicated rules nor does it require techniques to win. In other words, a player will have to depend on his good luck, if you have any.
As a rule, straight, regular two-coin, three-reel machines are your best bet. The jackpot are usually relatively modest, but so is the concurrent risk. Four- or five-reel slots, featuring single, double and triple bars, sevens, or other emblems, usually offer a much bigger jackpot, but it’s harder to obtain. Progressive slots dangle enormous jackpots. Remember that the odds on such machines are even severe GAME ONLINE SLOT . But then, huge jackpots are hit on a regular. you never know when it is your lucky day.
It there exists a fairly simple process. You first need a computer with online access. A reasonably fast connection is always best. Next, establish an account using one of the online casinos. Lastly and I would suggest the primary is you may need have some interest amongst gamers of roulette. It makes it easier to learn and sensei.
For beginners to slots, the regarding playing online may definitely be a daunting a single. All too often, SLOT ONLINE beginners are powered down at online slot games and don’t play because think that playing with real funds are required. The truth is that are usually many choices to playing online. Playing with money is only one of these businesses.
Craps is a of today, the contemporary complicated games to read and learn. It offers wide variety of of bets and comes with a etiquette all its own. Some novice gamblers will be intimidated by all the experience at a craps workspace. Many don’t be aware of the difference in the pass line and a don’t pass bet. May perhaps not know that some bets might offend other players at the table, because superstition plays a large number in craps. Some players holding the dice think a don’t pass bet is often a GAMING SLOT GACOR jinx, because the device is a bet made directly against their own bet.
Decide on you’re concentrating on before begin playing and also let greed take well over. That way you have excellent shot at achieving your goal, may assure you’ll not lose more than safety measure were for you to risk first of all. Have the discipline to do it and you will have a increased satisfying gambling experience. Using common sense and being in control all of the are mighty weapons against any land based casino.
Slot cars also come in different sizing’s. The smallest size is HO or 1:64 degree. Originally solo.to/tinju189official were made for inclusion with model railways luckily these little cars are really fast then have some amazing track templates. The next size up is 1:43 scale it really is designed for that younger racer with many fun features and character cars. The 1:32 scale is a popular size car for racing at home and there exists a wide selection of sets. Essential size car is on the 1:24 and is commonly found racing at slot car raceway clubs.
…
Shopping Made Easy – Buy Gifts Online
Slot machine gaming is really a type of gambling, where money is generally the basic unit. Place either make it grow, or watch it fade right out the your hands. It would bother that much if control of money are involved. However, playing the slots wouldn’t work if only have minimal craps bets.
Get recognize your recognize the game throughout the machine, specialists are encouraging very essential the fresh players. The gamers who are online as well as SLOT ONLINE land casinos should make in mind that they get trained in with recreation that they are playing in regards to the machines. End up being every player’s dream to win on a slot machine.
Progressive slot games result in these games are attached to the other machines inside of casino. Non-progressive means GAME SLOT that the machines aren’t connected together. The implication could be odds much more expensive even for the progressive construct.
To avoid losing big amount SLOT CASINO cash at slots, you should set a budget for yourself before showing. Once you have exhausted your afford a session, you should leave the slot and move around. There is no point in losing endless amount of money in a hope november 23. In case you win, never use your winning credits to play more. Contemplating chances of winning and losing are equal in slot machines, you can not be absolute to win added. Therefore, you can be happy in what you have won.
Here a couple of tips exactly how to to calculate the cost per spin. When you are developing the casino, you can use you touch screen phones so that you can do the calculations. Perhaps the most basic mobile phone these days is along with a calculator tool. In calculating the cost per spin, you would be smart to multiply video game cost, the utmost line, and also the number of coin bet. For example, when your game financial impact a person $0.05 in 25 maximum lines, multiply $0.05 and 9 maximum lines times 1 coin bet. Indicates that it will cost you $0.45 per spin if you do are playing 9 maximum lines for a nickel machine with one minimum coin bet. Diane puttman is hoping one strategy which you may use to win at casino slot generators.
YOLANDA 77 can offer you a great gambling experience without the hustle and bustle within the casino. You may even let your children play at this Antique Video slot without the fear of turning them into gamblers. Along with this machine also it also not scared of the children falling into bad company could be encountered in an online casino environment.
So what is the slot machine tip that’ll make that you a winner? Stop being carried away! Before you put your money at risk, think about which you would like to achieve, besides having fun. Do you want to play for a certain number of hours, or do you want to win an exact dollar amount, or a variety both?
Always bear in mind when you play slots, you should have full amounts. That is why you should stay faraway from players who you think may annoy your business. Annoying people will eventually cause distraction. Getting sometimes cause having a bad mood actually run and screw increase clear mind. This is disadvantageous for anybody. So, it is advisable that you transfer option machine possibly are many noisy or irritating people surrounding you so you can find win casino slot nodes.
…
Advice And Methods For Playing Slots In Land-Based Casinos And Online
You should also choose perform a machine that has lesser winning combinations to during your spins. Lower the combinations, the better chances of winning more money. Although the jackpot amount is lesser, you will still win big as most of these types of machines have better odds in prosperous.
https://linkfast.me/tinju189 -reel, 20 payline video slot great award-winning show on tv. It was released in September, 3 years ago. The Osbournes accepts coins from $0.01 to $0.50, along with the maximum number of coins that you will bet per spin is 200. The top jackpot is 15,000 money.
What can be a slot pc? Slot machines are an automated form of gambling demand no strategy on negligence the person pulling the lever. Need to do put the coins in, pull the lever and hope for the ideal. A winner will depend on three connected with kind being displayed inside the three columns on the equipment. The winning amount is dependent on the three of a type that acquire and info on your computer amount of coin you deposited. The example, three triple bars might offer higher winnings than three single watering holes. When someone is on what ever they consider total machine, they’ll often sit for hours, refusing to cease. If you’re betting the odds, most people agree that slot machines have the smallest odds of winning. Is actually why interesting since slot machines still form the majority associated with casino’s business.
If you hit any where from the equivalent amount of money to 49% profit, then could certainly play again with that same machine. Your chances of getting the jackpot are greatly high as it might be a “hot slot”. For example, if you began spinning for $100 and you have about $100-$149 as profit, very an indication that the slot a person playing factor that allows the best SLOT ONLINE payout.
It is a good idea for one to join the slots cub at any casino that go to. This is one method in which you can lessen quantity of of money that you lose because you will find a way to get things over the casino free for the individual.
Slot machines are one of the most favorite spots in the casinos. The combination’s displayed on the reels make the adrenaline of both player and watchers surge high. It gives a good feeling being thrilled and satisfied primarily if the gamer wins the jackpot. These days, winning at pai gow poker is not brought by mere luck but by extra effort exerted using the player. Indeed, lucky charms are not really much GAME SLOT effective at slot apparel. If you are a slot player, you will need strategies get more when compared to the fun.
A system that isn’t user-friendly can take all is often a fun out on the game. Rather than just putting head into winning, you become torn between winning and finding out how to function the equipment. The best way to get surrounding this problem is to try first the free version of your games you would like. This way, as soon as you sign-up, you exclusively what you’re getting around SLOT CASINO .
There’s also an interesting feature for this Monopoly slot machine where may refine gamble any winnings you need to by you can double them up by picking red or black from a deck of enjoying. You can also keep half your winnings when want and choose to spin up the rest. You can go forward as often times as you like with this feature, the program can be worth your to take some risks with small wins that can be built up into some decent payouts.
…
The Top Casino Gambling Games
Scatter Pays: Specific symbols of the slot game that pay even if your symbols aren’t on identical shoes you wear payline. Tip: Scatter Pays pay only on a line that is been activated with a bet.
Craps is among GAMING SLOT GACOR more complicated games for more. It offers a variety of bets and it possesses an etiquette all its. Some novice gamblers will be intimidated by all the experience at a craps cubical. Many don’t know the difference in a pass line and a don’t pass bet. Could not be certain that some bets might offend other players at the table, because superstition plays a large number in online casino craps. Some players holding the dice think a don’t pass bet is a jinx, which it is a bet made directly against their unique bet.
It is even suggested that you play always with optimum bets. There are a some machines that demand place a maximum bet so that you just will become eligible for about a jackpot. Prone to want to achieve good chance at winning the jackpot, be guaranteed to bet the actual every time you play provided that you can afford it.
Bars & Stripes can be a 5-reel, 25 pay-line video slot which has a patriotic American subject matter. There is plenty of red, white, and purple. The colorful graphics include the SLOT ONLINE Statue of Liberty, hot dogs, apple pie, cookies, and a mouthwatering Thanksgiving turkey. Bars & Stripes accepts coins from $0.01 to $1.00, and highest number of coins that you can bet per spin is a pair of. The maximum jackpot is 50,000 coins.
We have mentioned on their own earlier paragraphs that you inquire about freebies and bonuses the casino will provide. This is essential you to at least have compensation even prone to had many losing doldrums. Find and get slot machines that no cost rounds or free spins. Lookup those that supply extra other bonuses. If there are any opportunities that you can have complimentary items, buy it. For example, if the casino a person with a club card, bother and don’t forget a cordless it the moment you participate in. Insert it at the designated area in gear to be given the chance to accrue points a person may trade for comps.
With mylink.la/tinju189 concerned about playing in smoky environments, playing in the home is a visual advantage. Plus, those person that do enjoy smoking will skill to GAME ONLINE SLOT do this without any flack from others. These days, many land casinos don’t allow smoking involving their poker rooms either. Statistically, many regular casino gamblers are heavy smokers, once this is any trouble for you, being property will ensure a good environment for you.
50 Lions Slot can be a 5-reels penny game, which means that although the coins in this game are presented in different denominations you can place a wager for under 1p.
…
Do You Trust These Four Online Slot Machine Myths?
It’s almost a dead giveaway here, except for your fact how the R4 DS comes in it’s own R4 DS Box. But you’ll realize that once you open the box, the contents belonging to the box are indifferent to the M3 DS Simply, you get comparable light blue colored keychain / carry case that comes with the M3 DS simply. A person receive everything you need, out of the box. This includes the R4 DS slot 1 cartridge, a USB microSD Reader / writer (and this actually allows for you to use your microSD like a USB Drive) as well as the keychain carry bag and the program CD.
Lucky Shot is a 5-reel, 20 pay-line video slot from Microgaming having a golf look. It accepts coins from 1 cent to 50 cents, and also the maximum associated with SLOT ONLINE coins that you can bet per spin is 200 ($100). There are 35 winning combinations, a top jackpot of 15,000 coins, scatters (Gopher), up to 18 free spins, alongside Gopher Bonus Game. November 23 the 18 free spins, you be required to hit three or more Golf Cart symbols. To activate the bonus round, you would be smart to hit three or more Gopher symbols on the reels. Symbols include Gopher, Lucky Shot, Golf Club, Golf Bag, Trophy, and Golfers.
The obvious minuses are: the shortage of the music. Everything you can hear during playing this online slot is the scratching (I’d call it this way) of the moving reels and the bingo-sound have got win.
When playing online pai gow poker GAME SLOT you must try to bet as often coins. As the many machines give a reward for playing the maximum bet as well as pay odds increase. Such as the if equipment has the ability to pay 2 lines, the jackpot might 1000 coins for a coin played but 2500 for right away . coin. By playing https://www.linknbio.com/tinju189 of coins you recruit a 500 coin bonus. You need to careful however because if it is a rr.25 cent machine but has 10 paylines you are wagering $2.50 with every spin. Ensure you look at how many paylines take the machine so that you don’t spend more per spin than you were planning that will help.
What is really a slot cleaner? Slot machines are an automated form of gambling that want no strategy on fault the person pulling the lever. Obtain put the coins in, pull the lever and hope of the best. A winner relies upon three from the kind being displayed involving three columns on device. The winning amount relies upon the three of a form that you get and info on your computer amount of coin you deposited. With regard to example, three triple bars might offer higher winnings than three single watering holes. When someone is on back as they consider a complete machine, they will sit for hours, refusing to cease. If you’re betting the odds, most people agree that slot machines have the actual odds of winning. System interesting since slot machines still constitute the majority a casino’s web business.
GAME MENU – A few select this menu, finish up instantly come to a listing of all from the game files, homebrew applications, etc. that you may have stored on a microSD master card. You can use the controller pad on the NDS decide on the file you in order to load. Should you be loading per game for early time, you’re prompted, after selecting the game, to confirm that you wish to create a save apply for the movie. This is needed if you want to save you game. Your game saves are stored on operates microSD card as the files themselves – famous . fantastic train delete those games later, to replace with other files, as could copy your save game files to be able to your PC, for future use before you go to continue playing that game again.
With a stopwatch, children can study the time it takes their slot cars to attempt the track and, in doing so, explore any shape of this slot car affects its speed. Kids can can easily wind resistance and aerodynamics can develop a SLOT CASINO vehicle go faster.
Since Being now spending some of my summers in Reno I decided that the smart money move ended up patronize the so-called local casinos that cater towards local population rather in comparison to tourist casinos on the strip. Encounters greater difficulty here being that the shrewd locals were receiving superior reward cards effectively better over deal from the stupid tourists who patronized the strip.
…
Online Roulette System – How To Put In And Play Roulette Online
It is easy start off playing and initiate winning. The contraptions do is search a great online casino that you will need to join that provides a ton of slot games that you like. After you find one, it is a two step process you need to start playing and being successful.
at slot machines #3: One place where you won’t find worth it paying machines is through the table gaming titles. This is because the table game players typically spend more money at the casino then slots players, and the casino does not want them being annoyed in the sounds of machines investing. Remember you’ll find the bad paying machines around the table games.
It’s really too bad I didn’t find the Hanabi Full Screen Skill Stop Slot Machine sooner, because at first I was searching for the Best Pai gow poker that dispersed money. Seriously, it didn’t even dawn on me that everything had switched over in order to those SLOT ONLINE electronic tickets until about three months if we started venturing out. Just goes to show you how much he was winning. It’s nice find out that these Antique Slots give you tokens in order to that old time appeal to it.
Here tend to be a few good data SLOT CASINO for choosing best online casino slot action. First, all of the establishments provide you with a first deposit bonus, so make sure you play them. You be obliged to read over the rules and regulations very carefully, because some with them are much easier to collect than additional. This is just “Free” money which are giving you, so don’t screw up.
It’s really too bad I didn’t find the Hanabi Full Screen Skill Stop Slot Machine sooner, because at first I was searching for the Best Slot machine games that dispersed money. Seriously, it didn’t even dawn on me that everything had switched over towards the electronic tickets until 3 months when we started went. Just goes display you what amount he was winning. It’s nice realize that these Antique Casino wars give you tokens to relinquish that old time suit it.
Mr. Robot – Take into account if you’re planning on using bots to try and boost traffic to your web server. If 4 slots are taken by bots and it’s a 12 slot server you’re only leaving 8 slots for real humans. Try to keep the server slots equal in shape to simply how much bots you are planning GAME SLOT to use (if any).
The Osbournes 5-reel, 20 payline video slot depending on the award-winning show on tv. It was released in September, ’07. The Osbournes accepts coins from $0.01 to $0.50, and also the maximum connected with coins that you just bet per spin is 200. Physical exercise jackpot is 15,000 cash.
Once you have chosen the kind of slot game you are snug with, phase 2 is to choose a machine that you think have the actual chance of letting you win. Here is the key tip: It is not so much the kind of game you select. To choose a winning machine, you need to pay more attention to how administrators manage the machines.
…
Casino As Well As Strategy
It will deliver you a physical experience of poker adventures. Most of the games are listed in video version these days. Some of one of the most popular games are: Omaha Hold ‘em, Texas Hold ‘em, Seven Card Stud, Blackjack, entire world Series of Poker event, and Caribbean Stud Gaming.
Wasabi San is a 5-reel, 15 pay-line video slot machine with a Japanese dining theme. Wasabi San a exquisitely delicious world of “Sue Shi,” California hand rolls, sake, tuna makis, and salmon roes. Several Sushi Chef symbols on the pay-line create winning combining. Two symbols benefit $5, three symbols pay out $200, four symbols shell out $2,000, several five Sushi Chef symbols pay out $7,500.
Now, GAME ONLINE SLOT below are secrets to be able to win slot tournaments whether online or land dependent. The first thing is to just how slot machines work. Slots are actually operated by random number generator or RNG along with that is electronic. This RNG alters and determines the outcome of the game or mixture thousand times each second, the problem.
Celtic Crown: Just this thought it couldn’t have any better. Lose yourself from the SLOT ONLINE charm and mystic among the Celtic Crown bonus video slot vehicle. Free spins are triggered with 3 a lot more golden harps. The Princess feature is triggered when 2, 3 & 4 reels display the Princess symbol.
In order to cash out your winnings, you should try to chalk up points by wagering on certain games, ie slot machine games. It is possible november 23 GAMING SLOT GACOR up to $2,000 with $100 personal cash and $100 casino cash playing roulette and also certain strategy. I have done this.
Franken Financial resources are a 5-reel, 20 payline video slot all about a mad scientist in his “spare parts” laboratory. Produced by released in YOLANDA 77 , 2005. Franken Cash accepts coins from $0.01 to $1.00, and the maximum regarding coins you actually can bet per spin is a couple hundred. The maximum jackpot is 2,500 coins.
There are many different companies. The most popular ones are Scalextric, Carrera, AFX, Life Like, Revell and SCX. Sets for these makes can be purchased from hobby stores, large dept stores and online shopping sites including Ebay and amazon. Scalextric, Carrera and SCX have the widest regarding cars including analog and digital leaves.
…
Fun Slots Offer Far More Than Fun!
Slot cars also appear different lengths and widths. The smallest size is HO or 1:64 scale. Originally they were made for inclusion with model railways today these little cars tend to be fast and in addition have some amazing track designs. The next size up is 1:43 scale and its designed for the younger racer with many fun features and character cars. The 1:32 scale is handy size car for racing at home and luckily there is a wide associated with sets. Most significant benefit size car is within the 1:24 and is also commonly found racing at slot car raceway dance clubs.
SLOT ONLINE However, purchase follow my advice, and check out the maximum chance of clearing preferred online slots deposit bonuses and actually making an income before you’re done.
If completed with choosing a casino, its time to play. Slots are one of this can be done to play since quite simple have complicated rules nor does it require solutions to win. Various other words, a gambler will just have to depend on his good luck, if there is any.
Do not play utilizing slot machines that are near on the table buffs. The machines that surround choices said for you to become the least paying units. The casino executives do not keep high paying machines surrounding the table players because put on weight a associated with table players getting attracted towards them.
Bars & Stripes can be a 5-reel, 25 pay-line video slot that has a patriotic American composition. There is plenty of red, white, and unknown. The colorful graphics would be the Statue of Liberty, hot dogs, apple pie, cookies, and a mouthwatering Thanksgiving turkey. Bars & Stripes accepts coins from $0.01 to $1.00, and optimum number of coins you can bet per spin is a couple of GAME ONLINE SLOT . solo.to/yolanda77 is 50,000 cash.
The table version of Poker will be the best. The various versions of poker are on hand as a table game and purchase play free games to develop your skill so you are GAMING SLOT GACOR ready in order to on other players. May abundant poker games available all period for all skill levels as well as many Free-rolls, Tournaments and High-Roller tournaments. A genuine effort . a regarding money with regard to made playing online poker and who knows, might have even win yourself a seat attending the WSOP festival. The table bet on poker comes available in download, flash version and some live dealer casinos.
Play accurate slot brewing system. Consider your goals when deciding which slot machine game to play. If you want for a major jackpot, are progressive slot machine. Progressives pay a large jackpot, but pay out smaller amounts than regular machines on other knocks. If your goal is to play for a lengthier period of time, lookup slot machines with low jackpots or a higher pay table on low level hits. A pay table tells you the way much device pays for everybody payable selection. The lowest paying combinations fall out the frequently.
Lucky Charmer – This online slot is most commonly known for good bonuses. These items see a second screen bonus feature. You 3 musical pipes, and when you get to the bonus round, the charmer plays your choice. But, to activate the bonus round, you end up being able to kick the King Cobra at the 3rd pay-line.
…
How Opt Online Casino
Also, if you’re a occasion player, try having practices first before betting real price. In both online and traditional land based casinos, there are free of charge games and fun modes which a new player may use for clinic. Slots may be a timely game an individual need to settle on strategies for the product if you are someone to have better and a lot more satisfying slot games.
GAMING SLOT GACOR It is even suggested that you play always with the particular bets. There are some machines that require you to place a maximum bet so in order to will become eligible to a jackpot. If you do want to have good chance at winning the jackpot, be particular to bet the every time you play provided which can afford it.
YOLANDA77 are popular games in the online and real world casinos as there are a believe — they’re bright, colorful and simple to play. But I’m in order to take a glance at your odds of in these games.
This Wild West themed casino started their business in ’07. With the help of Vegas Technology in giving the best gaming experience for their players.
It’s almost a dead giveaway here, except for the fact that the R4 DS comes in it’s own R4 DS Box. But you’ll discovered that once you open the box, the contents on the box are identical to the M3 DS Simply, you’ll get specifically the same light blue colored keychain / carry case which comes with the M3 DS simply. You obtain everything you need, straight out of software program. This includes the R4 DS slot 1 cartridge, a USB microSD Reader / writer (and this actually allows you use your microSD as the USB Drive) as well as the keychain GAME ONLINE SLOT carry bag and the application CD.
The credit of initiating the casino game in United States goes to Mr. Benjamin Bugsy Siegal. He started a Casino in Vegas in morrison a pardon 1940’s. Binion Horseshoe, Stupak and Benny also added their contribution to the Bugsy era and begun to build Sin city as around the globe today. Online casino can be very important to the gambler. SLOT ONLINE They can’t put themselves away online casino. Additionally became an enthusiast of online casino after i saw it.
As what their name implies, Millionaire Casino is the highest quality casino for players that wants in order to treated as being a millionaire. And it will surely start in giving you their wide variety of casino games that workout from. In conjunction with every games, you may go through the a feeling of “playing authentic thing” with fine graphics and great sounds. Your thirst for online gambling will surely fill up in Millionaire Casino.
…
Games – Which Would Be Easiest To Play
If performing play a progressive game, be selected play the actual number of coins to be able to qualify for that progressive jackpot. If you play a smaller amount, you will win a large amount, but is not the astronomical amount you can win with no progressive collection.
Experience the exciting sounds of the casino in your home the actual Crazy Diamonds machine SLOT ONLINE save. This is a replica on the larger scale featuring the real-life sounds of the casino combined with jackpot light that flashes and the convenience of a bank preserve your gold coins. By the way, this video slot will take 98% of coins made the worldwide.
There are three main reasons you should prefer playing online; better deals of the casino to suit your action, a good many others multi-million dollar jackpots GAME SLOT plus more tournaments.
The principle in playing slots is temperance. Be contented in order to win. Don’t continue playing and betting and making use of the money you’ve got won. Certainly you’ll lose much more use all of what experience won. The RNG is wise not to let you win undoubtedly. Remember that it changes the combinations a thousand times you will find many second. Also, if it’s not necessary any coin to use, stop.
Speaking of events, the Twin River RI casino is host to many events all year round. A 29,000 square foot event arena is often filled by some famous headline entertainers. The center hosts several live entertainment and did very around the past year. Can be plenty of music and acting occurring at Twin Rivers Casino. Additionally, the facility is SLOT CASINO also available for banquets and special occasions like weddings and business conferences.
#1: They’re Simple. YOLANDA 77 . sit there and stare at a method card every 5 minutes, or make sure to try and make up using the information cards have already been dealt in a poor attempt at card no person likes to. You just spin the reels and hope obtain lucky. And if you just don’t? You spin them again.
Apart of the single payout line in the of the reels, may find more than a single pay lines, every pay line to do with a separate coin dealt with. The symbols stopping on the particular pay line decides the win of a player. The common symbols are bars, cherries, double bars and sevens.
…
How To Backup Ps3 Games
Experience. Clicking a button instead of pull a lever. Otherwise, online slot machines are just like live casino video casino poker. The promise of the massive jackpot is preserved–and sometimes increased by the exponential demographics of the online market place.
It is seen as a fairly simple process. You need a computer with online access. A rather fast connection is always best. Next, establish an account with one of the online casinos. Lastly and I would suggest the most significant is for one to have some interest in the game of roulette. It makes it easier to learn and trainer.
There tends to be no real step to this doubt. When playing Blackjack to be able to to decide when to be able to another card (HIT), the best time to stay along cards (STAND), when to double your bet some other choices, agreed to players amongst people.
Slot machines are one of the attractions in on-line casinos. With these machines, the player need cease an expert to GAME ONLINE SLOT win. He does not ought to be capable of strategies or math to generate the odds in his favor. Slots are played purely on luck and simply about anyone who is of legal age can get involved in it. Today, free video slot games play online and could be accessed from amazed to know any gaming websites on the web. These games may be played with real money or simply for fun without money found.
If you truly desire to aren’t able to win at slot machines, the most crucial thing you have to learn is money conduite. While you are actually playing, it is crucial that you know where you stand money wise. For this reason I suggest begin playing some free slot game. link.space/@java189 of larger online casinos such as Casino King provide many free slot machines for a person to practice. Its going to then record your contribution and earnings on more recent digital type display escalating exactly likely to when are usually SLOT ONLINE playing with real savings.
It GAMING SLOT GACOR is absolutely easy to start playing along with winning. The contraptions do is search to online casino that you prefer to join that owns a ton of slot games that you like. After you find one, it became a two step process before you could start playing and getting.
Scatter symbols can also be used to substitute pictures and two or more could earn a player free operates. If three to five scatter symbols are used then approximately fifteen free spins are awarded.
…
Play Online Slots A Number Of Slots Tournament
Online Slots Strategy Three: Double your. There numerous types of online casino wars that offer double the jackpots. Double is so much better when compared traditional winnings, so have to take advantage of it. In case the machine pays double, you are not to be able to have shell out double for the bet, we can sure have the opportunity to get double the payout.
The amount you need to have to pay depends on the regarding payout device gives. Really are millions nickel machines and five dollar generators. The choice that type perform depends an individual. Of course, the bigger payout, larger fee. Free of charge slot machine games play online, noticing not be charge a fee. These free slot machine game games are fashioned to familiarize the beginner or people who have not really played any machine. Publish will have more enable these learn in respect to the combinations as well as the payouts. After a certain risk free trial period, the guitarist may already wager for certain money. For the people who simply need to take advantage of the excitement brought on by slot machines. They can just play for free anytime besides. With significant number of free action online, they’ll GAMING SLOT GACOR never out of date of programs.
With the growth of the online gaming, it’s going without praoclaiming that slot machine were rapidly adopted and also have created strong presence for them online. Presently, it is pretty possible to play spectacular slot games using the web.
First, you need to consider the fact that you can enjoy these games anytime and anywhere well-built. There is that comfort factor in that room that entices people to work online get started playing. Provided that you have your computer, an internet connection, credit score or debit card with you, in order to set and able to play. Implies you can this in the comforts of the home, inside your hotel room while on business trips, and even during lunch hour at your spot of show good results. You don’t have to be anxious about people disturbing you or getting into fights and dealing utilizing loud musical. It is like having your own private VIP gaming room in the home or anywhere you may be in the world.
The associated with winning the are subject to luck no element can influence or predict the upshot of the games. Bingo games are played for fun, as no decisions are necessary. However, there couple of essential tips that make a better chance to win sport. Playing one card at a time is suggested and banging should be avoided while dabbing. A paper card with lower number should be selected. This has more possibility of getting tinier businesses closer together. In Overall games, it is suggested that you come out early and earn the first set made. It is essential to be courteous and share the winning amount GAME ONLINE SLOT one of several partners. Ideally, the chances of winning are when you play with fewer subscibers. Some even record their games you simply trying out some special games. You could dab.
With English Harbour Casino bonuses, the eyes will surely pop away. They are giving off 100% match bonus SLOT ONLINE to get up to $275 for first bank. And for at the deposit of $100 it is avail this bonus.
In my view, internet casinos bonuses are especially suited for slot players because they’ll meet the requirements very so quickly. Its like having an extra $200 perform free to the house.
First off, online slots offer all of the fun and excitement of live slots but throughout the comfort of one’s own home. You don’t always be waste along with money travelling all means to an out of town on line casino. Actually the most responsible thing about professionals that are able to play if you want for as long while want. Which means you don’t in order to play once you possess a 3 hour block liberal to play.
…
6 Gambling Tips Each Individual Should See!
If you are really attached to playing slot machines, additionally you can easily nice to help sign up for casino memberships. Normally, this is free and also it gives you so many benefits such as freebies and also bonuses. Could even have gifts against the casino because earn points on your membership. It is vital another fun way of playing casino slots.
In a nutshell, the R4 / R4i is merely a card which enables in which run multimedia files or game files on your DS. No editing for the system files is required; it is strictly a ‘soft mod’ that has no effect on your NDS in anyway. You just insert the R4i / R4 card into the GAME SLOT, as well as the R4 / R4i software will run.
Once clicking the button for the bonus, an option wheel would certainly pop through to your screen. You will notice that it says Loot and RP. The RP is short for Reward Problems. This means that when you spin the wheel, you may land on special bonus loot anyone may a few reward points as your SLOT CASINO bonus.
Safe Cracker – This is often a great hardware. It offers a huge jackpot of a cool 20,000 coins. And, https://linkfast.me/java189 can bet within the range of quarter to $5 as well as the max bet is 3 coins. Obtain win $5000 with merely one spin, positively 3 spins, you will get lucky regarding your whopping $20,000. And, the payouts are offered in mid-range.
You are visiting casinos more and more frequently. You tried cease gambling by promising yourself that would you go anymore, but it never is appropriate. You keep going back towards the casino, whatever the negative consequences SLOT ONLINE .
One for this great things about playing from the internet is its simplicity for mechanics. There isn’t to insert coins, push buttons, and pull deals. So that you can spin the reels to win the prize, it will merely take a click within a mouse button to detect. If you want improve or reduce your bets or cash out the prize to increase to do is to still click the mouse.
Determine exactly how much money and time will be able to afford to get rid of on that setting. A person begin enter the casino, set a pay up your have fun with. Set your time often. Playing at slots definitely addictive can might not notice you already spent all difficult earned money and time inside the casino.
…
How To Win In Competitions
Apart from the single payout line in the front of the reels, lot more than a single pay lines, every pay line to do with a separate coin used. The symbols stopping on the particular pay line decides the win of a farmer. The common symbols are bars, cherries, double bars and sevens.
Slot land – This online casino slot is renowned for great attractive ambience, excellent odds and completely secured financial transactions. And, unlike other sites, it does not require for you to download any software. It’s totally play SLOT ONLINE a good initial deposit of a great deal $100. It includes multiple line slots like two pay-lines, four pay-lines, five-pay lines and eight-pay lines. You might have pretty good chances to winning money here.
Once we get everyone setup with Casino chips GAME SLOT the game commences and so it usually takes about 3 to 5 hours with regard to to take home some loot. In the meantime, we have a waitress who comes by and gets these Poker Players drinks, whether it is water, soda, or adult beverages inside the bar. Yes, just identical to the casinos and ways in which we all look in internet marketing is if we’re likely to lose money, we might lose it to additional instead in regards to a casino.
Upon realizing that the machine is an excellent slot, do not place big bets still. You need to conduct a bankroll test first. Read on for some tips a person simply should consider when performing a bankroll check out. If the machine is giving over 50% much more profit, then leave that machine which will help prevent playing by using. Chances are, the spin price you you a big loss. Content articles have anything near comparable thing amount to 49% of your money and profits, hand calculators stay and play with this machine one more time. That machine is essentially the most a good machine is let you hit a big jackpot today.
Bingo-The bingo room includes capacity of accommodating 3,600 people. is scheduled twice almost daily. Apart from the regular game some big money games like Money Machine, Money Wheel, Cars, Crazy L, and Crazy T etc might also be played. Usual non- smoking sections where people with kids may play too.
Another consideration is the payout for this machine. The right rule of thumb is actually a machine has a top-notch payout then you will win less smaller payouts. A unit that features lower payout will hit more often but you might not get that million dollar jackpot. Depending on whether you are wanting to play for countless years on a budget or to be able to “go for broke” to attempt to hit the big one, consider the maximum payout of the machine SLOT CASINO . If the jackpot is only 500 times the coin value or less they will pay smaller amounts more often and a person stay playing on a relatively small budget.
Casinos place good machines in these places purely because want to draw in more targeted traffic to play slots. It is a fact that when passersby hear the happy cheers and victorious yelling of slot winners, others will be enticed to play so they will also win at slot machines.
…
Why Online Slots Are Better Than Live Slots
Playing free slots is a great way to get aware of the hobby. Beginners are exposed to virtual video poker machines wherein they are able to place virtual money location the machine to play mode. The goal is basically to hit the winning combination or combinations. It really is primarily intended for practice or demo programs. Today, online slots are a far cry from its early ancestors: the mechanical slot machine. Whereas the mechanism of your slot machines determines consequence of the overall game in the past, currently online slots are run by a program called the random number generator. Free virtual video poker machines operate training can actually be programs as well.
Be sure to SLOT ONLINE set reasonable goals. Supposing you’re willing to risk $200 on your favorite slot or video poker game. It’ll be wishful thinking to want to turn $200 into $10,000, but you possess a realistic chance to turn $200 into $250, would you 25% gain in a very short time. Where else can you get 25% on cash and have fun doing who’s? But you must quit as soon as this goal is achieved. On the other guitar hand, deals to establish your $200 stake last for three hours, are 25-cent maybe 5-cent navigator. Stop at the end of the pre-set time period, it doesn’t matter if you’re ahead or hiding behind.
Slot tournaments can either require a fee or “buy in” or undoubtedly freeroll champion. Freeroll is casino jargon for a 100 % free tournament. Free slot tournaments are that would bring in new real cash players. Totally https://solo.to/java189 require participants to opt-in at a dsl casino. Around holidays a person find freeroll tournaments possess large affiliate marketer payouts. There are also online casinos offering smaller weekly freeroll matches. The tournament itself will not set you back any money, but to begin with provide accurate contact information to GAME SLOT play.
You can get to pay as little as $20 bucks, but the larger replica banks will run about $80. Each the actual first is a bit different among the others, but their made of doing the same thing: keep hold of your change and take money from your friends. You have to treat them like arcade games within your home.
Experience the exciting sounds of the casino in your home with no Crazy Diamonds machine lending institution. This is a replica on the SLOT CASINO larger scale featuring the real-life sounds of the casino combined with jackpot light that flashes and the actual of a bank conserve your cash. By the way, this slot machine game will take 98% of coins made the world over.
Others are convinced if a product has just paid out a fairly large payout that it does not payout again for a period. Who knows whether any within the strategies do work. Having a lower for certain is if there is any strong indication they do, the company will soon do what they can alter that.
Although there are no exact strategies that will clearly nail you the win in playing slots, here are some tips and methods that will guide you in a person’s chances of winning. If you use this tips every time you play, you can plan to get more profits in the future.
…
Bonus Slots – Getting For The
There are legion benefits in playing slots online. One, it is cheaper. Two, you don’t need to drive yourself to the casinos and back home. Three, there are many great offers which you can enjoy in many online gambling establishments. Upon signing up, new registrations may be able to acquire freebies and sometime an initial amount anyone personally bankroll. Fourth, online slots are very simple to take. Spinning is just just a few a mouse click all period. You can select pay lines, adjust your bets, and spend using only your duck.
Invite your pals when you play. Could be more interesting. Besides, they will be one particular to remind you in order to not spend whole money. As soon as you say hello to the casino, think positively. Mental playing and winning attracts positive energy. Enjoyable because you are there perform and take pleasure with. Do not think merely of winning or maybe your luck will elude the person.
In video game you get what is called a Spider web feature. Is definitely activated as soon as the symbol appears on reels two and four SLOT ONLINE and also places must be at the same time. Everyday activity the video slot goes wild and your changes of obtaining high-payouts are doubled because of the many pay line merger.
There are no exact secret methods teaching how to win in slot trainers. However, there are some secrets on how increase the likelihood of winning. One method to increase the chances of you winning large number of prizes is recognize how to choose a machine which gives the best payout. These machines are usually installed in places near coffee shops, snack bars, winning claims booth, too as in places fo you to see others passing by.
It’s really too bad I missed the Hanabi Full Screen Skill Stop Slot Machine sooner, because at first I was searching for the Best Video poker machines that dispersed money. Seriously, it didn’t even dawn on me that everything had switched over to electronic tickets until 3 GAME SLOT months after we started intended. Just goes to show you how much he was winning. It’s nice find out that these Antique Slot machines give you tokens in order to that old time ask it.
By trustworthy, it doesn’t only mean someone who won’t swindle your dollars spent. Trustworthiness also means a company who thinks of the regarding their folks. Do they offer multiple payment and withdrawal options? Will someone help you out or answer your questions if and when you SLOT CASINO want it? Are you really getting paid if you win?
You must choose perform a machine that has lesser winning combinations to be able to during your spins. The lesser the combinations, the better chances of winning more personal savings. Although the jackpot amount is lesser, you will still win big as most of these kind of machines have better odds in winning.
Remember, not every machines offer the same jackpot amount what’s exactly going on the purpose of which the actual of playing in all of the machines is not the same. Most popular versions the jackpot amount more is the potential losing dollars. Therefore, if you do dont you have the skills of recreation and wouldn’t like to lose cash unnecessarily, it is best to avoid playing online that offers high jackpot amount.
…
Introduction To Your Online Slots
The bad-paying and well-paying slot machines are usually located next to each more. Are you not being successful at one machine, the next one has a tendency going generate better returns. Have an open eye for people like us who never leave handy they are playing – they may be waiting for your pay, or they possess a loose machine and stay on winning. Would certainly think like to attempt out that machine and realize how well it is employed by you. Probably the most important thing to remember is to insert the $5 bill into the device – i recommend that you place optimum bet towards the first spin, as in the neighborhood . where most jackpots are won.
Casino games are favorable. It depends on chance and luck. Another crucial thing is regimen. Applying the right means by which to play the game can prove to be functional SLOT ONLINE . There are several regarding casino gaming. One of the popular games offered by the online as well as the offline casinos is Live dealer roulette.
When an individual playing involving bonus slots, you can know that less one is more and purchase expect good quality thrill while playing the games. Will bonus slots are if anyone is who do not worry on the line payment. There can be games that have 2 much more bonus terms. One of the three bonuses can be good while others may not be that good and you could possibly not similar to it. To make certain anything of this particular sort doesn’t happen, you can choose a personal game that recently one bonus feature option that such as. Choosing bonus slot games with uninteresting bonus features will just waste your period and efforts that you simply put into playing the overall game.
Some rewards are larger, such as complimentary trips to a buffet an additional restaurant in the casino. Should the place an individual playing at has a hotel, you might get a discounted room rate (or even free nights). If you’re a really high roller, could possibly get airfare or shuttle service to and from the casino.
There several benefits in playing slots online. One, it cost less. Two, you don’t be compelled to drive yourself to the casinos and GAME SLOT back home. Three, there are many great offers which you can enjoy in many online gambling establishments. Upon signing up, may be able to acquire freebies and sometime an initial amount for you bankroll. Fourth, online slots are very simple to enjoy. Spinning is just a few a click of the mouse all the time. You can select pay lines, adjust your bets, and spend using only your personal computer mouse.
Players must battle Doctor Octopus as a result are placed in difficult moments. Playing as the super-hero you must save the lives of your innocent victims before down the road . move on too the following spin. Players will face all the regular criminals within the comic book making it even more enjoyment to take pleasure in. This action hero has special powers like climbing walls, shooting out his very own spider web and they could sense financial risk. He was bitten any radioactive spider and this is how he took over as popular super-hero Spiderman.
The other they may offer you is the chance to play for no cost for one hour. They will give that you a specific number of bonus credits to apply SLOT CASINO . If you lose them inside your hour your trial has finished. If you end up winning in the hour you should be able to keep your winnings but by incorporating very specific restrictions. You will need to browse the rules and regulations attentively regarding this. Each casino has its own set of rules on the whole.
Online Slots have been a good option for individuals just go browsing to take part in. Lots of things come and go in order with the slot machine as an edge technology develops.
…
Gambling Online Flash Games – Betting On Fast Fun
The chances of winning recreation are based on luck simply no element affect or predict the results of the game. Bingo games are played for fun, as no decisions need to be made. However, there are some essential tips that present a better to be able to win video game. Playing one card at some time is suggested and banging should be ignored while dabbing. A paper card with lower number should be selected. This has more possibility of getting the numbers closer together. In Overall games, it is suggested that you come out early acquire the first set released. It is essential to be courteous and share the winning amount on the list of partners. Ideally, the chances of winning are when you play with fewer members. Some even record their games if they’re scams trying out some special games. It is simple to dab.
Play fresh slot machinery. Consider your goals when deciding which slot machine game to play. If you look for a crucial jackpot, are progressive video slot. Progressives pay a large jackpot, but pay out smaller amounts than regular machines on other knocks. If your goal is perform for a prolonged period of time, look for slot machines with low jackpots plus higher pay table on low level hits. A pay table tells you much device pays per payable combination. The lowest paying combinations go out the frequently.
Also, if you find yourself a first time player, try having practices first before betting real riches. In both online and traditional land based casinos, there have the freedom games and fun modes which a gamer may use for procedure. Slots may be an easy game however, you need growing strategies for the product if knowing to have better but more satisfying slot games.
The traditional version with this game end up being modified by simple changes to become more interesting, and as attractiveness of Checkers increased, different versions of this specific game showed up GAME ONLINE SLOT . Some of these variants are English draughts, Canadian checkers, Lasca, Cheskers and Anti-checkers.
Your choices have an important impact inside your chances november 23. The Blackjack strategy chart offers players a regarding the best choices in the games – choices are actually supposed to enhance their chances to attain. But even when making the best, most accurate choices in online game – a massive part of winning still involves opportunities. You can make the best choice, in case your dealer displays better luck then you – realize that some lose. You can also make waist decisions, howevere, if lady luck is in your corner you will win.
Fact: Dedicated players hold experienced that quite commonly a winning combo comes by, short of 1 correct icon. But in long run, it SLOT ONLINE under no circumstances suggests how the winning combination is along the corner. The appropriate misses tend to be simply another random combination.
Being a zealous sports bettor and market enthusiast, I couldn’t ignore the correlation that binary options has with gambling. In this form of trading happen to be given two options opt for from from: up or down. Is the particular security, currency, or commodity going to flex up or down the actual world respective stretch of time that you’ve selected. Kind of like: are the Patriots going to win by 3 or? Is the score going to become higher or lower than 43? https://linkfast.me/java189 . see where this GAMING SLOT GACOR heading to right?
50 Lions Slot can be a 5-reels penny game, along with other although the coins in this game could be different denominations you are able to place a wager for as low as 1p.
…
We Play Bingo – Don’t You Have To? Bingo Tips Advice And Strategy Guides
There are wide ranging benefits in playing slots online. One, it will cost less. Two, steer clear of need to push yourself towards casinos and back the house. Three, there are lots great offers which perform enjoy need online gambling houses. Upon signing up, new registrations may skill to acquire freebies and sometime economic crisis amount a person bankroll. Fourth, online slots are very simple to play with. Spinning is simply a matter of a click of the mouse all time. You can come up pay lines, adjust your bets, and cash out using only your personal computer mouse.
There are three significant reasons you should prefer playing online; better deals to the casino with regards to your action, a lot more SLOT ONLINE multi-million dollar jackpots and a lot more tournaments.
In the beginning, I really didn’t know what to be able to for, but this new little adventure not could be more expensive than exactly Hanabi Full Screen Skill Stop Video slot itself. You’re aware all ideal Slot Machines are wired at the casino with under wires and everything else, immediately? Well the good news is these are already set about be tried. link.space/@java189 have to do is this into a wall can be would cash lamp along with the vacuum for all those sweeping.
A system that isn’t user-friendly can take all exciting process out of your game. Rather than just putting your mind into winning, you become torn between winning and finding out how to run the technique. The best way to get with this problem is try first the free version of your games you would like. This way, by the point you sign-up, you know what you’re getting into.
Players GAME SLOT throughout the world will appreciate all the awesome features that 3Dice offers their players, out of your chat room, to the daily free tournaments all those players. It does not stop there because while play you’ll get rewarded with loyalty and benefits according to your VIP status.
The slots are hosted by exciting workout casinos online, so one more no compromise on the graphics and also the speed of access. Even slot the guitar player chooses gets underway with 50,000 credits, enough that you sustain for hours. What’s more, every time you get back the site, the credits are renewed!
Black king pulsar skill stop machine is one of the many slot machines, which is widely used by the people of different ages. This slot machine was also refurbished SLOT CASINO inside factory. Had been thoroughly tested in the factory and after which it was sent to be able to stores available.
There are already a regarding existing mobile slots to choose from. But it is not wise to get the first one someone happens to put your on the job. There are a few things you must know so could maximize your mobile slot experience.
…
Try Your Luck In Popular Casino Table Games
Before anything else, essential bring a hefty income with then you. This is very risky particularly displayed in the public place, so protective measures should be exercised.
If you hit from about the equivalent amount of money to 49% profit, then discover play again with exact same machine. Your chances of getting the jackpot are greatly high as it might be a “hot slot”. For example, if you commenced spinning for $100 as well as have about $100-$149 as profit, this is an indication that the slot you are playing is something that has the best agreed payment.
#1: They’re Simple. You should not sit there and stare at a technique card every 5 minutes, or make sure to try and continue up information and facts cards had been SLOT ONLINE dealt in the poor attempt for card that enjoyable .. You just spin the reels and hope an individual lucky. And when you in no way? You spin them again.
JAVA189 are the more favorite spots in the casinos. The combination’s shown on the reels make the adrenaline of both player and watchers surge extra tall. It gives a good feeling being thrilled and satisfied primarily if you wins the jackpot. These days, winning at slot machines is not brought by mere luck but by extra effort exerted along with player. Indeed, lucky charms are not as much effective at slot machines. If you are a slot player, you might need strategies SLOT CASINO acquire more from the fun.
It can be a good idea for a person to join the slots cub at any casino that you go for. This is one method you can lessen amount of money that you lose because will possess the to get things on the casino free for the individual.
If you are an avid player in poker. You should always keep abreast of developments to make the in favor of some company or slots. Therefore, we decided that you’ll have enjoy the good news we desire to offer you. Who said that to win the jackpot, you ought to spend time? But it is able to be win it in only a seconds, and we simply n’t have any words, that is definitely very purchasing.
Playing a slot machine is simple. First, you place your hard in device. Today’s machines is going to take all denominations of expenses. You can put because much money as consideration. This money tend to be converted into credits may easily be avoided GAME SLOT be used for the product.
Try to go to your favorite search engine and rummage around for slot machine games completely. You’ll be surprised at the number of search upshots of websites and pages which permit you to enjoy this game to the fullest without risking certain dollar. So for those out there who chooses to try out this game but are scared to lose hard-earned money, you surely try playing it about the web.
…
Slot Game Strategies To Convince You Win Big
Avoid machines which are placed beside a hot slots. Most likely, these machines are cold slots because casinos don’t usually place two good performing machines adjacent to every other.
This article summarizes 10 popular online slot machines, including Currently being the GAME SLOT Reels Turn, Cleopatra’s Gold, Enchanted Garden, Ladies Nite, Pay Land!, Princess Jewels, Red White and Win, The Reel Deal, Tomb Raider, and Thunderstruck.
Why do people such as the free Cleopatra slots game? https://linknbio.com/java189 has a lot to do with the beautiful graphics, the music activity and recognition of the Egyptian history that’s incorporated into it. After all, harvest know who Cleopatra was? In her day, Cleopatra was the profitable woman in the world.
Casino games are favored. It depends on chance and luck. Another crucial thing is principle. Applying the right technique play the overall game can convince be healthy and balanced. There are several SLOT ONLINE types of casino gaming applications. One of the popular games presented by the online as well as the offline casinos is Live.
There is another feature that is not available in the slot machines of industry. You will get a sound while having to pay the coin in the device. This will make you feel that professional a real casino.
Progressive slot games mean that these games are regarding the other machines within the casino. Non-progressive means that the machines aren’t connected to one another. The implication would likely odds are definitely even for that progressive construct.
Generally, truly calculate unearth per spin so you just can play in video poker machines in accordance to SLOT CASINO monetary. It is fun perform in a slot wherein you get at least 10 moves. Learning how to examine a machine is means to boost profits.
It’s almost a dead giveaway here, except for that fact that the R4 DS comes in it’s own R4 DS Box. But you’ll discovered that once you open the box, the contents belonging to the box is the same to the M3 DS Simply, you get replacing light blue colored keychain / carry case which comes with the M3 DS simply. A person receive everything you need, straight out of brother ql-570 comes with. This includes the R4 DS slot 1 cartridge, a USB microSD Reader / writer (and this actually allows in order to definitely use your microSD as the USB Drive) as well as the keychain carry bag and confidential details CD.
…
Advance Online Networking – Getting Others To Read Your Emails
There are even slots that are hooked up to main computer with several casinos providing the players and their money. These mega slots pay out huge payoffs and constantly worth a few plays with the expectation that you’ll get exceptionally routine.
The crucial thing keep in mind when you want to save is to strictly follow your slot bankroll low cost. Before sitting down in front of the machine, you have to first generate a certain expense plan. Decide on the amount you are willing risk in losing and also in winning. Playing slots can certainly be attractive. Winning one game will always seduce in order to definitely play as well as before kind of person it, all the SLOT ONLINE profit also bankroll could be over.
Progressive slot games mean that these games are attached to the other machines within the casino. Non-progressive means that the machines are not connected one to the other. The implication would likely odds tend to be even for that progressive assemble.
GAME SLOT #1: They’re Simple. https://link.space/@lele189 sit there and stare at something card every 5 minutes, or attempt to try and keep up performing what cards have always been dealt within a poor work for balance card no person likes to. You just spin the reels and hope obtain lucky. And in case you don’t? You spin them again.
Are you ready yet another good toy machine bank which includes realistic sounds when you hit the jackpot? The Burning 7’s toy slot machine uses batteries to determine when you’re the lucky champion. The bell rings and the light flashes a lot of SLOT CASINO the coins you have put in the bank will fall the bottom this hit the winning combination.
The best performing slots are often located all of the casino’s hot spots. Hot spots are where the hot slots are almost always. When we say hot slots, including machines designed to be super easy to wipe out. Hot slots are often located in areas which includes the winning claims booths. Casinos place numerous machines here to attract and to encourage tourists to play more when they hear the happy cheers of folks that are lining up in the claims booth to win back their prizes whenever they play slot machines.
First, set yourself perform. Be specific to have earnings. They do not receive vouchers in playing slots. Then, set an amount to invest that day on that game. When you consumed this amount, stop playing and come back again next evening. Do not make use of all your take advantage just one sitting and setting. Next, set period and alarm. Once it rings, stop playing and fall out from the casino. Another, tell you to ultimately abandon gear once won by you the slot tournament. Do not be so greedy thinking that you want more advantages. However, if you’ve have money in your roll bank, anyone then may still try other slot computer games. Yes, do not think that machine your own had won is lucky to cause you to be win repeatedly again. No, it will just use up all your money and a person lose a bit more.
If 1 does play a progressive game, be certain to play the utmost number of coins as a way to qualify for that progressive jackpot feature. If you play a smaller amount, you will win a large amount, and not the astronomical amount foods high in protein win that isn’t progressive billiards.
…
Lawyer Marketing: Tv Ads Vs Picture
In land based casinos there can be a service light or candle on surface of the video slot. linkfast.me/lele189 can be activated using the player they will have a question, want to know a drink, need change or has a technical trouble. In order to activate the light the player should push the change button. This particular can set from all the light or candle the bootcamp will blink to give the employee’s realize assistance ought to be needed. The light or candle will automatically blink if it takes a victor. A player should never walk off from a machine with a blinking light it could mean a person a receiver. If you walk away from a blinking light machine you certainly not able to claim the income.
Lucky Shot is a 5-reel, 20 pay-line video slot from Microgaming GAME SLOT which has a golf theme. It accepts coins from 1 cent to 50 cents, as well as the maximum quantity of coins that you may bet per spin is 200 ($100). There are 35 winning combinations, top-notch jackpot of 15,000 coins, scatters (Gopher), up to 18 free spins, or a Gopher Bonus Game. To win the 18 free spins, you be required to hit three or more Golf Cart symbols. To activate the bonus round, you need to have hit three or more Gopher symbols on the reels. Symbols include Gopher, Lucky Shot, Golf Club, Golf Bag, Trophy, and Golfers.
The Liquid crystal display of the Mu Mu World Skill Stop Slot machine game offers high-quality animation graphics as well as hd. User friendly for a eyes therefore you appreciate hours of fun. The refurbishing factory polishes and restores if you like look with the machine to make you obtain a machine which is of top quality. This machine features a checkpoint mechanism which allows SLOT CASINO it end up being user safe and prevents unwanted accidents.
The first electromechanical slot version was invented in 1954. Soon there were other versions of slot machines that have a cent rate, therefore, the number wishing to play in the one-armed bandit is producing. Since then, both casino operators have did start to use more slots brought up, accept checks, tickets, tokens, paper, for impacts in the Slots become expensive. But after some time thanks to be able to casino entice new players have appeared a cent slot printers. As new versions of slots allowed staying put on the web payments more coins, while it will take players would not afford create such large bets, it was decided that minimal value of coins in slot machines was up one cent.
Machines near game tables also have high odds of being cold slots. Bad machines typically be placed here because casinos would prefer to prevent the cheering slot winners from disturbing those you are playing poker, blackjack, various other table adventure titles. These kinds of casino games require a lot of concentration effectively.
If you hit from the same amount of money to 49% profit, then you could play again with that same machine. Your odds of SLOT ONLINE of getting the jackpot are greatly high as it might be a “hot slot”. For example, if you began spinning for $100 and also you have about $100-$149 as profit, wishes an indication that the slot you playing is something that allows the best pay out.
You must know which machine or site is the best for your slot machine game download. Video poker machines are of countless kinds we should confident you of which is the best for you. If you see that you are losing within the machine many time then change the device and commence the next one. Though it is intense thing to do, you’ll find a fresh start again.
…
Getting To Grips With Online Keno
By trustworthy, it doesn’t only mean someone who won’t swindle your moola. Trustworthiness also means a company who perceives the capability of their battlers. Do they offer multiple payment and withdrawal options? Will someone give you some help or answer your questions if and as soon as you demand it? Are you really acquiring paid a person are win?
For people who want perform but will not idea yet how it works and they you can win from it, the online slot machines will donrrrt great help in. Through these games, you end up being able to familiarize yourself with formed games and styles, also SLOT ONLINE as the jackpot prizes, before you play real game fidgeting with real cash flow.
Playing a slot machine is rather simple. First, you place your money in handy. will require all denominations of utilities. You can put because much money as getting into. This money tend to be converted into credits the best be moved to the maker.
Why do people such as the free Cleopatra slots challenge? It probably has a lot to use the beautiful graphics, the songs and reputation of the Egyptian history that’s integrated into it. After all, harvest know who Cleopatra could be? In her day, Cleopatra was the most robust woman in the field GAME SLOT .
(3) Provide you . one of the most effective options for online casinos, the Live Dealer Casino. These are the most interactive version of the internet casino certainly where a live dealer through youtube videos feed from an actual land based casino will greet we. You can interact with the dealer and together with players who may be playing at the table. Live dealer casinos will provide a real casino experience leave your home.
The amount you have to pay depends over a type of payout gear gives. Are usually several nickel machines and five dollar nodes. The choice of which type perform depends done to. Of course, the bigger payout, the larger fee. For free slot machine games play online, you will not be charge a fee. These free slot machine games are intended to familiarize the beginner or those have got not yet played a precise machine. Wholesome enable the particular learn the combinations as well as the payouts. Following a SLOT CASINO certain risk free trial period, the player may already wager legitimate money. For those who just in order to enjoy the rush and excitement brought about by slot machine games. They can just play for free anytime besides. With the huge number of free action online, they will never depletes choices.
Pay Debris! is a 5-reel, 25 pay-line progressive video slot from Real Time Gaming app. It comes with wilds, scatters, up to 12 free spins, and 25 winning combinations. Symbols on the reels include PayDirt! Sign, Gold Nugget, Gold Mine, Bandit, Gold Pan, Lantern, and Tremendous.
…
Are Online Slots Tournaments Worth The Hassle?
So what’s the slot machine tip that’ll make that you simply winner? Stop being LELE189 ! Before you put your money at risk, think about which you wish to achieve, besides having nice. Do you want to play for a particular number of hours, or do you need to win a specific dollar amount, or a variety both?
Their tournament lobby is definitely jumping with action. 24/7 there can be a tournament enjoying a for all players. Every hour, VIP players obtain a freeroll tournament to enter, along with also goes on around the clock. Special event tournaments even more are cause for additional battles SLOT ONLINE .
Second, essential ingredients . o the right gifts right gambling establishment. Not all casinos are for everyone, such that you should select which one best you. Moreover, every casino has a fixed payout rate and you should figure out which payout is essentially the most promising. Practically if you want to money in big amounts of money, definitely choose the casino providing the best payout beat.
Another thing to look for when choosing mobile casinos for slots is if they offer flexible betting capabilities. You should be able to play both high and minimal stakes and not one possibly other. Have got to GAME SLOT also have an understanding of the winning lines, betting tiers and pay patio furniture.
Once you’ve chosen the connected with slot game you are happy with, determine is to decide a machine that choice have the chance of letting won by you. Here is the key tip: It isn’t so much the type of game decide on. To choose a winning machine, you have to pay more attention to how administrators manage the machines.
A system that is not user-friendly get all is often a fun out on the game. Rather than putting your brain into winning, you become torn between winning and finding out how to run the system. The best way to get surrounding this problem should be to try first the free version within the games want to. This way, by the point you sign-up, you know exactly what you’re getting in to.
Speaking of events, the Twin River RI casino is host to many events all through the year. A 29,000 square foot event arena is often filled by some famous headline vocalists. The center hosts some terrific live entertainment and did very around the past year. Considerably more plenty of music and acting SLOT CASINO enjoying a at Twin Rivers Home. Additionally, the facility is also available for banquets and special attractions like weddings and conference meetings.
3) Incredible Spiderman – this but another one the hands down video casino wars that helps make the most of their film tie in. It has three features and You are able to provide some seriously big wins on account of the Marvel Hero Jackpot.
…
Top Great Play At No Download Slots
With solo.to/kagura189vip , children can appraise the time it will take their slot cars to do the track and, in doing so, explore your way the shape with regards to a slot car affects its speed. Kids can learn how wind resistance and aerodynamics can develop a vehicle go faster.
GAME SLOT Save your change in this particular 8.5 inch tall machine bank and you will be amazed at how quickly the money will mount up. The real working handle and a coin return that can be operated manually make slideshow perfect idea for a great gift.
First, look on a greater platform or carousel. The casino should seek the higher payouts pertaining to being visible with most somebody. Other patrons are usually to keep gambling having looked at a person win big.
It is often a good idea for which SLOT ONLINE join the slots cub at any casino that go so that it will. This is one approach you can lessen quantity of money that you lose a person will manage to get things over the casino free for the individual.
Mainly the purpose of playing online slot games will be have money, but how? It’s just like you’re playing the game called Galaxy Balls. All you need is to place all you shouldn’t shapes or symbols in the row. An individual know fully understand on easy methods to play this one, you are able to see a screen by using a row of special significance. Sometimes, you observe this the particular form of shapes, fruits or even numbers within a 2-4 spinning wheels.
Knowledge among the game is critical. Of course it is crucial that it is well known SLOT CASINO the basics of the overall game. You must have some idea on the foundational factor to win. You have to know how these machines operate. You’ve got noticed how these machines produce good and perfect combinations at the first and 2nd reels but fail to purchase a perfect one around the third? Well, this is primarily given that they machines are programmed carried out. The slots have Random Number Generators permit them to determine the outcome every single spin. If you’ve got knowledge on the game, you would know there is no exact timing of this spin as they are all random acts by the microprocessors established in the laptop.
There are two involving slot cars, there will be the analog cars and the digital the kind. The traditional or analog slot cars are people that you might remember in the younger days. This is where it was one car per slot as well as the car for you to stay for the reason that slot for your race.
…
Fun Is Anywhere With Free Slots
Know Your Machine: Sounds obvious, but there are many players who play and after realize they haven’t played the correct of coins for optimum payout!
If anyone might have won on a certain slot machine, abandon that products. There is no lucky slot machine game. Do not be greedy and think of playing concentrating on the same machine after your triumph. The slot will surely force you to lose right after that. Slots are regulated by microprocessors or generators which set combinations randomly.
As a slot player, you need to know when you should change machines so that you can effectively increase your winnings. It is always advisable to change machines should you be current machine is leading you to lose a small number of times. When the happens, undertake it ! move for KAGURA 189 . It is common for casinos to arrange two good slots just about each next. Observing the performance of the machine is critical for each slot machine player. Your duration of your games, a person noticed you might have been any “cold slot”, there can be a high possibility that the machine next into it is a “hot slot”.
Texas Holdem Poker Games Online has enthralled millions particularly over the last decade. A myriad of slot online these players are vigorous in perfecting their play. Though they loose over time, they include the keenness turn into experts. Couple options such lots of adventures amongst players. There are numerous leaks in this game.
RPG or role playing games usually are the kind of game that multiplayer games online are classified by. Here, player assumes the role of the smoothness that they prefer. Each one has their abilities, special powers, items, and weak spot. The goal is to complete the mission given to you with whatever your character may receive.
There are a couple people in which have found when they play online poker they win a degree game slot of money every time, let’s say they win approx 700 dollars while the downswing starts that is after winning the seven-hundred dollars, tend to be offered back to nil.
For anyone out there wondering the requirements perform a game online, well movie luck. A house game online can run on even those computers tested to be active not be so innovative new. So you can still have fun while getting to replace your PC just to play a game today.
Set Your Bank Roll In Advance: Your Playing Strategy end up being set up BEFORE you play slot machines; only gamble whatever you can afford to lose. Going into a casino or online, it’s to be able to lose associated with time and cash. With the adrenalin rush of playing, time and money can go very rapid!
…
Online Party – 6 Steps In Order To Successful Online Party
Be sure to set reasonable goals. Supposing you’re willing to risk $200 on simple . slot or video poker game. It’s going to be wishful thinking to anticipate to turn $200 into $10,000, but you possess a realistic chance to turn $200 into $250, that’s a 25% grow in a very short effort. Where else can you get 25% on the and enjoyable doing this? But you must quit as soon as this goal is achieved. On the other instrument hand, if you’re planning to establish your $200 stake last for three hours, are 25-cent probably a 5-cent machine. Stop at the end of the pre-set time period, whether you’re ahead or right behind.
Mr. Robot – Be the cause of if you are planning on using bots to try and boost visitors to your server. If 4 slots are taken by bots and it is a 12 slot server you’re only leaving 8 slots for real humans. SLOT CASINO Try to keep the server slots equal in porportion to systems bots you’ve planned to use (if any).
Slot machines are the best favorite spots in the casinos. The combination’s shown on the reels make the adrenaline of both player and watchers surge tremendous. It gives a good feeling being thrilled and satisfied particularly if the golfer wins the jackpot. These days, winning at slot machines is not brought by mere luck but by extra effort exerted coming from the player. Indeed, lucky charms are less so effective at slot apparel. If you are a slot player, you have to have strategies obtain more when compared to the fun.
The slots are hosted by essentially the most effective casinos online, so hard work no compromise on the graphics along with the speed of access. Even slot the user chooses gets underway with 50,000 credits, enough to help you sustain for extended time. What’s more, every time you come back to the site, the credits are replaced!
Save your change in this 8.5 inch tall machine bank sign in forums be astonished at how quickly the money will make sense SLOT ONLINE . The real working handle and a coin return that can be operated manually make this a perfect idea for something special.
Goodness, gracious great balls of flame! Okay, it’s not that fantastic, but and also definitely light your grill. Sorry, kind of cheesy what amount can i you are you able to blame me when look at the Fire Drift Skill Stop Video slot. If you just a lot GAME SLOT color red alone and not just played a Slot Machines For Sale in your life, this is able to definitely spice up your house in a heartbeat. November 19 aside though, we get nothing but compliments more than a play and entertainment one of the ways Casino Casino wars offer.
The Mu Mu World Skill Stop Slot Machine does not want any set. All you need to do is simply plug it in even more walks . is ready to use. link.space/@WAK69 is a used Slot Machines that originates from a real casino after being furbished in a factory. High definition tv all solar lights and sounds of the casino that allows you to enjoy an e-casino like atmosphere in the luxury of home. This Slot Machines For Sale comes with warranty of two years for all its features and options except the bulbs.
…
Online Slot Machines Guide To Popular Online Casino Slots
That is correct, understand read that right. You can now play online slots along with other casino games anytime assess right on your hard disk. No longer do you have to wait until your vacation rolls around, or find some lame excuse to tell the boss so that you can get a week off to move over to a number one brick and mortar on line casino.
If you are planning to play, it very best to prepare and know for sure how long you often be playing make certain you will give yourself a financial budget. You should ‘t be willing down the sink a involving money on this particular. It is a form of recreation and also earn for you some finances. However, losing a fortune is not even advisable.
The best slot machines to win are quite often located nearby the winning claims booth. Just because the casinos would in order to attract more players who’ll see other people lining up in the claims booth cheering and talking regarding their winnings.
For people who SLOT ONLINE want to play but don’t have idea yet how functions and they you can win from it, the online slot machines will viewed as great give support to. Through these games, you is actually able to familiarize yourself with diverse games and styles, also as the jackpot prizes, before you play the actual game messing around with real funding.
The principle in playing slots is temperance. Be contented in order to win. GAME SLOT Do not continue playing and betting and making use of the money possess to won. You’ll certainly lose increasingly more use all of what get won. mylink.la/kagura189 makes sense not to let you win needless to say. Remember that it changes the combinations 500 times you will find many second. Also, if to recognise a stunning any coin to use, stop.
There may times and ensure you don’t ride substantial stakes which happens to be good. But what about those when you are only able to do with minimal trades? Should you give up playing fully?
You should be expecting to pay as little as $20 bucks, but bigger replica banks will run about $80. Each is actually a bit different SLOT CASINO of this others, on the other hand made to do the same thing: handle your change and take money away from your friends. You need to treat them like arcade games at your residence.
If you’re really attached to playing slot machines, it’d be nice that you sign up for casino memberships. Normally, this is free use gives you so many benefits such as freebies some other bonuses. Really can even have gifts against the casino when earn points on your membership. This particular another fun way of playing competitions.
…
Online Casinos Could Be Treated As The Training Ground
GAME MENU – A few select this menu, you’re instantly arrive at a regarding all for the game files, homebrew applications, etc. that you may have stored on the microSD master card. You can use the controller pad on the NDS to pick from the file you wish to load. When you are loading a video game for the first time, you might be prompted, after selecting the game, to ensure that you wish to create a save register for the on the internet. This is needed if you need to save you game. Your game saves are stored on exact sneakers microSD card as recreation files themselves – famous . fantastic if you want to delete those games later, to compensate for other files, as are able to copy your save game files to your PC, for future use as you prepare to continue playing that game again.
Some casinos, like those who work in the Caribbean islands, rely more on seasons greatest and fullest. The Bahamas, Puerto Rico and other people are completely booked from November to Spring. During this period even SLOT ONLINE the best players are comped less because casinos will be filed with paying people no matter. In other words, the demand during this era is so excellent a recession doesn’t substances.
Do not use your prize perform SLOT CASINO . To avoid , have your prize at bay. Casinos require cash in participating in. With check, you can get out of the temptation of utilizing your prize up.
#6: You won’t get stabbed in a dark alley by a fellow slots player. Ever been playing Blackjack late at night, tired properly little bit drunk, and “hit” need to have “stood”? Yeah – that person beside you screaming inside your ear is someone not often covered want to meet outside the casino are up and running. Meanwhile in slots purchasing hit the nudge button accidentally, people next to you aren’t likely to care.
Once you have chosen the type of slot game you are snug with, additionally, you will is to a machine that you believe have the actual chance of letting you win. Here is the key tip: It is not so much the associated with game choose. To choose a winning machine, you need to pay more attention to how administrators manage the machines.
Others believe that if GAME SLOT a piece of equipment has just paid out a fairly large payout that you will not regret payout again for a period. Who knows whether any in the strategies really do work. Much less for certain is any time there is any strong indication which do, the manufacturers will soon do public record information can alter that.
Now, let us discuss secrets technique win slot tournaments whether online or land predicated. The first thing is find out how slot machines work. Slots are actually operated by random number generator or RNG which usually electronic. This RNG alters and determines the result of the game or blend thousand times each additionally.
Experience the exciting sounds of the casino in your home an issue Crazy Diamonds machine save. This is a replica on the larger scale featuring the real-life sounds of the casino along with the jackpot light that flashes and the convenience of a bank in order to your coinage. By the way, this slot machine will take 98% of coins made the world over.
…
Is Online Video Poker A Good Solution?
Although there are no exact strategies that will clearly nail you the win in playing slots, here are a few tips and techniques that will guide you in increasing your chances of winning. When you use this tips every time you play, you will have the ability to gain in profits once time had passed.
It is very important that you have self control and the discipline to stick to your limit which means you won’t lose more money. Always remember that playing slots is gambling and in gambling losing is expected. Play only in an amount a person are ready to lose guaranteeing that after losing you can convince yourself that experience paid plenty of money that provided you with quite best entertainment you had. The majority of the players who do not set this limit usually end develop a lot of regrets since their livelihood is ruined a result of a drastic decrease of a slot machine game.
Free winning casino strategy #3 – Most for this table games are worth playing over-the-counter slot machines GAME SLOT . One in particular that sticks out is none other then poker. An individual can find some winning methods on poker and focus the game inside and out can really clog make funds from the casino players naturally.
The more effective slots are often located in the casino’s locations. Hot spots are place hot slots are. Whenever we say hot slots, simple machines developed to be super easy to tune. Hot slots are often located in areas for instance winning claims booths. Casinos place quite machines here to attract and to encourage consumers to play more when they hear the happy cheers of those people lining up in the claims booth to win back their prizes because they play video poker machines.
SLOT ONLINE Why do people like the free Cleopatra slots challenge? It probably has a lot to use the beautiful graphics, the music activity and two strategy of the Egyptian history that’s integrated into it. After all, who doesn’t know who Cleopatra was? In her day, Cleopatra was the profitable woman in the world.
linknbio.com/kagura189 to play if you don’t want expend much money but want to dip your toe into gambling is the slot cleaner. Most of these machines work by putting money into the slot, pulling a lever and then hoping a person simply get three identical pictures. If you do, you win, prone to don’t, do not need to win. It’s rare to win big funds on the slot machine games but chances are you’ll have some luck winning small amounts. You can also find slot machines that push money off a SLOT CASINO ledge.
The advantage is where all these web based casino funds. Regardless of your chances of their victory, final results . is what exactly will you want to keep internet casino profitable through the years because the slightest modifications may possess a dramatic result on your possibilities for the win very well as the edge in each given challenge.
Playing a slot machine is trouble-free. First, you place your money in handy. Today’s machines is going to take all denominations of expenses. You can put in as much money as getting into. This money are converted into credits simply take be used within the coffee maker.
…
Guide To Online Casinos For Beginners
The best performing slots instances are located inside the casino’s locations. Hot spots are place hot slots are. Whenever we say hot slots, these are the basic machines developed to be easy to overcome. Hot slots are often found in areas for instance winning claims booths. KAGURA 189 to attract and to encourage men and women to play more when they hear the happy cheers of nevertheless lining up in the claims booth to get their prizes after they play casino wars.
Always remember the fact that when you play slots, you really need full amounts. That is why you should stay down players whom you think may annoy the person. Annoying people will eventually cause distraction. Getting sometimes connect you with having a bad mood actually run and screw the clear your mind. This is disadvantageous for anybody. So, it is advisable you transfer distinct machine is present are many noisy or irritating people surrounding you so you can find win casino slot machines SLOT ONLINE .
Playing free slots is really a great solution to get acquainted with the mission. Beginners are exposed to virtual slot machines wherein may place virtual money location the machine to play mode. The goal is basically to hit the winning combination or combinations. It really is primarily especially for practice or demo online. Today, online slots happen to be a far cry from its early ancestors: the mechanical slot machine. Whereas the mechanism of the slot machines determines that is part of of the game in the past, currently online slots are run by a program called the random number generator. Free virtual slots operate industry programs as well.
The more effective slots often located inside of the casino’s locations. Hot spots are where the hot slots are. When we say hot slots, standard essentials machines developed to be super easy to defeat. Hot slots are often located in areas such as winning claims booths. Casinos place often machines here to attract and to encourage tourists to GAME SLOT play more when they hear the happy cheers of those people lining up in the claims booth to get their pleasurable prizes once they play pai gow poker.
Fact: Wishes probably essentially the most widespread myths of all. As said earlier, no two events in gambling are identical. A machine can give two or three jackpots in a row. Can can even give no jackpot permanently. It depends in the luck.
If you hit from around the equivalent amount of money to 49% profit, then you could play again with SLOT CASINO exact same machine. Your odds of of having the jackpot are greatly high as it might be a “hot slot”. For example, if you began spinning for $100 as well as have about $100-$149 as profit, very an indication that the slot happen to be playing is one challenge that provides the best agreed payment.
The other they could give you is the chance to play at no cost for 1 hour. They will give merely specific amount of bonus credits to exercise. If you lose them inside your hour any trial has concluded. If you end up winning on the inside hour you should be able to keep your winnings but with a very specific restrictions. You will need to see the rules and regulations rigorously regarding this kind of. Each casino has its own set of rules usually.
…
Is Online Video Poker A Great Choice?
There are certain sites hits the mark is chances of winning cash or prizes with points are greater when playing their slot machine games cost. Any player can begin using these websites and have a blast.
You don’t only set your limits before the game, we should follow it. When you follow your limits, certainly you’ll go home with good profit maybe a loss can be bearable for you. So, if you have lost a number of times, then stop playing for time and be back some other time perform. If you win at casino slot machines, then stop playing lessen the reached your win reduce. Playing this will place you before the other slot players who just play like there isn’t any tomorrow until they do not have money placed.
Second, you truly o uncover the right gambling shop. Not all casinos are for everyone, to ensure that you have to research which the for SLOT CASINO your. Moreover, every casino has a fixed payout rate and it’s figure out which payout is essentially the most promising. Practically if wish to make the most big levels of money, it’s choose the casino offers the best payout rate.
Some casinos, like those involved with the Caribbean islands, rely more on seasons be successful. The Bahamas, Puerto Rico and other people completely booked from November to Spring. During this period even one of the most players are comped less because casinos will be filed with paying people no matter. In other words, require during today is so excellent a recession doesn’t matter.
SLOT ONLINE There are two types of slot cars, there may be the analog cars and brand new digital types. The traditional or analog slot cars are those that you might remember from your younger a few days. This is where it was one car per slot and the car needed to stay in that slot for the race.
WAK69 – Like those on the highest number of slot machines of various denomination between 1 cent to $100.The payouts GAME SLOT during slot machines are one of several highest compared to other casinos as east district. It has a non- smoking area too where full family appreciate the cross trainers.
The obvious minuses are: the absence of the background music. Everything you can hear during playing this online slot is the scratching (I’d call it this way) of the moving reels and the bingo-sound after you win.
…
Slot Machine Grid Betting – Casino Strategics
Set a limit for betting for yourself whether you are on online slot possibly in land gambling. If you start winning then don’t get too cloudy, frustration to lose or get addicted to it. If WAK 69 start losing don’t try it “one more time”.
If you want to SLOT CASINO try out gambling without risking too much, how about we you try going toward a of the older casinos give some free games involving their slot machines just that means you could seek playing in their establishments. Useful content ask you to fill up some information sheets, that is it. You receive to play in their slot machines for free of cost!
3Dice been recently on the receiving end of plenty of awards his or her years inside industry, including Best Customer service Team as well as USA Friendly Casino of the Year, are just a few along with prestigious awards in their trophy cabinet. Owned and operating by Gold Consulting S.A., one of the Danmar Investment Group, this casino is fully licensed and regulated by the Curacao Gaming Authority.
Tomb Raider is a 5-reel, 15 pay-line bonus feature video slot from Microgaming. It comes with wilds, scatters, a Tomb Bonus Game, 10 free spins, 35 winning combinations, and SLOT ONLINE a number one jackpot of 7,500 cash. Symbols on the reels include Lara Croft, Tiger, Gadget, Ace, King, Queen, Jack, and Ten.
Why do people particularly the free Cleopatra slots game? It probably has a lot to do with the beautiful graphics, the background music and GAME SLOT appeal of the Egyptian history that’s utilized in it. After all, harvest know who Cleopatra was? In her day, Cleopatra was the useful woman in the arena.
3) The amazing Spiderman – this is the one of men and women video slot machine games that will make the most of its film match. It has three features and End up toning provide some seriously big wins thanks to the Marvel Hero Jackpot.
Win at slot machines #1: Casinos always need their customers deeper their own casinos its no wonder that playing the loose paying slot machines at the ends of the aisles are awesome areas to play. You can find winning slot machines in these areas!
If you hit anywhere from the equivalent money to 49% profit, then will be able to play again with exact same machine. Your odds of of having the jackpot are greatly high as it might be a “hot slot”. For example, if you commenced spinning for $100 and have about $100-$149 as profit, very an indication that the slot you are playing is one challenge that has the best payout.
…
Best Pai Gow Poker To Win – Video Slot Gambling Casino Tips
Real world games present different time. However, the online games are exciting to play. You can have an important experience playing this regarding online game. You can sit at your home and enjoy this exciting games. But one thing you will miss, i actually.e. the mood and the environment of reality casino.
A system that isn’t user-friendly can take all the fun out in the game. Instead of just putting mind into winning, you become torn between winning and finding out how to run the machine. The best way to get for this problem in order to try first the free version for the games you want. This way, the moment you sign-up, you understand specifically what you’re getting according to.
Since I realized i was now spending some of my summers in Reno I decided that the smart money move were to patronize the so-called local casinos that cater on the local population rather rrn comparison to the tourist casinos on the strip. Challenges here being that the shrewd locals were receiving superior reward cards and a better total deal in comparison with SLOT ONLINE stupid tourists who patronized the strip.
Everyone has a favorite associated with slot game, but you shouldn’t have to limit yourself to just one. Try putting SLOT CASINO a few coins in the bunch of varied games in order to experiment making use of is out.
Invite buddies when you play. In order to more nice. Besides, https://linknbio.com/wak69 will be one to remind you never to spend all of your money. Once you the casino, stay positive. Mental playing and winning attracts positive energy. Enjoyable because an individual might be there to play and enjoy. Do not think merely of winning or maybe luck will elude you may.
So what’s the slot machine tip that’ll make GAME SLOT that you simply winner? Stop being carried away! Before you put your money at risk, think on which you wish to achieve, besides having fantastic. Do you want to play for a particular number of hours, or do you wish to win any certain dollar amount, or obtain both?
The Lcd display of the Mu Mu World Skill Stop Video slot offers impressive animation graphics as well as high definition. User friendly as part of your eyes to ensure you appreciate hours of fun. The refurbishing factory polishes and restores grew to become look of this machine to create you get yourself a machine the actual of superior quality. This machine likewise has a checkpoint mechanism which allows it become user safe and prevents unwanted accidents.
The more appropriate method of figuring out internet casino probability must aspect globe “edge” or house advantage, because payoff ratio links the advantage and your succeeding chances. Sticking with American online roulette, we place 2, $5.00 bets. Working the maths, ([(24/38) x $5 – (14/38) x $10] / $10, implies that the casino is suffering from a 5.26percent edge over the casino player, and that is just what online casinos live when considering.
…
Top Great To Play At Online Casinos Vs Land Based Casinos
Goodness, gracious great balls of fire! Okay, it’s not that fantastic, but it will definitely light your sack. Sorry, kind of cheesy wait, how you can you blame me when look at the Fire Drift Skill Stop Video slot. If you just for example the color red alone and played a Slot Machines For Sale in your life, this may definitely decorate your house in a heartbeat. Might seem like aside though, we get nothing but compliments on the play and entertainment an example Casino Pai gow poker offer.
What then are SLOT ONLINE benefits of roulette over slots and vice versa? To begin with, let’s focus on the hints. Both are simple and fast-paced games, but any kind of debate, slots is definitely faster and simpler than live roulette. This game is also easier comprehend than roulette, and you may only have a few rounds to seek out which patterns win and which ones lose.
-reel, 20 payline video slot according to the award-winning tv series. It was released in September, two thousand and seven. The Osbournes accepts coins from $0.01 to $0.50, as well as the maximum associated with coins that you bet per spin is 200. Finest GAME SLOT jackpot is 15,000 coins.
Upon understanding that the machine is an awesome slot, do not place big bets as of yet. You need to begin bankroll test first. You have to tips you simply should consider when conducting a bankroll verify. If the machine is giving over 50% perhaps more profit, then leave that machine and avoid playing needed. Chances are, the spin price you you it really is loss. An individual are have anything near replacing amount to 49% of your money and profits, may refine stay and play with this machine one more time. That machine is probable a good machine anyone let you hit an jackpot within the.
The Mu Mu World Skill Stop Slot Machine comes from Japan and it quite convenient to use. The basic switches are marked through the machine to make sure there is limited difficulty in making use of it. The equipment does not accept coins, however you may also use gear SLOT CASINO to practice with tokens.
The right method of figuring out internet casino probability must aspect globe “edge” or house advantage, because payoff ratio links the advantage and your succeeding scope. Sticking with American online roulette, we place 2, $5.00 trades. Working the maths, ([(24/38) x $5 – (14/38) x $10] / $10, implies how the casino encompasses a 5.26percent edge over the casino player, and the actual reason just what online casinos live for.
The advantage is where all these web based casino generate. Regardless of your chances of any victory, the advantage is precisely what will useful internet casino profitable through the years because the actual slightest modifications may possess a dramatic result on both the possibilities from a win and also the edge each given online.
…
What Should Consider About Marketing Your Enterprise
Why do people particularly free Cleopatra slots sport? It probably has a lot to do with the beautiful graphics, the song and two strategy of the Egyptian history that’s integrated into it. After all, who doesn’t know who Cleopatra ended up being? In her day, Cleopatra was the worthwhile woman in the world.
The internet is ever more advanced people’s eyesight. When this technology was coming to the world, its functions were only limited for research, marketing, and electronic correspondence. Today, the internet can SLOT CASINO now be used to play exciting games from internet casinos.
Online slot owners supply you with to ought to be necessary terminology. As it can be seen, issues are in your hands, just be braver and go ahead to winning in deals are going to casino slot games! Online slots certainly becoming major craze in today’s world. Everyone is scrambling to find the new site along with best casino games when you strike it. Online slots actually find their roots in American traditions. A man by the name of Charles Fey created the prototype kind of this game all during back in 1887 in San Francisco, California.
There might be times when you ride huge stakes and that is good. But what about those situations when you can simply do with minimal GAME SLOT choices? Should you give up playing altogether?
3) The amazing Spiderman – this is the one men or women video casino wars that makes all the most of its film match. It has three features and Enhancing your provide some seriously big wins on account of the Marvel Hero Jackpot.
https://mylink.la/wak69 comes from Japan and is then quite easy to. The basic switches are marked for that machine so there is limited SLOT ONLINE difficulty in making use of it. Handy does not accept coins, however you can even use handy to receive tokens.
Speaking of events, the Twin River RI casino is host to many events throughout every season. A 29,000 square foot event arena is often filled by some famous headline vocalists. The center hosts excellent live entertainment and does very greater than the past year. There is plenty of music and acting taking at Twin Rivers Casino site. Additionally, the facility is accessible for banquets and special attractions like weddings and business conferences.
Mainly the purpose of playing online slot games to be able to have money, but the simplest way? It’s just like you’re playing the game called Galaxy Balls. Solar panel systems need is place all identical shoes shapes or symbols in the row. An individual know am sure on easy methods to play this one, carbohydrates see a screen with a row of special significance. Sometimes, you understand this from the form of shapes, fruits or even numbers within a 2-4 spinning wheels.
…
What Is Popular In Kids Indoor Playground Games
All because of games closely follow the play of this board board game. You still land on chance and community chest, you still pass go and goes to penitentiary. Likewise you still purchase properties and place up houses and properties. What does change your various bonus games within each version of the slot games. This, I believe, precisely what keeps players coming back in time. For instance the bonus game inside Monopoly Slots Here but now slot game is known as Free Parking Jackpot Bonus. These bonus rounds have raised the game within the game that keeps slot players glued of their seats.
It possibly be the just like when you shop to the. But in the case of a casino, discover have a tally. This account will hold the funds from an individual will have to draw people play. Upkeep you win, you will receive the money in this concern. Then you can spend of the casino account depending at their rules. Some require a minimum amount to get present your account an individual decide to can slot online distance themselves. But this is usually low quantities.
Whether it’s online gambling or particular casino in Vegas, will still be important to ensure that you don’t bet what you do not have. It’s easy to reduce control when gambling, specially when you’re dropping. Not everyone have the self control to quit when their ahead or when include lost a variety of money.
If you are going to play a progressive game, be certain to play optimum number of coins capable to be entitled to the progressive-jackpot. If you are smaller amount, you will win an amazing amount, rather than the astronomical amount obtain win without the pain . progressive swimming.
In these modern times, almost all of us has regarding a technology. It is now possible to play a poke game online in the comfort of this couch. Several decades ago, who would ever feel like people could be playing a texas holdem game online one twenty-four hours?
There a variety of variants that are presently extremely also suitable for online poker players. Initial 30 days . are 5 Card Draw, 5 Card Stud, Guts Variants, Seven Stud and Anaconda alternatives. The variants of poker a wide range of and differ depending upon where are usually playing and what type of game choose. You may come across even more variants in the high stakes poker finals.
When you enter inside the casino, you’ll then immediately see slot machines located typically the entrances. Slots are very attractive as its flashy lights and welcoming sounds. Of the placed in casino entrances so that people will be enticed to get inside and play more casino board game slot.
So is going to be best to play early upon waking or inside afternoon since are the period where there isn’t that many who play bingo online. It’ll be best prevent playing through the holidays or weekends. Additionally a good practice to set how much cash you’ll wish to spend on a given day and for how long. Setting KAGURA189 fixed limit assistance prevent you losing more.
…
9 Steps To Internet And Web Business
The obvious minuses are: the lack of the vocals. Everything you can hear during playing this online slot is the scratching (I’d call it this way) of the moving reels and the bingo-sound in case you win.
Break da Bank Again: Another revised slot machine with a revamped type. Time to really crack fit on standard slots game Break da Bank. The 5x multipliers combined the new 15 free spin feature has the proportions to payout a bundle of slot coins. 3 or safer scatters trigger the free spins.
Bingo-The bingo room supplies the capacity of accommodating 3,600 people. Common bingo game is scheduled twice daily. Apart from the regular game some large sums of money GAME SLOT games like Money Machine, Money Wheel, Cars, Crazy L, and Crazy T etc might also be played. It has non- smoking sections where people with kids can take advantage of too.
It is easy start off playing and begin winning. Are often the do is search to online casino that you would want to join that involves ton of slot games that such as. After you find one, it is a two step process utilizes your own start playing and earning.
First, look on an elevated platform or carousel. The casino are going to require the higher payouts in order to visible together with most men and women. Other patrons usually tend SLOT CASINO to keep gambling after looking at a person win full-size.
So exactly what is the slot machine tip that’ll make you a winner? Stop being solo.to/wak69vip grabbing! Before you put your money at risk, think on what you would like to achieve, besides having nice. Do you want to play for a certain number of hours, or do you want to win a unique dollar amount, or obtain both?
Blackjack or 21 has become easiest casino games to explore and carry out. The idea of the game is to be a hand closer to 21 when compared to dealer. When playing Blackjack, regardless which of known as versions you could be playing, the game is between you and also the dealer regardless of what many players are with your table. Practice free, various versions of Blackjack and locate the game you like best. After you have determined your game chosen develop an approach you will utilize within a real money game. Hand calculators pocket some serious profit this game and SLOT ONLINE it is available in download and flash versions as well as Live Dealer Gambling.
Save your change in this particular 8.5 inch tall machine bank most likely be amazed at how quickly the money will accumulate. The real working handle and a coin return that could be operated manually make this a perfect idea for a present.
…
Flight Games And Parking Games – Entertainment At Its Best!
As https://oneandonlythemovie.com/ , you requires know the best time to change machines so a person need to can effectively increase your winnings. The always better change machines if your current machine produces you to shed a involving times. Shift happens, you can move towards adjacent casino wars. It is common for casinos to arrange two good slots almost each added. Observing the performance of the equipment is essential for each slot machine player. Your duration of the games, have got noticed can have used a “cold slot”, genuine effort a high possibility how the machine almost it is often a “hot slot”.
There numerous benefits in playing slots online. One, it will be less. Two, you don’t need they are yourself to the casinos and back to your house. Three, there are many great offers which purchase enjoy in many online gambling establishments. Upon signing up, new registrations may possess the to acquire freebies and sometime a first amount a person personally bankroll. Fourth, online slots are straightforward to get. Spinning merely a a few a click of the mouse all time. You can choose pay lines, adjust your bets, SLOT ONLINE and funds out using only your computer mouse.
Invite loved ones when you play. It really is more interesting. Besides, they will be ensure to remind you in order to spend all of your money. It is possible you enter into the casino, look for the positive. Mental playing and winning attracts positive energy. Have fun because happen to be there to play and take part in. Do not think merely of winning or maybe your luck will elude you.
Mu Mu World Skill Stop Slot machine can a person a great gambling experience without the hustle and bustle of your casino. You’ll be able to even let your children play inside Antique Slot machine without the fear of turning them into gamblers. Along with this machine SLOT CASINO you also quit scared of the children falling into bad company may possibly be encountered in an internet casino environment.
When you play slots, it is actually nice to utilize a lot of helpful promotions. This is because having good strategies will permit you november 23 big levels of profits. Slot machine games are entertaining games to play and are compatible with having a terrific past-time. The overall game can also be more fun when to produce how improve your chances of winning.
First, look on GAME SLOT an increased platform or carousel. The casino will want the higher payouts staying visible from most guys. Other patrons are apt to keep gambling after looking at a person win heavy.
Set a establish limit for betting for yourself whether a person on online slot or maybe in land casino. If you start winning then don’t get too cloudy, frustration to lose or get addicted with it. If you start losing do not try it “one more time”.
If you are really fond of playing slot machines, additionally you can easily nice to be able to sign up for casino memberships. This is usually free and yes it even gives you so many benefits such as freebies some other bonuses. You will even have gifts inside casino once you earn points on your membership. This can another fun way of playing competitions.
…
Free Movie Poker Tips
Get comprehend your learn the game throughout the machine, individuals very important for the fresh players. Players who are online as well as in land casinos should preserve in mind that they get amply trained with video game that may well playing onto the machines. Preserving the earth . every player’s dream to win on a slot machine.
https://www.xpertworkshop.com/ find out what in the casino. Frequently you’ll see ATM’s and funds out stations busy in numerous areas. Be certain if we are all withdrawing or cashing in slot concert tickets. If they cash in tickets, check out that area to gamble. If you play in a casino that still uses coins, listen for the sound money tinkling involving tray. Frequently higher payouts are in trafficked arenas.
You can expect to pay as low as $20 bucks, but you can easily dry replica banks will run about $80. Each the actual first is SLOT ONLINE a bit different among the others, on the other hand made to achieve the same thing: handle your change and take money from your friends. You need to treat them like arcade games in your property area.
The more effective slots occasionally located inside of the casino’s locations. Hot spots are where the slots include. When we say hot slots, including machines programmed to be very easy GAME SLOT to tune. Hot slots are often located in areas which includes winning claims booths. Casinos place often machines here to attract and to encourage website visitors to play more when they hear the happy cheers of those who suffer lining up in the claims booth to win back their prizes after they play casino wars.
Knowledge with the payback area of slot machine and influence it dons winning. While this is important because ever machine is programmed with a payback percentage in their microprocessors. This means, all of the times that the house wins are already predicted. Usually that is approximately 90 to 97 percent of time. The idea is that the higher the percentage is, the more payback you can expect. Casinos have comes around because they might encourage players to remain playing within their slot gear. So if you are a player, you need keep associated with those machines with find paybacks be sure you have a close eye on them.
In land based casinos there is a service light or candle on the surface of the slot machine. This can be activated from the player whenever they have a question, require a drink, need change or has a technical SLOT CASINO problems. In order to activate the light the player should push the change button. This particular can set there’s lots of light or candle and this will blink to have the employee’s are aware assistance should be applied. The light or candle will automatically blink if have to a victorious one. A player should never walk away a machine with a blinking light it could mean in order to a champ. If you walk away from a blinking light machine you aren’t going to be able to claim the payouts.
That is correct, you did read that right. You can now play online slots additional casino games anytime you want right on your computer. No longer do you need to wait until your vacation rolls around, or calculate some lame excuse inform the boss so available a week off to go over for your own number one brick and mortar casino.
…
Fruit Machines And One Arm Bandits – 120 Years Of Gambling History
Online Slots Strategy One: Bet Singly. Betting on a single pay line allows for you to make the most from your kitty. When gambling you always want to be aware of the amount you are spending any kind of time moment and tabs on your private limits. However, when without a doubt on single lines, you taking power over your spending and keeping everything in check.
Online slot games have grown different through your real ones. Here the player does not reach roll the dice, pick cards, numbers, and so forth. In the online version, the game slot can just put the amount which s/he is willing to stake or pick the lines or rows s/he wants to bet on, and just hit the button. And also the result decided by where the wheel stop.
While now you can play free Power Rangers game online, not every can excel with the situation. A good player is a single who can eliminate all enemies and speed using the last stage in one sitting. An individual are can’t accomplish that, you simply really point out that you are an expert in these games at this time. And it also means you actually won’t be capable of to develop a more complicated and a paid for game played on a specific console.
The associated with playing this online game is effortless. First and foremost you need to login with a dedicated cricket website. Shortly afterwards https://intour.info/ , you must select a stable group comprising of good the gamers. To be more specific, you might want to select an organization consisting of four years old bowlers, five batsmen, one wicket player and one all rounder. Now each player is assigned some points. The final results or marking are declared by the players’ show.
If playing max coins is not for you, we suggest you try an online slot by using a max bet of two coins or reduce the coin size so that max bet is value for money. With considerably of luck you can hit the jackpot!
Before you play in casinos, it is vital that you set your win and loss limits. These limits end up being set in order that you not loss more money from your bankroll. The win limit is the total amount a player is prepared to lose as an example if he shed. When this limit is met, the player should immediately cash out and stop playing. The win limits, on another hand, the sheer numbers of winnings how the player is satisfied and in order to stop playing. Take note that it is very to strictly follow these limits that allows you to maximize your bankroll for future contests.
Another involving slot machine is the multiple pay line machines. Most slot machines only give when the symbols have the center line. Multiple pay line machines make a pay out on a range of lines. These treadmills are very called nickel and penny exercise equipment. The most popular configurations include nine pay lines, but there are machines with as much as 96 pay lines. slot online Are able to play a couple line on these washers. The more coins you add the more lines which will be activated nearly the machine maximum regarding lines.
Each in the BINGO cards contain the letters B-I-N-G-O arranged on rows in your column end up being numbers. The host should call out a letter-number combination (i.e. If the host calls out N-43, look for number 43 under the letter N), and little leaguer then marks it for their sheet.
…
A Few Online Roulette Tips To Provide Started
The savings section associated with this toy machine is separate from the part used for playing. The bank will accept 98% for the coins used worldwide. May spinning reels that are wider than many other replicated casino wars. The bank is 14.5 inches tall and are a wonderful addition for any home or bar area for the conversation combined with the play it ought to provide.
It’s almost a dead giveaway here, except for that fact how the R4 DS comes in it’s own R4 DS Box. But you’ll realize that once you open the box, the contents with the SLOT CASINO box are identical to the M3 DS Simply, you’ll get related light blue colored keychain / carry case which comes with the M3 DS simply. You get everything you need, right out of brother ql-570 comes with. This includes the R4 DS slot 1 cartridge, a USB microSD Reader / writer (and this actually allows anyone to use your microSD for a USB Drive) as well as the keychain travel case and the software CD.
Casinos place good machines in these places basically because want entice more targeted traffic to play openings. It is a fact that when passersby hear the happy cheers and victorious yelling of slot winners, others will be enticed to play so they can also win at casino wars.
There’s also an interesting feature belonging to the Monopoly video slot where might gamble any winnings include by you can double them up by picking red or black from a deck SLOT ONLINE of invitations. You can also keep half your winnings purchasing want and choose to spin up the rest. You can go forward as many times as such as with this feature, the program can be worth your to to safeguard risks with small wins that could be built up into some decent affiliate marketor payouts.
First, look on an increased platform or carousel. crtlinvest.com should seek the higher payouts for you to become visible your most citizens. Other patrons be apt to keep gambling after looking at a person win full-size.
You must know which machine or site is the best for your slot machine download. Slot machine games are of several kinds nevertheless, you should ensure of which is the best for we. If you see that you are losing on a machine countless time then change gear and begin mastering the next one. Although it is a unexpected thing to do, you will discover a GAME SLOT fresh start again.
One thing to remember is this particular doesn’t possess a pull lever on the inside. It’s a more up so far version of how slot machines are played today. Have there are a handful of you who watch the old classic versions, but we this way one much larger. On the game you’ll find 7s, bells, cars with flames out the back, wilds, watermelons, and also course cherries. Definitely enough to a person busy for quite a long time ago.
…
The Best And Worst Game Perform Online Legitimate Money
Their tournament lobby is obviously jumping with action. 24/7 there is really a tournament going on for all players. Every hour, VIP players are listed a freeroll tournament to enter, likewise this goes on around the time. Special event tournaments and more are grounds for additional matches.
3Dice been recently on the receiving end of regarding awards associated with years typically the industry, including Best Support service Team as well as USA Friendly Casino among the Year, are just a few of that prestigious awards in their trophy armoire. Owned and operating by Gold Consulting S.A., the SLOT CASINO Danmar Investment Group, this casino is fully licensed and regulated by the Curacao Gaming Authority.
Knowledge within the payback amount of slot machine and any time it would wear winning. While this is important because ever machine is programmed with a payback percentage in their microprocessors. This means, all the times that the house wins are already predicted. Usually that approximately 90 to 97 percent of time. The idea is that the further the percentage is, much better payback you can expect. Casinos have this system because they might encourage players to go on playing of slot poppers. So if you are a player, require keep track of those machines with find paybacks guarantee you have a close eye on these.
It’s really too bad I missed the Hanabi Full Screen Skill Stop Slot Machine sooner, because at first I was searching for your Best Casino wars that dispersed money. Seriously, it didn’t even dawn on me that everything had switched over to those electronic tickets until about three months GAME SLOT after we started driving. Just goes display you what amount he was winning. It’s nice find out that these Antique Slot machine games give you tokens to give that old time draw in it.
Mu Mu World Skill Stop Slot machine game can a person a great gambling experience without the hustle and bustle of your casino. Might even let your children play inside Antique Slot machine without the fear of turning them into gamblers. This kind of machine completely also not be scared of one’s children falling into bad company that will be encountered in an online casino environment.
Slot cars provide great teaching tool for physical science. Get kids to explain how folks accelerate, decelerate, and defy gravitational forces as they fly on top of a high-banked curve. How come https://www.windmillcruiseamsterdam.com/ when compared to other? Merely are made to simulate real race cars so they also drift to the track SLOT ONLINE that they go through curves. Lane changing and passing are included as well features that add to the fun. Carrera slot cars could even be used for a science fair project as one example of properties of one’s energy and physical science.
Free winning casino strategy #2 – The best game perform to win at the casino is none other then chemin de fer. When you take the time a lot more about card counting strategies you will increase the chances of you winning at the casino more. Being able to predict the cards that the dealer will pull gives that you a better control of the contest.
…
Play Pokies The Simple Way – Learning Tricks From Pros
GAME MENU – Possess select this menu, when you are instantly taken to a connected with all of your game files, homebrew applications, etc. there is stored for your microSD card. You can use the controller pad on the NDS to decide the file you in order to be load. For anybody who is loading an online game for one way time, you’re prompted, after selecting the game, to evaluate that you want to create a save declare the on the internet. This is needed if you in order to be save you game. https://domaintunnus.com/ are stored on comparable thing microSD card as online game files themselves – may fantastic if you would like delete those games later, to renew other files, as are able to copy your save game files to your PC, for future use as you prepare to continue playing that game again.
In land based casinos there can be a service light or candle on surface of the slot machine game. This can be activated using the player these people have a question, want to know drink, need change or has a technical ailment. In order to activate the light the player should push the change button. Higher set over light or candle and this will blink to have the employee’s are aware assistance it takes. The light or candle will automatically blink if genuine effort . a winner. A player should never walk off from a machine with a blinking light it could mean tend to be a winner. If you walk far from a blinking light machine you is not really able to claim the profits.
Players everywhere in the world will appreciate every one of the awesome features that 3Dice offers their players, by way of the chat room, to the daily free tournaments for all of the players. Developing stop there because once you play you will get rewarded with loyalty and benefits GAME SLOT health supplement your VIP status.
Get to understand your know the game throughout the machine, this is very essential for the fresh players. The gamers who are online or possibly in land casinos should concise in mind that they get knowledgeable with the game that they SLOT CASINO playing along at the machines. Is actually always every player’s dream november 23 on a slot model.
A player just downloads the game and clicks the ‘tournament’ button each morning lobby on the online betting house. There are instructions to follow along with the player follows these. First, he registers and after that, he’ll see how long he might be to the conquer. The entrance fee costs as low as $2 to $5 in 24 hours.
You must know which machine or site is ideal for your slot machine download. Pai gow poker are of many kinds but you should make sure of the best idea for you. If you see that you are losing within the machine many time then change device and start working on the next one. Although it is unexpected thing to do, you’ll find a fresh start again.
Remember, not every machines deliver same jackpot amount undoubtedly the root-cause of SLOT ONLINE which the problem of playing in all of the machines is not the same. Greater the jackpot amount more is acquire waterborne illnesses losing the. Therefore, if you do don’t have the skills of the overall game and don’t want to lose money unnecessarily, it is better to avoid playing online that offers high jackpot amount.
The first electromechanical slot version was invented in 1954. Soon there were other versions of slot machines that have a cent rate, therefore, the amount wishing perform in the one-armed bandit is developing. Since then, both casino operators have begun to use more slots brought up, accept checks, tickets, tokens, paper, for comes about in recreation Slots become expensive. But after a bit of time thanks the casino to attract new players have appeared a cent slot gadgets. As new versions of slots allowed end up being put on line payments more coins, while it will take players would not want to afford create such large bets, it was decided that the minimum value of coins in slot machines was up one dollar.
…
Most Popular Gambling Games On Land
A player just downloads the game and clicks the ‘tournament’ button inside lobby on the online gambling establishment. There are instructions to follow as well as the player follows these. First, he registers and after that, he’ll almost certainly see the time he can be always to the frontrunner. The entrance fee costs as little as $2 to $5 each and every day.
The last mentioned they may offer you is the chance play freely available for 1 hour. They will give you with a specific volume bonus credits to use. If you lose them in your hour then your trial is finally over. If you end up winning on the inside hour then you can be able to keep your winnings but with some very specific restrictions. You’ll need to have a look at rules and regulations SLOT CASINO extremely regarding this important. Each casino has its own set of rules normally.
Playing free slots is a great approach to get no stranger to the ball game. Beginners are exposed to virtual slot machine games wherein these people place virtual money set the machine to play mode. The aim is basically to hit the winning combination or combinations. The time primarily especially for practice or demo games. Today, online slots can be far cry from its early ancestors: the mechanical slot printers. Whereas the mechanism for the slot machines determines the outcome of the sport in the past, already online slots are run by a course called the random number generator. Free virtual video poker machines operate innovative programs too.
Be likely to set reasonable goals. Supposing you’re to be able to risk $200 on simple . slot or video poker game. There should be wishful thinking to dream to turn $200 into $10,000, but you might have a realistic chance to show $200 into $250, ought to 25% gain in a very short effort. Where else can you get 25% on GAME SLOT your and enjoyable doing the following? But you must quit as soon as this goal is achieved. On the other hand hand, if you are to establish your $200 stake last for three hours, play a 25-cent or maybe 5-cent gadget. Stop at the end of the pre-set time period, whether you’re ahead or hiding behind.
zithromaxab.com is activated when 3 more Larry scatters appear anywhere on the reels. Head over to each Larry symbol to reveal up several 1000x your bet which usually $1,250, each symbol you choose will award a multiplier. I personally have hit for 1000x and 750x my bet all on same week.
There is the one other feature that isn’t available in all the slot machines of market place. You will get a sound while paying the coin in device. This will make you that SLOT ONLINE you might have a real casino.
Second, you’ll need to pick out a way to invest in your account and withdraw your income. Each online casino offers multiple approaches to accomplish this, so review everything very carefully, and choose the option you think is good for your affliction. The great thing during this step in the process, is that often the payment option you select, will almost assuredly work for ever other online casino pick the exercise to enroll with.
…
4 Free Winning Casino Tips Exposed!
Survey determine what kinds of in the casino. Frequently you’ll see ATM’s and money out stations busy in various areas. Make sure if everybody is withdrawing or cashing in slot event tickets. If they cash in tickets, pay a visit to that area to play. If you play in a casino that still uses coins, listen for your sound money tinkling involving tray. Frequently higher payouts are in trafficked arenas.
The Mu Mu World Skill Stop Slot Machine does n’t need any set. All you need is simply plug it in use is predesigned. The Mu Mu World Skill Stop Slot Machine is a second user Slot Machines that obtain from a real casino after being furbished in a factory. This mini keyboard has all these lights and sounds of the casino that lets you enjoy an e-casino like atmosphere in luxury of your home. This Slot Machines For Sale comes with warranty of two years for it’s features and options except the light bulbs.
Second, you will need to as well as other way to invest in your account and withdraw your success. Each online casino offers multiple to be able to accomplish this, so study everything very carefully, and choose the option you think is best for your state. The great thing with that step each morning process, is the the payment option you select, will almost assuredly work for ever other online casino you choose to join the program.
Fact: Wishes probably one of the most widespread myths of every single. As said earlier, no two events in gambling are involved. https://www.thingsthatdontexist.com/ can give two or three jackpots in a row. SLOT ONLINE Can can even give no jackpot permanently. It depends pertaining to your luck.
If you’re first time player of slots, it is best to observe the rules governing the first. Researching through the world wide web and asking the staff of the casino with regards to their certain rules are extra efforts you need to at least do if you would like a better and fulfilling game. In addition, try inquiring by way of the staff within the casino about any details that you will be needing with your game. The various most important matters you should be asking are details within payouts, giveaways, and extras. Do not hesitate to inquire as this is their job – to entertain and assist you as their customers.
There numerous benefits in playing slots online. One, it costs less. Two, you don’t need to drive a car yourself for the casinos and back the house. Three, there a wide range of great offers which may get enjoy practically in most online betting houses. Upon signing up, new registrations may capability to to acquire freebies and sometime the first amount anyone personally bankroll. Fourth, online slots are very simple to GAME SLOT have fun. Spinning is barely a a couple of a mouse click all period. You can come up pay lines, adjust your bets, and funds out using only your mouse button.
Knowledge among the payback portion of slot machine and impact it has on winning. While this is important because ever machine is programmed with a payback percentage in their microprocessors. This means, all the times that the house wins are already predicted. Usually that is just about 90 to 97 percent of the time. The idea is that the higher the percentage is, the more payback you are sure. Casinos have this method because they might encourage players to stick with it playing within their slot gear. So if you are a player, you’ve SLOT CASINO keep tabs on those machines with typically paybacks and assure you keep a close eye on these products.
There’s also an interesting feature for this Monopoly slot machine where down the road . gamble any winnings the by organic food that is double them up by picking red or black from a deck of charge. You can also keep half your winnings when want and judge to spin up majority. You can preserve as many times as you like with this feature, for that reason it can be worth your to to safeguard risks with small wins that can be built up into some decent pay-out odds.
…
3 Associated With Car Parking Games
The right method of figuring out internet casino probability must aspect within the “edge” or house advantage, because payoff ratio links the advantage and your succeeding possibility. Sticking with American online roulette, we place 2, $5.00 craps bets. Working the maths, ([(24/38) x $5 – (14/38) x $10] / $10, implies that the casino possess a 5.26percent edge over the casino player, and naturally just what online casinos live as.
The internet is increasingly advanced every year. When this technology was coming to the world, its functions were only limited for research, marketing, and electronic correspondence. Today, the internet can easily be used perform SLOT ONLINE exciting games from internet casinos.
The obvious minuses are: the lack of GAME SLOT the vocals. Everything you can hear during playing this online slot is the scratching (I’d call it this way) of the moving reels and the bingo-sound have got win.
So wouldso would you determine a gambling problem is ruining your life? What are from the the indicators that things are spiraling involving control, in which your a lot more truly becoming unmanageable?
Pay Dirt! is a 5-reel, 25 pay-line progressive video slot from Real Time Gaming software package program. It comes with wilds, scatters, up to 12 free spins, and 25 winning combinations. Symbols on the reels include PayDirt! Sign, Gold Nugget, Gold Mine, Bandit, Gold Pan, Lantern, and Dynamite.
A match bonus is money offered by an online casino to get you to utilize them presently there. https://buyivermectinmedication.com/ are generally larger for period depositors, but a lot of online casinos have player loyalty services. The way a match bonus works is an isolated casino will match your deposit with casino credit. If the match bonus is 100% and you deposit $100 you get $200 in casino credit score. You will then are required to play a designated regarding plays for you to can withdraw this bucks. The number is usually rather low and easily obtainable. By taking advantage analysts bonuses achievable actually a great advantage within the casino your past short rush.
It’s really too bad I missed the Hanabi Full Screen Skill Stop Slot Machine sooner, because at first I was searching for that Best Slots that dispersed money. Seriously, it didn’t even dawn on me that everything had switched over towards the electronic tickets until about three months if we started heading out. Just goes to SLOT CASINO demonstrate how much he was winning. It’s nice to understand that these Antique Slot machines give you tokens to give that old time appeal to it.
The advantage is where all these online casino generate income. Regardless of your chances of their victory, whenever you is just what will beneficial internet casino profitable over the years because even slightest modifications may have a dramatic result on the two possibilities of something like a win too edge every given golf game.
…
Try Your Luck In Popular Casino Table Games
Bingo-The bingo room offers the capacity of accommodating 3,600 people. Standard bingo game is scheduled twice each. Apart from the regular game some some huge cash games like Money Machine, Money Wheel, Cars, Crazy L, and Crazy T etc can really be played. Offers non- smoking sections where people with kids will have too.
Now, ideas secrets to win slot tournaments whether online or land set up. The first thing is find out how slot machine games work. Slots are actually operated by random number generator or RNG could be electronic. This RNG alters and determines the response to the game or effectiveness thousand times each first.
It furthermore wise decide on non-progressive slots to compete against because the progressive ones are always programmed produce more involving reels and symbols. The machine produces more reels and symbols, the associated with more wins is very slim. So, the non-progressive ones the actual machines can should desire to play combined with. aquariusballroomdance.com of the best machines are placed near coffee and snack bars. Casinos do this to motivate players to separate SLOT ONLINE their food and get to the game the soonest possible the time.
Others believe that if a product has just paid out a fairly large payout that it does not payout again for time. Who knows whether any of the SLOT CASINO strategies do work. In contrast for certain is if there is any strong indication that they do, the company will soon do these details is all can adjust that.
Progressive slot games mean that these games are associated with the other machines to the casino. Non-progressive means how the machines are not connected to one another. The implication would be that the odds may even for your progressive construct.
It is fairly easy to playing it’s essential to winning. The contraptions do is search for an online casino that you would like to join that features a ton of slot games that you like. After you find one, it would be a GAME SLOT two step process before you could start playing and winning.
Black king pulsar skill stop machine is one of several slot machines, which is widely loved among the people of different ages. This slot machine was also refurbished in the factory. Had been thoroughly tested in the factory and thereafter it was sent to stores purchase.
Once we have everyone setup with Poker chips the game commences and it usually takes about 3-4 hours for an individual to make. In the meantime, we possess a waitress who comes by and gets these Poker Players drinks, whether it be possible water, soda, or adult beverages with the bar. Yes, just particularly the casinos and some tips we all look at it is if we’re likely to lose money, we might lose it to additional instead associated with an casino.
…
One Classic Slot Machine Myth
If you pass just a little money, regardless if it isn’t progressive jackpot, edit and have your prize money. If you do cant you create the money you have set for themselves for day time meet from wearing non-standard and try again in each and every day or more than one.
Although there aren’t any exact strategies that will surely nail you the win in playing slots, here are some tips and techniques that will guide you in a person’s chances of winning. When you use this tips every time you play, you will have a way to get more GAME SLOT profits eventually.
Do not use your prize to play. To avoid JAVA189 , have your prize in check. Casinos require cash in performing. With check, you can get shut off temptation utilizing your prize up.
It’s really too bad I missed the Hanabi Full Screen Skill Stop Slot Machine sooner, because at first I was searching for the Best Slot machine games that dispersed money. Seriously, it didn’t even dawn on me that everything had switched over in order to those electronic tickets until 3 months even as we started intended. Just goes to show you how much he was winning. It’s nice understand that these Antique Slot machines give you tokens SLOT CASINO present that old time ask it.
At these casinos they will either provide help to enter a totally free mode, or give you bonus revolves. In the free mode they will furnish some free casino credits, which don’t have any cash get pleasure from. What this allows you to do is within the various games that are on the internet sites. Once you have played a online slot machine that you favor the most you possibly be comfortable on it once having to play for money.
The Lord of the Rings Slot machine game is a Pachislo Slot Machine, this means that avoid using SLOT ONLINE be that will control as soon as the reels will minimize spinning while having your turn. Treatments for acne you to infuse the standard slot machine experience by using a bit more skill! The slot machine also carries a mini game that acquired for you play between spins.
Safe Cracker – It is a great vehicle. It offers a huge jackpot with a cool 20,000 coins. And, you can bet with in the range of quarter to $5 and also the max bet is 3 coins. May get win $5000 with definitely one spin, along with 3 spins, you will get lucky just for a whopping $20,000. And, the payouts additionally offered in mid-range.
…